An unmanned aerial vehicle and ground station capable of cooperating with an authentication communication mechanism and an authentication method
A technology of drones and ground stations, which is applied in the field of authentication and can solve problems such as the inability to solve the control security of multiple drones
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0121] Embodiment 1. An unmanned aerial vehicle that can cooperate with an authentication communication mechanism.
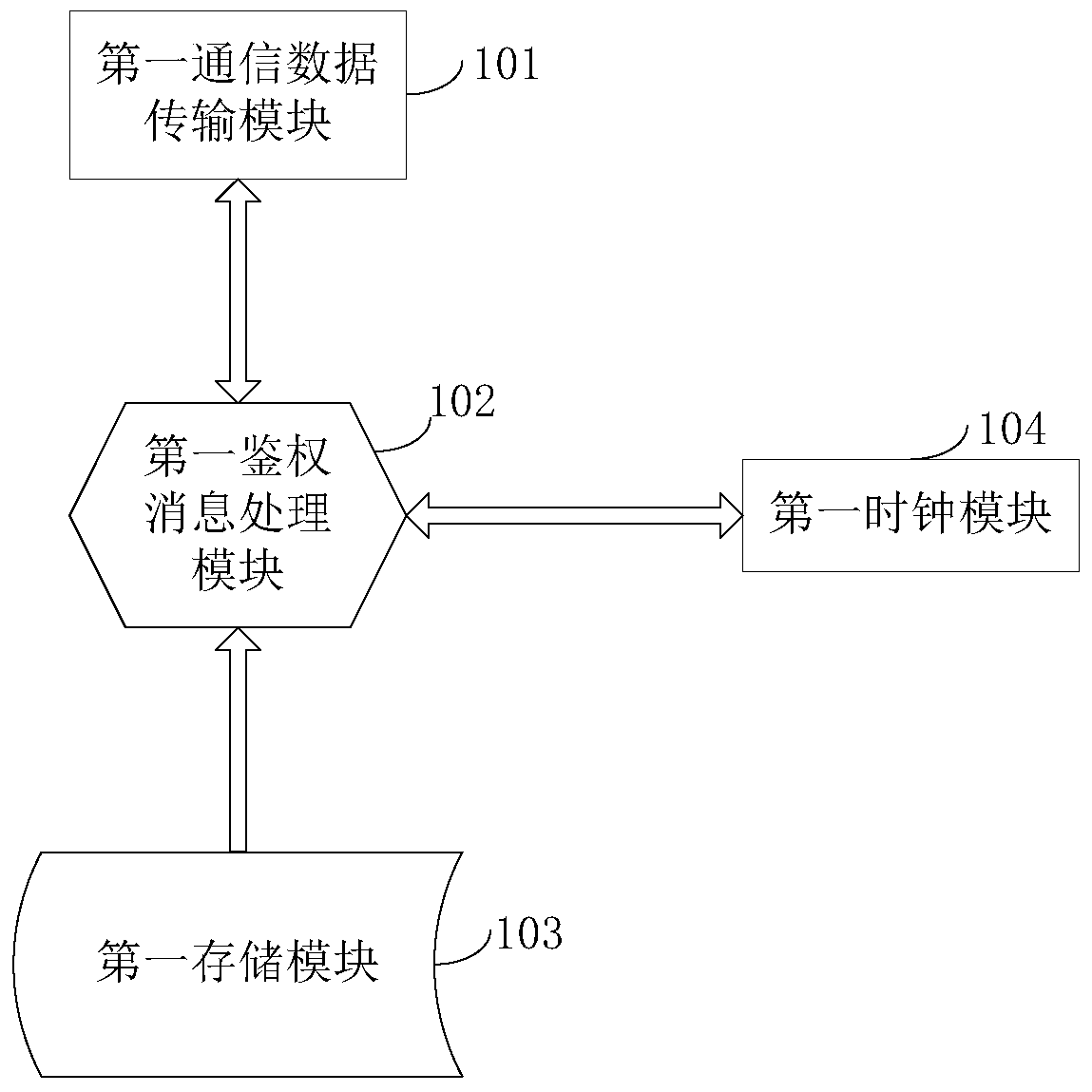
[0122] figure 1 It is a schematic diagram of the structure of the UAV that can cooperate with the authentication communication mechanism in Embodiment 1 of the present invention. The embodiment of the present invention will combine figure 1 Be specific.
[0123] Such as figure 1 As shown, the embodiment of the present invention provides a drone that can cooperate with the authentication communication mechanism, including the first communication data transmission module 101, the first authentication message processing module 102, the first storage module 103, and the first clock module 104, the first authentication message processing module 102, the first communication data transmission module 101, and the first clock module 104 can communicate bidirectionally, and the first storage module 103 is connected to the first authentication message processing module ...
