A Unified Import Method of Card Encryption Data
A data and unified technology, applied in the direction of digital data protection, electronic digital data processing, other database retrieval, etc., can solve the problems of only opening, card encryption data leakage, difficult to unify format storage, etc., to improve security and realize Flexibility, the effect of reducing manual intervention factors
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0058] This embodiment provides a method for importing card-encrypted data based on a card-encrypted file provided by the same supplier. In this embodiment, corresponding identification templates are preformed and saved according to the card encryption files provided by different suppliers.
[0059] So-called recognition templates, which are used to indicate:
[0060] Where and in what form the serial number data is stored; and
[0061] The storage location and storage form of password data.
[0062] In this embodiment, a corresponding identification template is generated in advance according to the encrypted file provided by the supplier (it may be the first encrypted file provided by a new supplier).
[0063] The specific structure of the recognition template will be described in detail below.
[0064] The definition of storage location and storage form here is the same as the above explanation, and at the same time, the identification template can be used to indicate other...
Embodiment 2
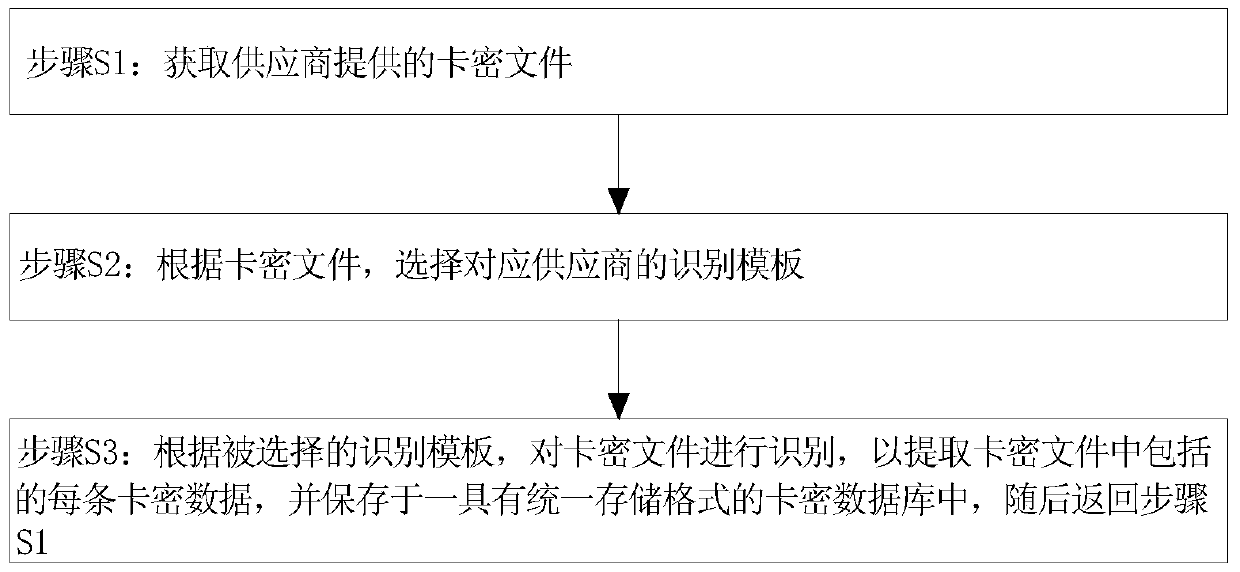
[0075] In this embodiment, the above-mentioned unified import method is as follows figure 1 shown, including:
[0076] Step S1, obtaining the encrypted file provided by the supplier;
[0077] Step S2, select the identification template corresponding to the supplier according to the encrypted file;
[0078] Step S3: Identify the encrypted file according to the selected identification template to extract each piece of encrypted data included in the encrypted file, and save it in a encrypted database with a unified storage format, and then return to step S1.
