LBS (location-based service) track privacy protecting method
A privacy protection and trajectory technology, applied in the field of information security, to achieve the effect of enhancing trajectory privacy security, reducing time complexity, and protecting trajectory privacy security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
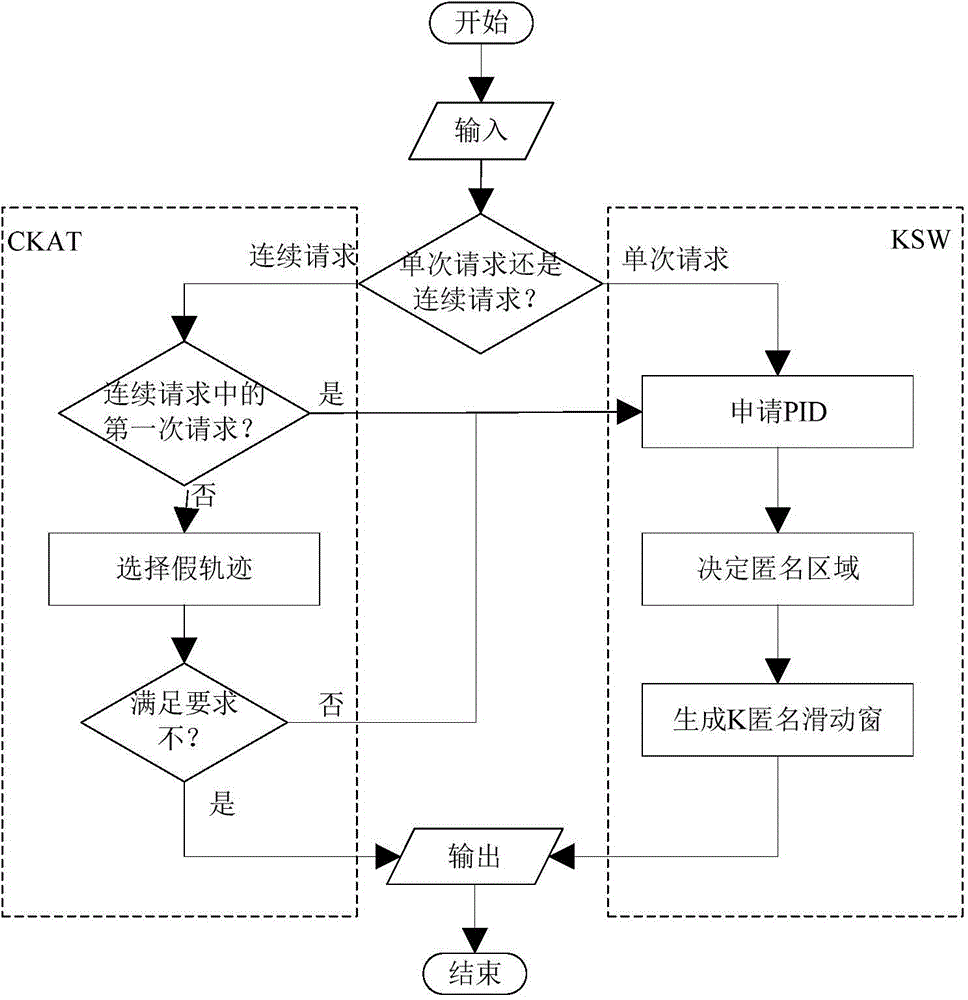
[0029] A track privacy protection method in LBS, its process is as follows figure 1 As shown, it specifically includes the following steps:
[0030] Step 1. Initialization: The user terminal input values include: privacy degree K, user's real location d 1 , the difference is the parameter flag of a single request or a continuous request, the relative time t of the request, the current anonymous area A (that is, the selection range of the false location of the current request), the anonymous threshold ε and the distance threshold s t , where ε≥0.7×K, distance threshold s t The size of is related to the user's request speed and the interval of request time, s t Refers to the maximum distance acceptable to the client when two adjacent requests of the same continuous request are submitted; the client judges whether it is a single request or a continuous request based on the input value: when flag=0, it is a single request, and flag= 1 is a continuous request; further, if it i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com