A data processing method for voice calls
A voice call and data processing technology, which is applied in the electronic field, can solve problems such as voice call security risks, reduce the possibility of being monitored, ensure safety, and improve the success rate.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
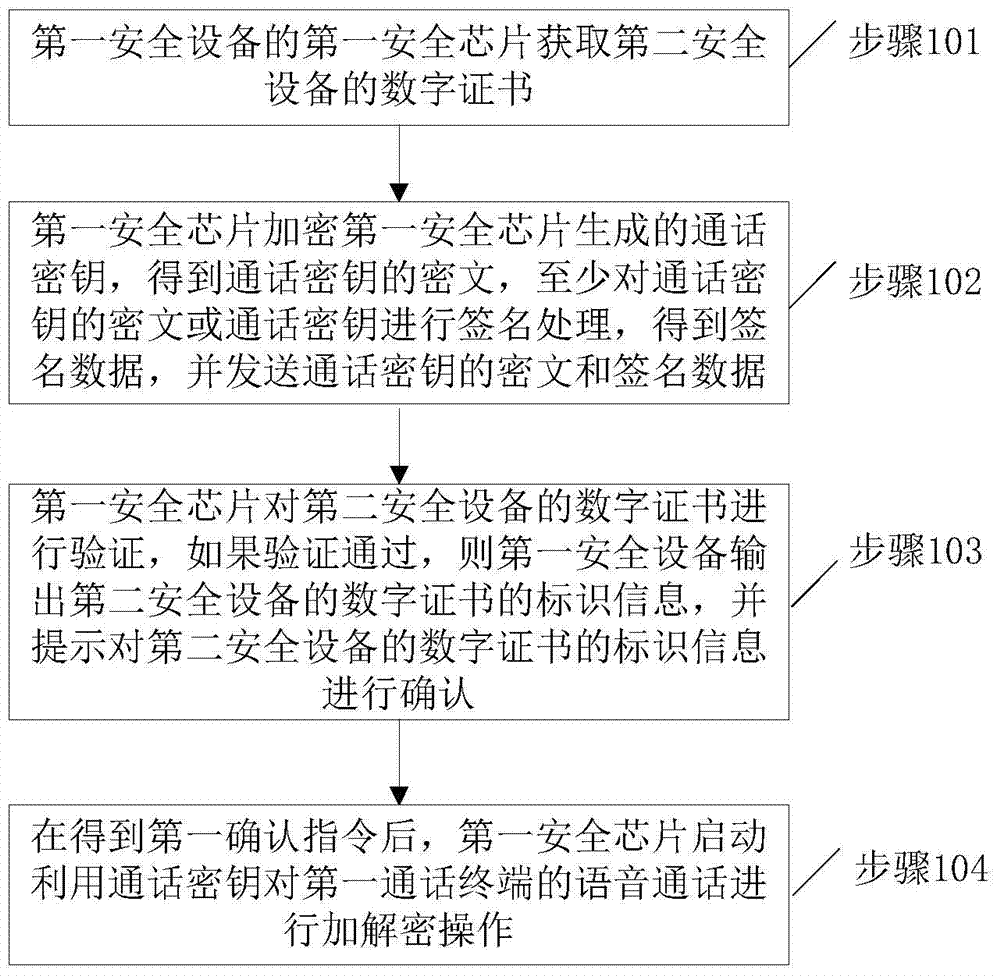
[0031] figure 1 It is a schematic flow chart of the voice call data processing method provided by Embodiment 1 of the present invention. figure 1 The methods shown include:
[0032] Step 101, the first security chip of the first security device obtains the digital certificate of the second security device, wherein the first security device is independent of the first call terminal, and the first security device is connected to the first call terminal through the first communication interface, The second security device is a security device of a second call terminal that conducts a voice call with the first call terminal;
[0033] Step 102: After the first security chip obtains the digital certificate of the second security device, the first security chip uses the public key of the second security device to encrypt the call key generated by the first security chip to obtain the ciphertext of the call key, and use The private key of the first security device at least signs the...