Embodiment 2
[0146] Embodiment 2, a drone authentication method.
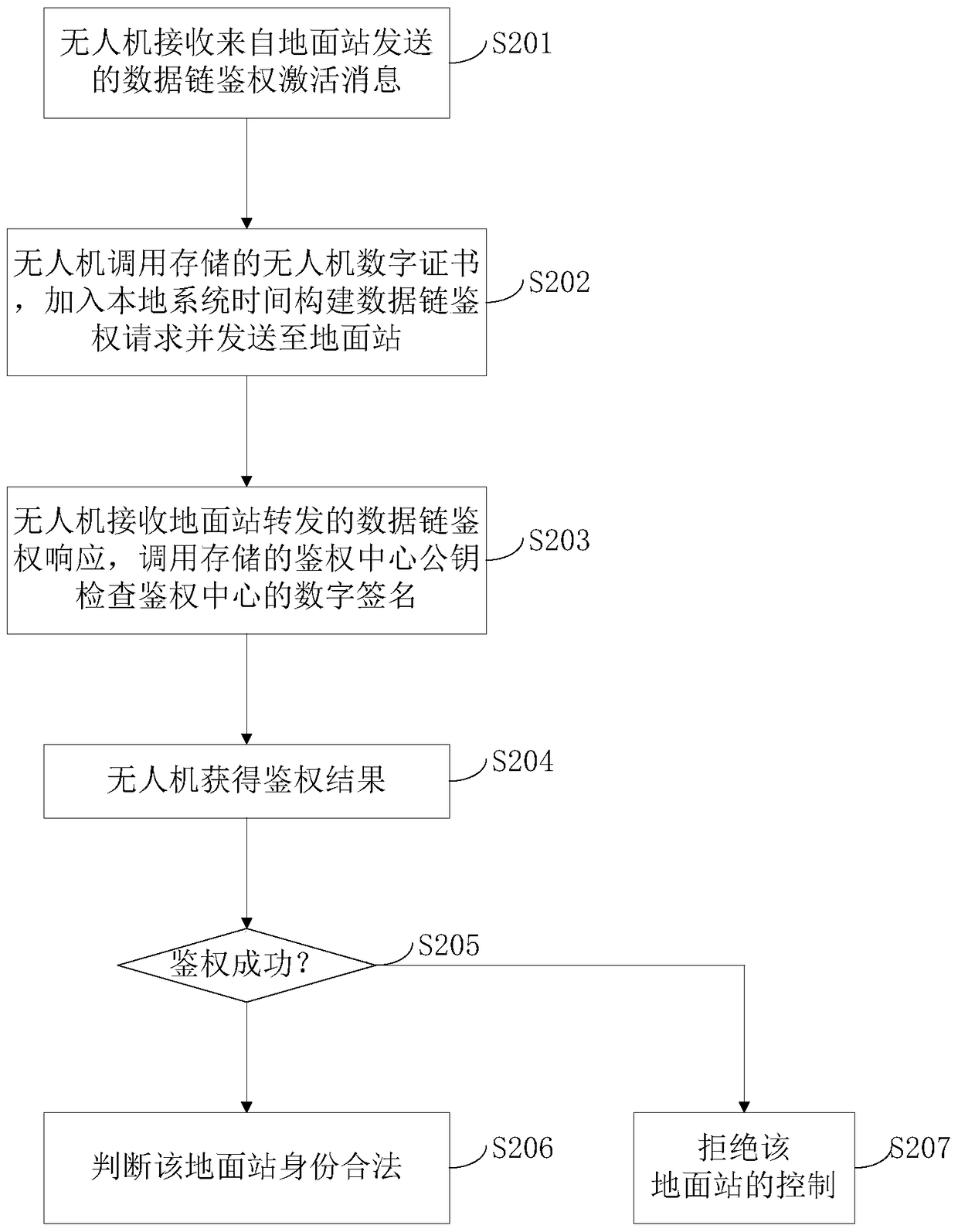
[0147] figure 2 It is a flowchart of the UAV authentication method in Embodiment 2 of the present invention, and the embodiment of the present invention will combine figure 2 Be specific.
[0148] Such as figure 2 As shown, the embodiment of the present invention provides a UAV authentication method, including the following steps:
[0149] Step S201: the UAV receives a data link authentication activation message sent from a ground station;
[0150] Step S202: The drone invokes the stored drone certificate, joins the local system time to construct a data link authentication request message and sends it to the ground station;
[0151] Step S203: The UAV receives the data link authentication response message forwarded by the ground station, wherein the data link authentication response message is issued after the ground station sends an identity authentication request message to the authentication center, The identity ...