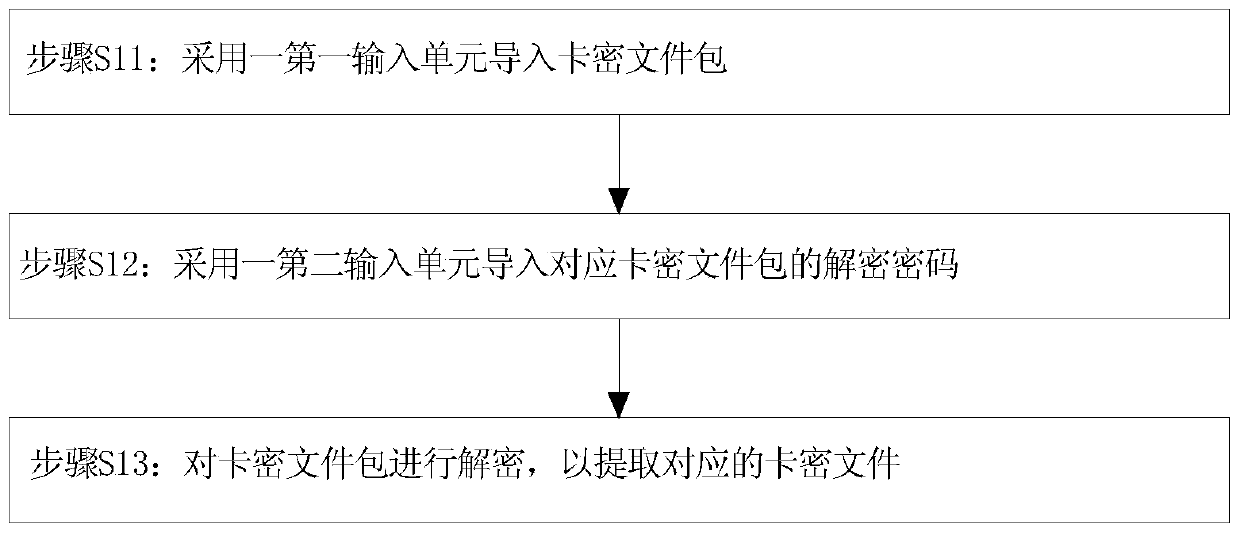
[0079] In this example, if figure 2 As shown, step S1 specifically includes:
[0080] Step S11, using a first input unit to import the card-encrypted file package;
[0081] In this embodiment, the card-encrypted file is encapsulated in an encrypted card-encrypted file package, and the first input unit has a certain authority. For example, if the first input unit is used to log in to the system, a certain input authorit...
Embodiment 3
[0089] In this example, if figure 1 As shown, the above unified import method specifically includes:
[0090] Step S1, obtaining the encrypted file provided by the supplier;
[0091] Step S2, select the identification template corresponding to the supplier according to the encrypted file;
[0092] Step S3: Identify the encrypted file according to the selected identification template to extract each piece of encrypted data included in the encrypted file, and save it in a encrypted database with a unified storage format, and then return to step S1.
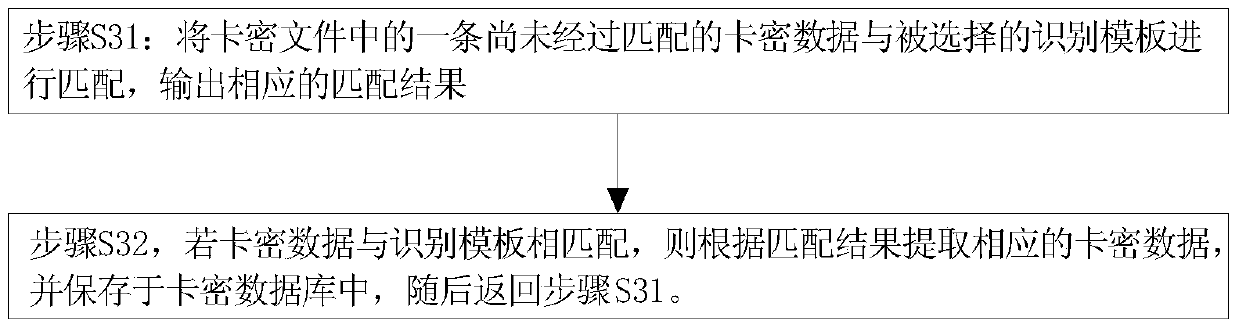
[0093] In this example, if image 3 As shown, the above step S3 specifically includes:
[0094] Step S31, matching a piece of unmatched card-encrypted data in the card-encrypted file with the selected identification template, and outputting a corresponding matching result;
[0095] In this embodiment, for a piece of card-encrypted data that has not been matched in the card-encrypted file, the selected corresponding identificatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com