Embodiment 2
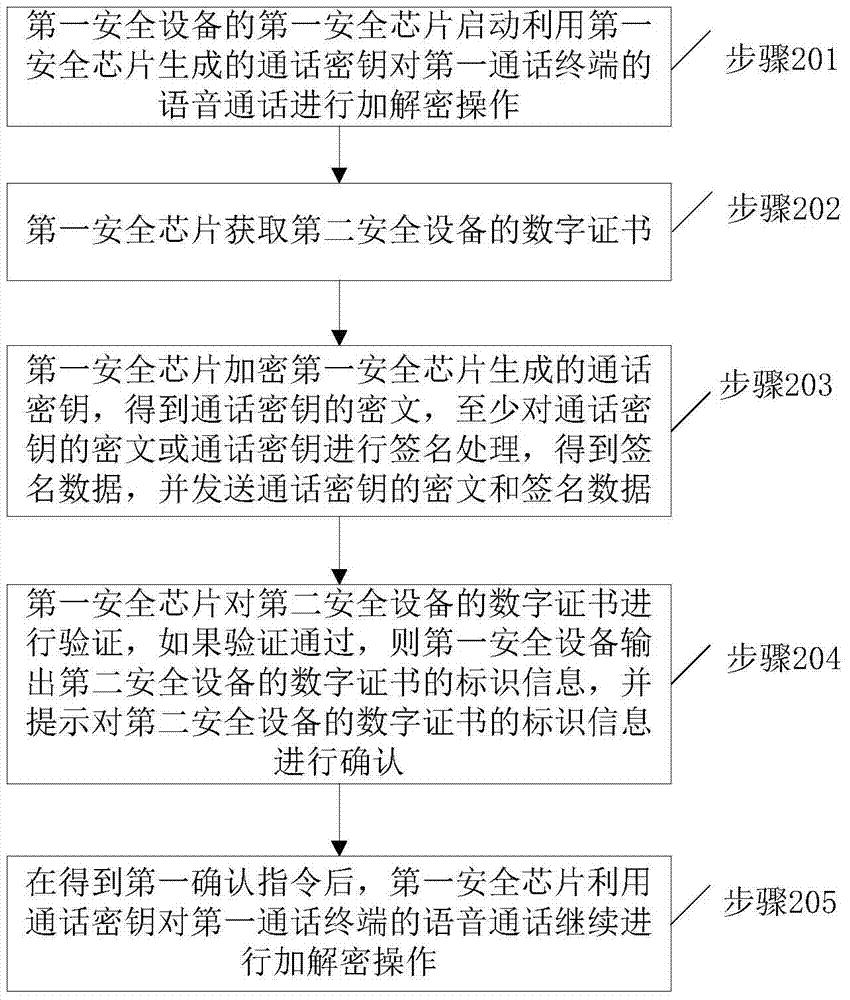
[0043] The difference between the method provided by the second embodiment of the present invention and the first embodiment above is that the receiving timing of the first confirmation instruction is different. If the encryption and decryption operation is performed on the voice call of the first call terminal, the first security chip in the second embodiment obtains the first confirmation instruction after starting the encryption and decryption operation on the voice call of the first call terminal, and uses the call key to encrypt and decrypt the voice call of the first call terminal. The call continues to perform encryption and decryption operations.
[0044] figure 2 It is a schematic flow chart of the voice call data processing method provided by Embodiment 2 of the present invention. figure 2 The methods shown include:
[0045] Step 201, the first security chip of the first security device starts to use the call key generated by the first security chip to encrypt an...
Embodiment 3
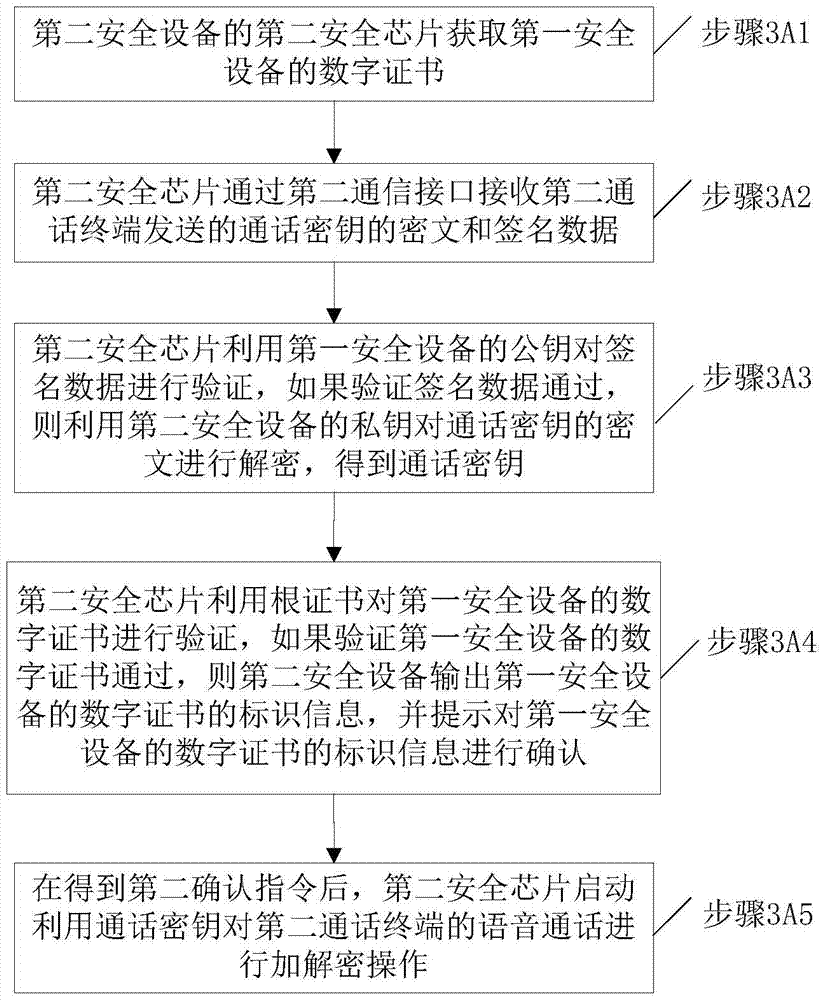
[0123]The method provided in this embodiment corresponds to the method provided in Embodiment 1, wherein Embodiment 1 is the data processing method on the side of the first security device, and this embodiment is the method on the side of the second security device corresponding to Embodiment 1 data processing method. Since the first security device can use two implementation methods when performing signature processing, that is, it can sign the ciphertext of the call key, or sign the call key to obtain signed data. Correspondingly, in this embodiment The following two data processing methods are also provided.
[0124] Figure 3A It is a schematic flow chart of the voice call data processing method provided by Embodiment 3 of the present invention. Figure 3A The methods shown include:
[0125] Step 3A1, the second security chip of the second security device obtains the digital certificate of the first security device, wherein the second security device is independent of t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com