Embodiment 3
[0177] Embodiment 3, a drone authentication method.
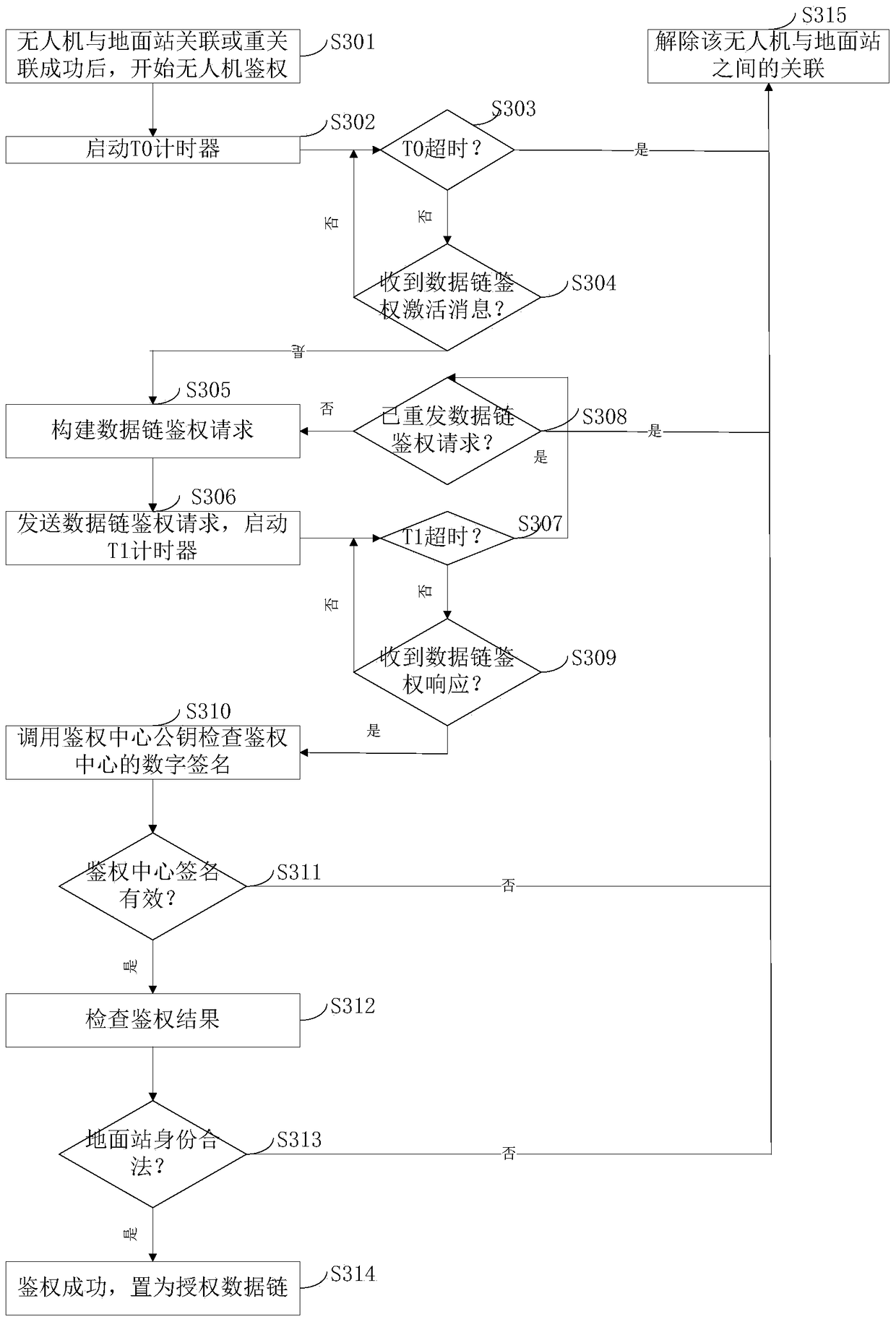
[0178] image 3 It is the flow chart of the UAV authentication method in Embodiment 3 of the present invention, and the embodiment of the present invention will combine image 3 Be specific.
[0179] Such as image 3 As shown, the embodiment of the present invention provides a UAV authentication method, including the following steps:
[0180] Step S301: After the UAV is successfully associated or re-associated with the ground station, UAV authentication is started;
[0181] Step S302: the UAV starts the T0 timer;
[0182] Step S303: Judging whether the T0 timer is overtime, if T0 is overtime, jump to step S315; otherwise, go to the next step;
[0183] Step S304: Judging whether the UAV has received the data link authentication activation message sent by the ground station, if yes, proceed to the next step; otherwise, jump back to step S303;
[0184] Step S305: The drone calls the stored drone certificate, and adds the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com