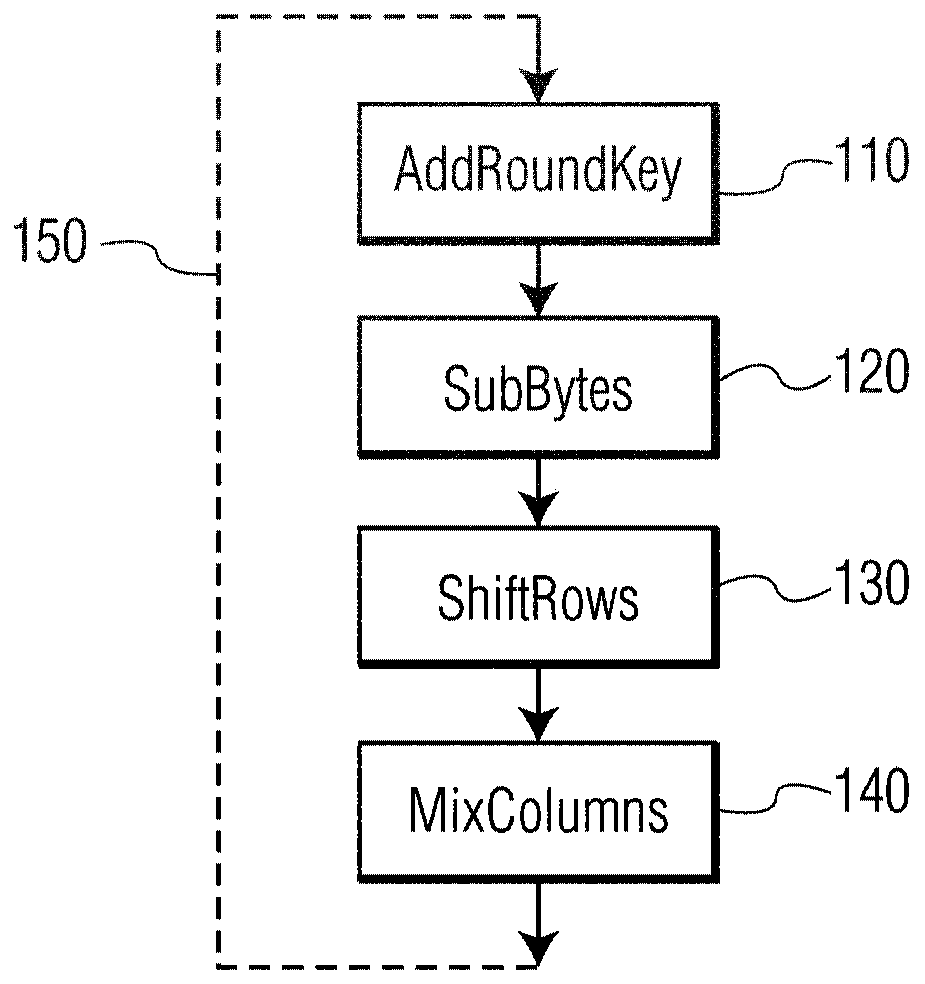
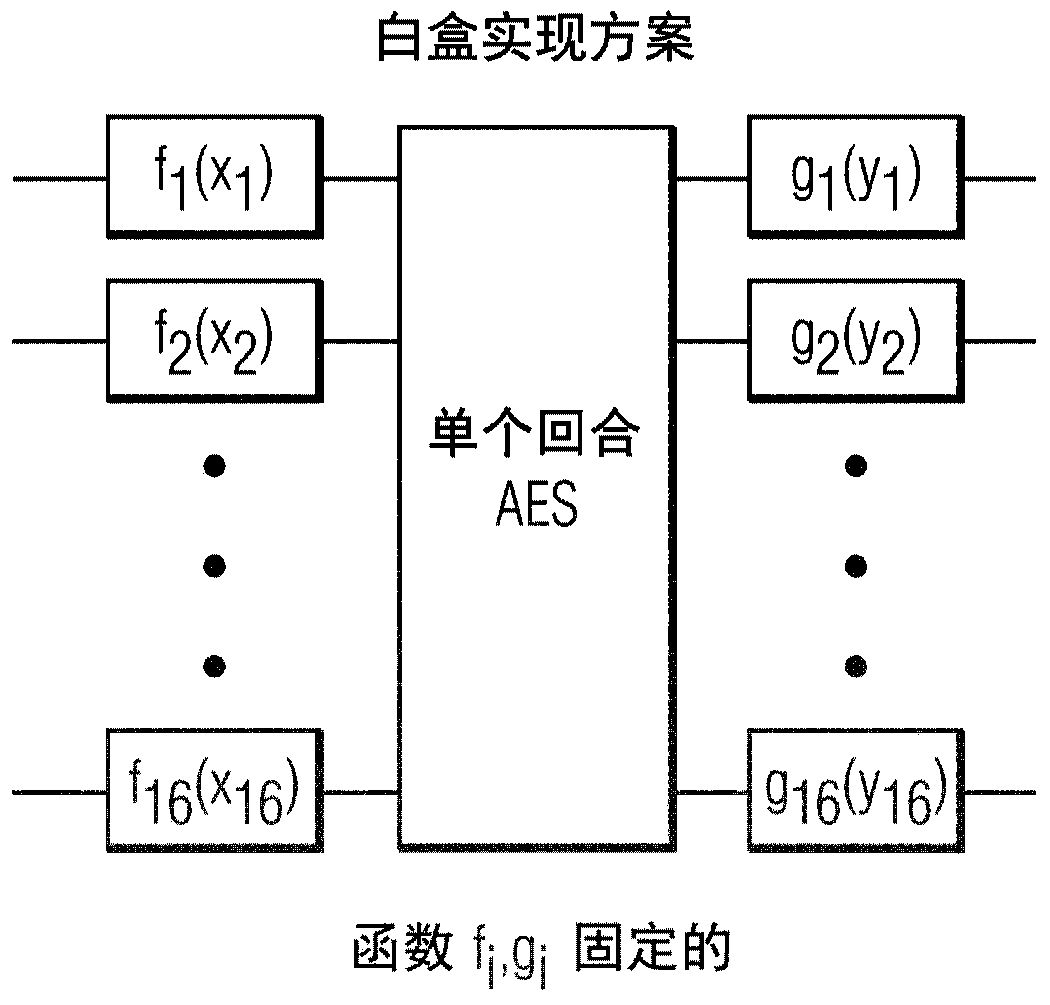
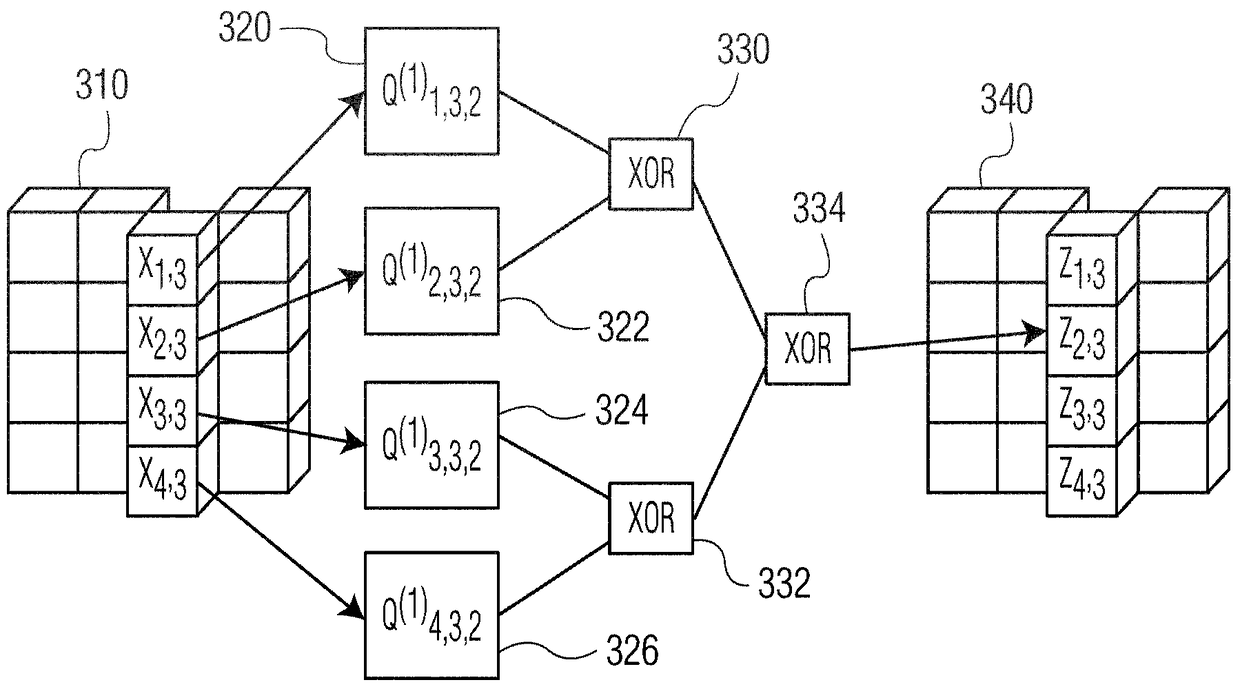
Splitting s-boxes in white-box implementations to prevent attacks
A white box, replacement box technology, applied in countermeasures against encryption mechanisms, digital transmission systems, instruments, etc., can solve problems such as difficulty in extracting information, difficulty in finding codes for access and permission control, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0058] The following description and drawings illustrate the principles of the invention. It will thus be recognized that those skilled in the art may devise various arrangements embodying the principles of the invention which, although not explicitly described or shown herein, are intended to be within the scope of the invention. In addition, all examples described herein are mainly used explicitly for teaching purposes to help readers understand the principles of the present invention and the ideas provided by the inventors to advance the prior art, and the present invention should be understood as not limited to such specifically recorded examples. Examples and conditions. Furthermore, as used herein, the term "or" means a non-exclusive or (ie, and / or) unless stated otherwise (eg, "otherwise" or "or instead"). Furthermore, the various embodiments described herein are not necessarily mutually exclusive, as some embodiments may be combined into one or more other embodiments ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com