An Anti-Intrusion Identity-Based Signature Method
A technology of identity signature and identity, which is applied in the field of information security and can solve problems such as the inability to forge user signatures
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0083] The following examples are used to describe the implementation of the present invention in detail, so as to fully understand and implement the process of how to apply technical means to solve technical problems and achieve technical effects in the present invention.
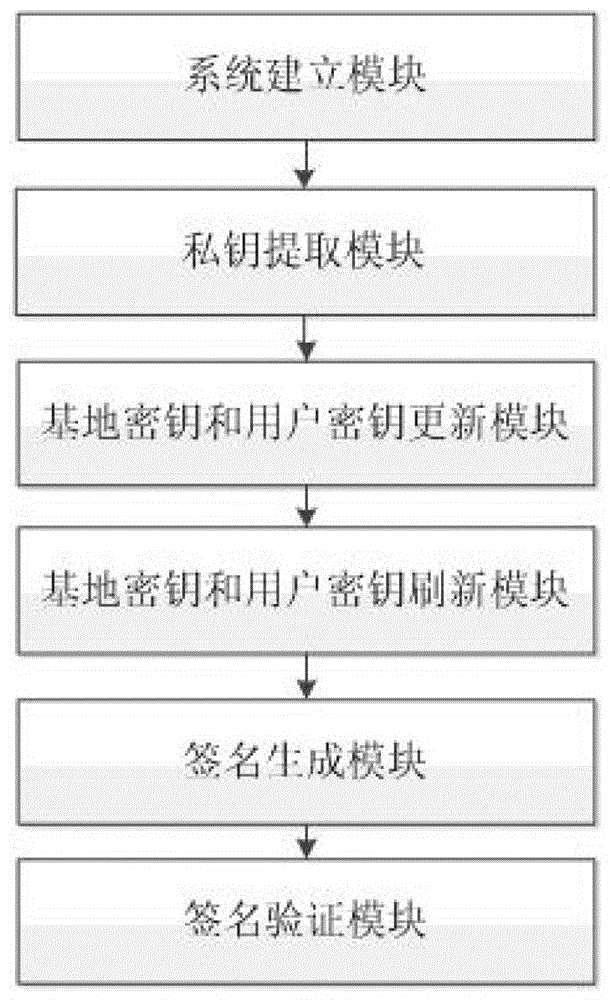
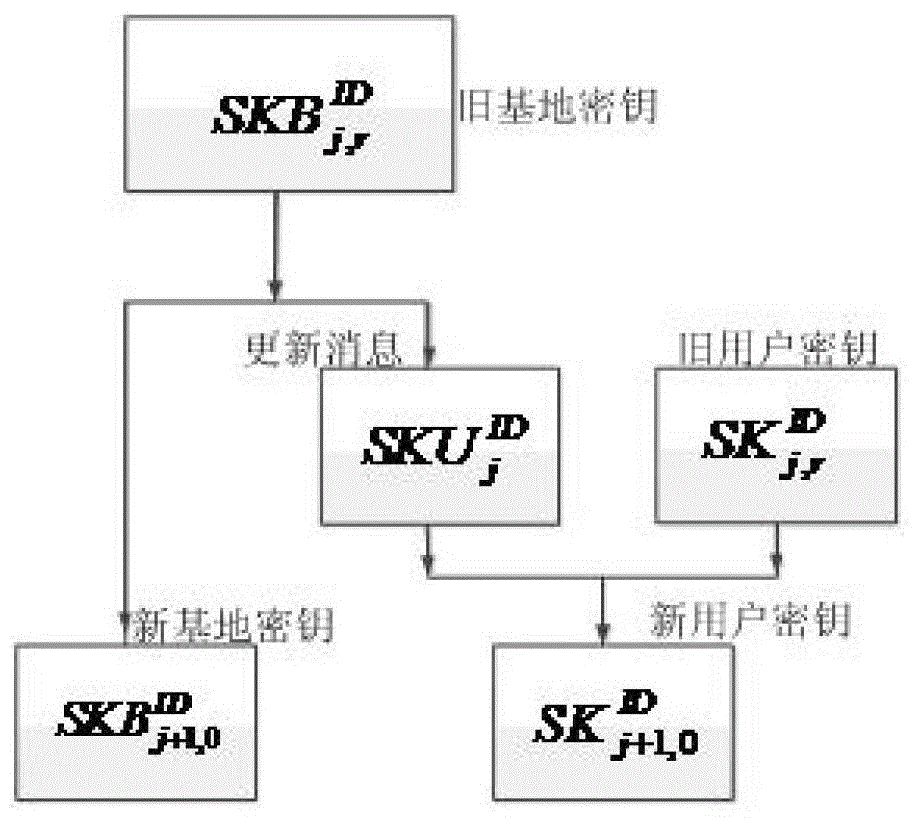
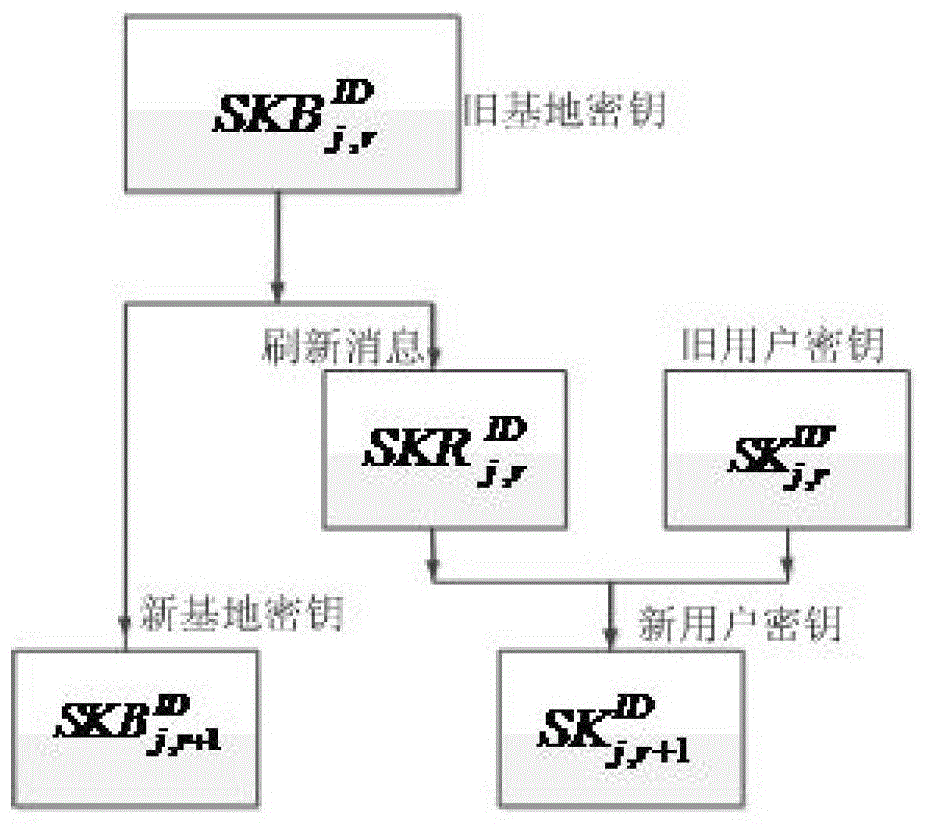
[0084] figure 1 It is a working diagram of the anti-intrusion identity-based signature method provided by the embodiment of the present invention, wherein the system building module generates the public parameters and master key required by the invention according to the input security parameters and the total number of time periods; private key extraction The module generates the initial base key and the initial user key according to the public parameters, the master key and the identity of a user; the base key and user key update module generates j+ The new key of 1 time period; The base key and the user key refresh module, according to the base and user key of the r sub-time period during the j tim...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com