Using Ethernet ring protection switching with computer networks
A technology of Ethernet and network, applied in the field of computer network, can solve the problems of loop condition, correct work can not be controlled, invisible, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment
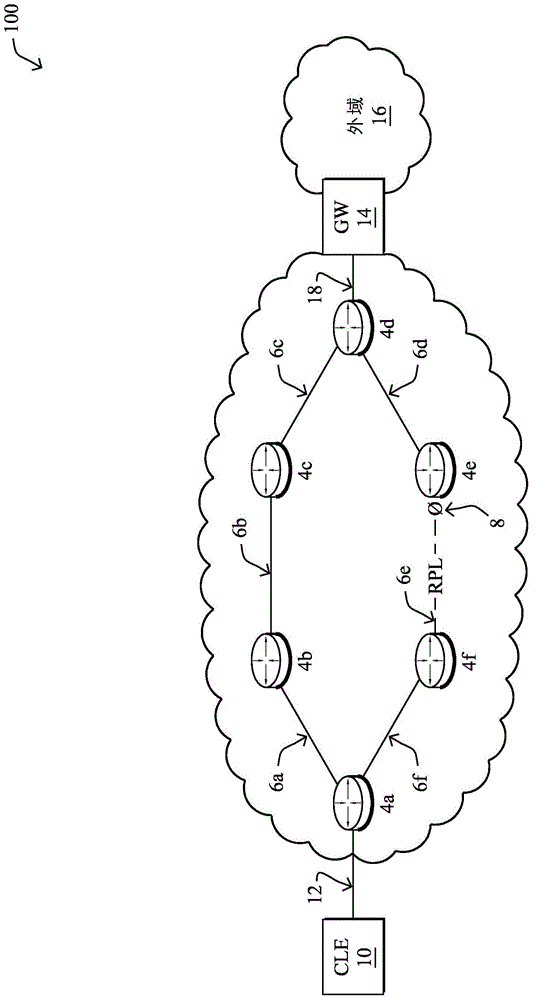
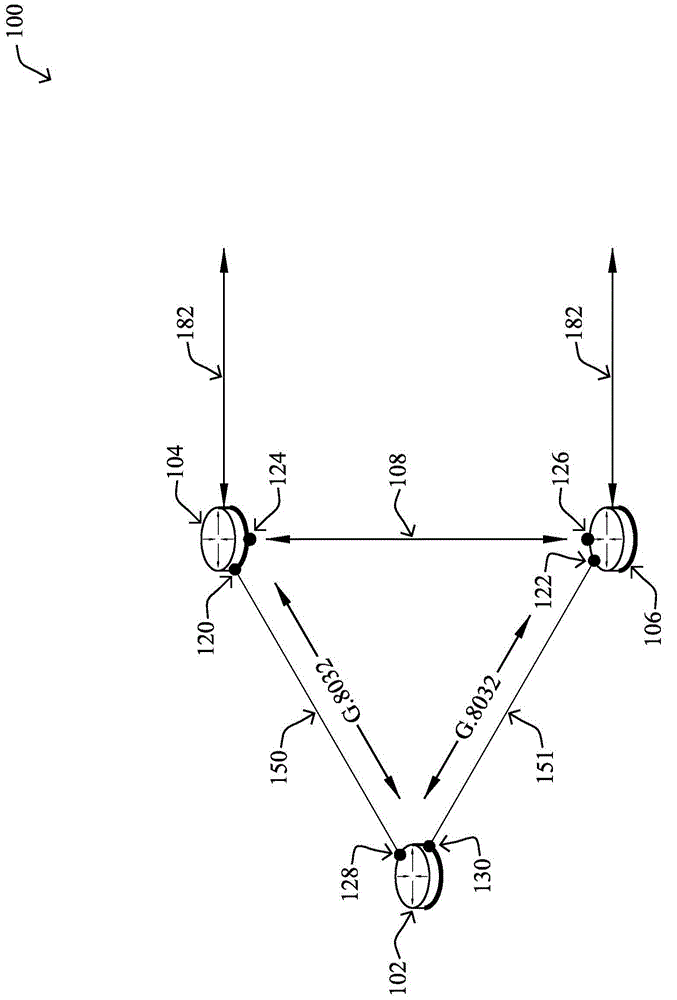
[0015] ITU-T SG15 / Q9 Recommendation G.8032 (February 2008) describes protection switching in Ethernet rings. refer to figure 1 , Ethernet ring 2 is an Ethernet network comprising nodes 4 and links 6 connected together in a closed loop topology. One of the links 6 of the ring is usually designated as a Ring Protection Link (RPL) and is disabled during normal operation of the ring by placing a channel block on that link. Typically, a communication block 8 is imposed at a node at one end of the RPL, which node may then be referred to as the RPL owner. Channel blocking 8 may, for example, include a policy that prevents packets of the ring from being forwarded through ports hosting the RPL. With such channel blocking, ring 2 is ensured loop-free, and conventional Ethernet MAC snooping and path computation can be used to compute and set appropriate forwarding information in each node of the ring.
[0016] As described in ITU-T recommendation G.8032, failure of either link 6 or n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com