A method and device for acquiring ipsec SA
An acquisition method and an acquisition device technology, which are applied in the field of IPSecSA acquisition and can solve the problems of consuming large system resources, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
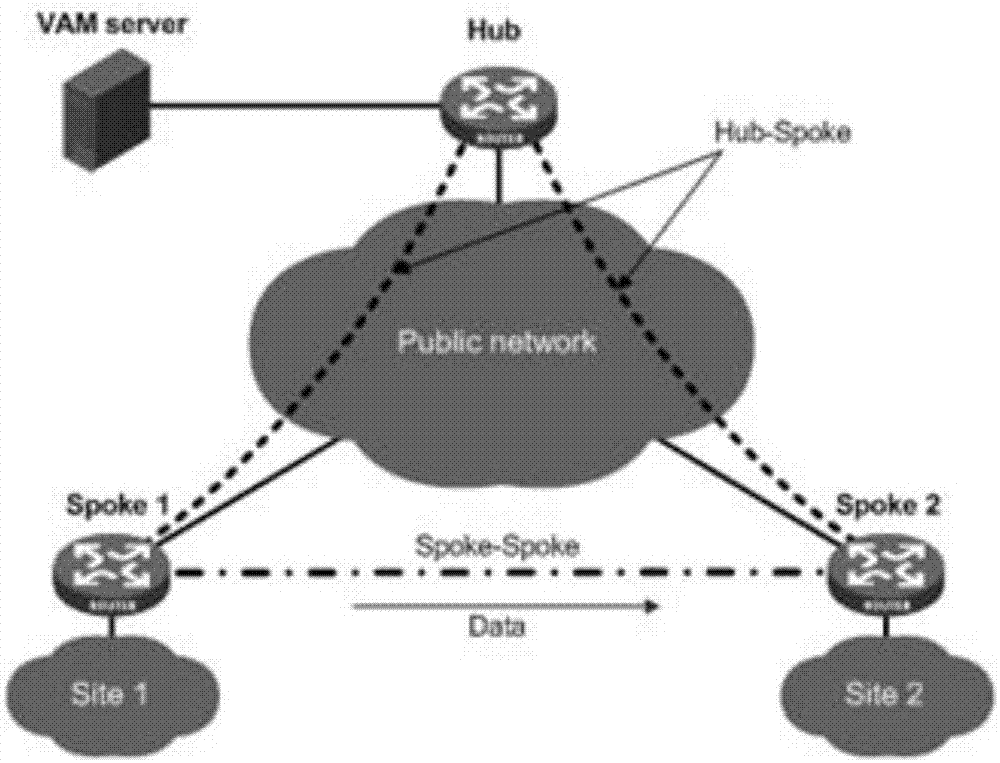
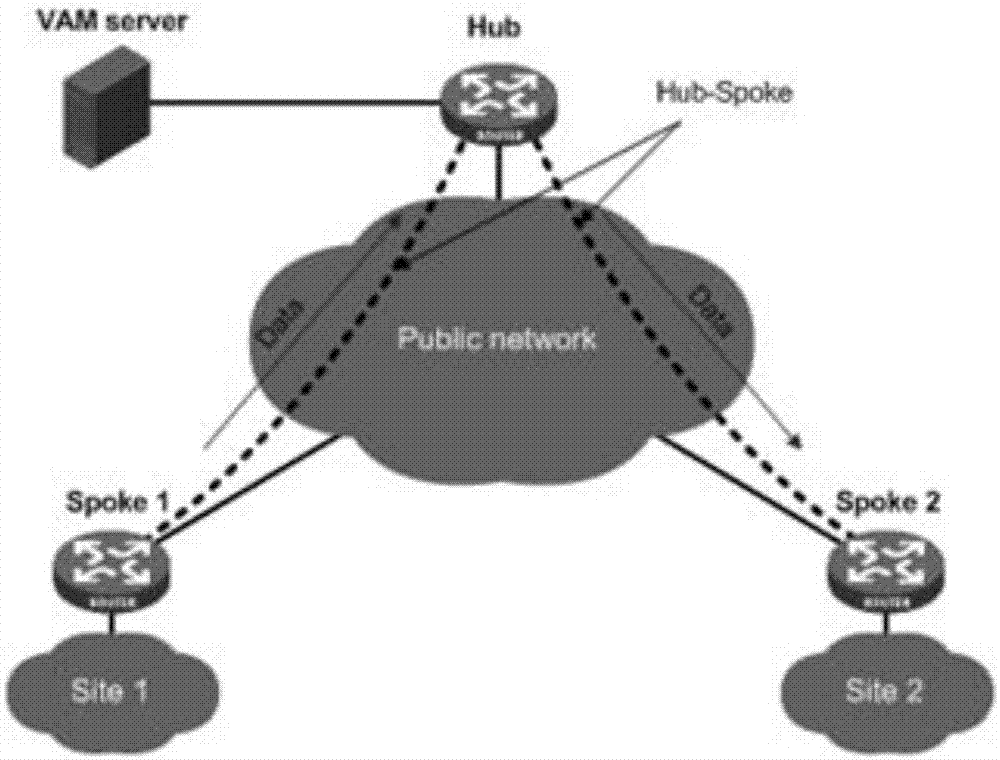
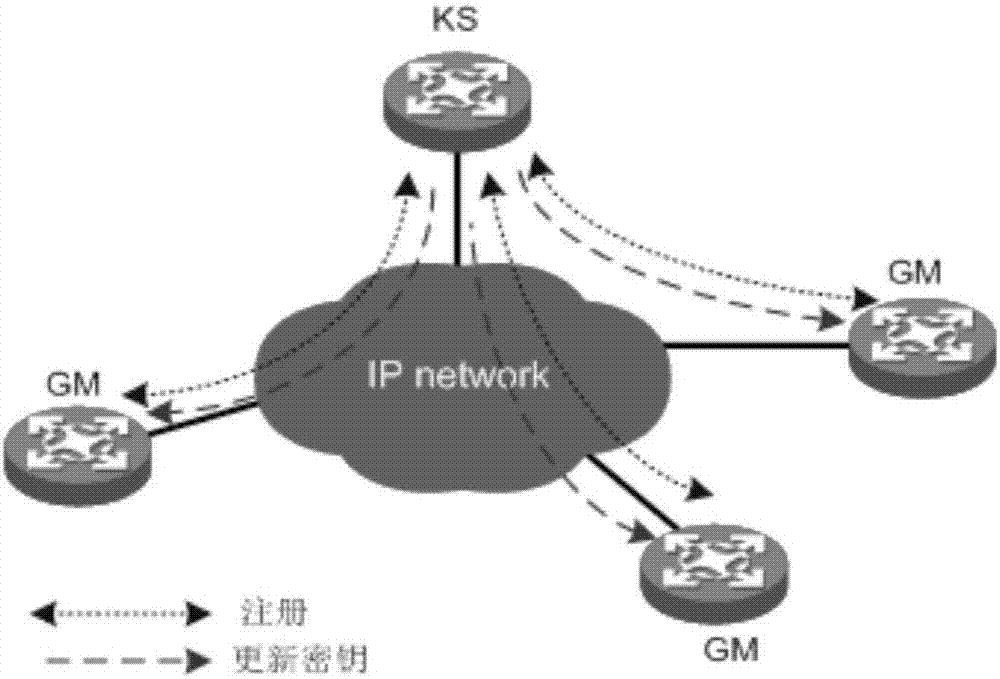
[0046] In a specific application, in order to prevent the user's private network data carried by the ADVPN network from leaking to the public network, IPSec technology can be introduced into the ADVPN network. After the introduction of IPSec technology, each node in the ADVPN network negotiates IPSec SA one-to-one, and the private network data between nodes is encrypted and transmitted after encapsulating specific headers with IPSec SA. Specifically, when each node in the ADVPN network negotiates IPSec SA, it must first ensure the security of the control packets exchanged when negotiating IPSEC SA, so the whole negotiation is divided into two stages; the first stage is to establish IKE (Internet Key Exchange, Internet key exchange) peer entities, and then negotiate IKE SA between entities; IKE SA is used to protect the second stage, that is, to protect the control messages exchanged when establishing IPSEC SA; the second stage is to The process of negotiating the IPSEC SA unde...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com