A method and device for preventing readable and writable data from being copied
A technology for reading and writing data and data. It is applied in the fields of digital data protection, computer security devices, and electrical digital data processing. It can solve the problems of low security and inflexible and convenient use, and achieve the effect of high security and enhanced functions.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
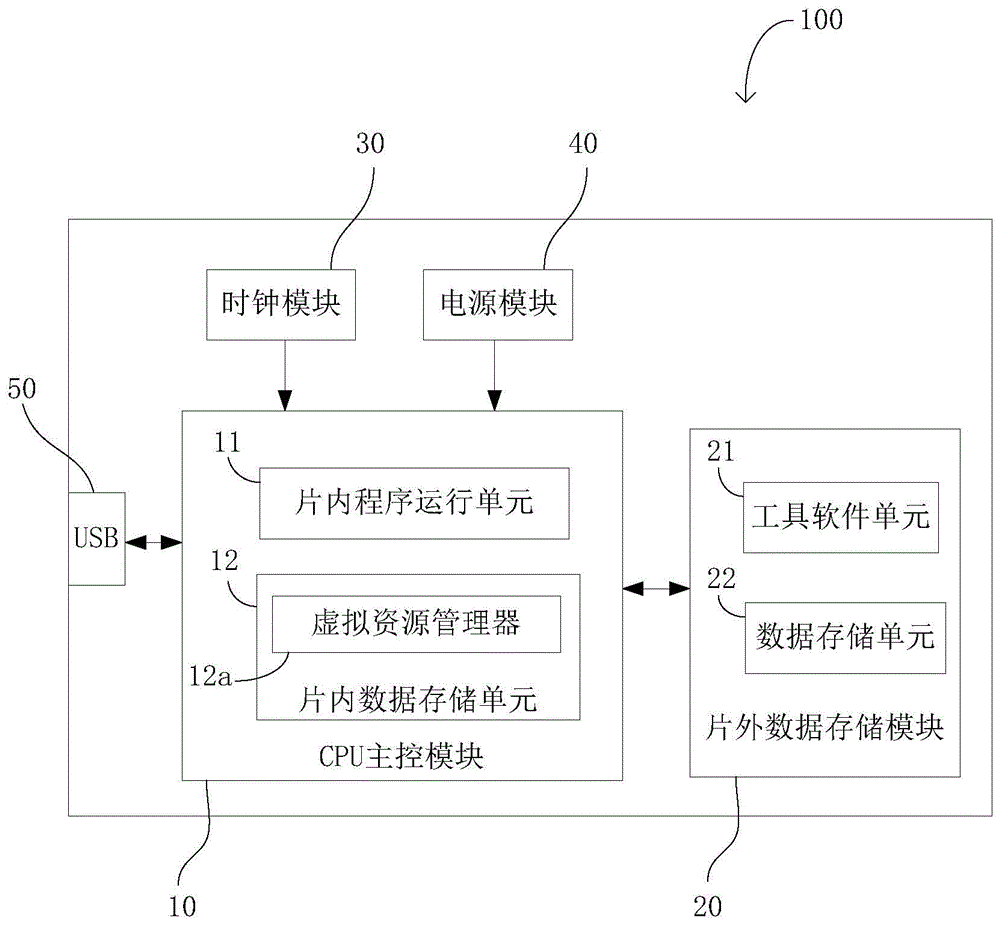
Image
Examples
Embodiment 1
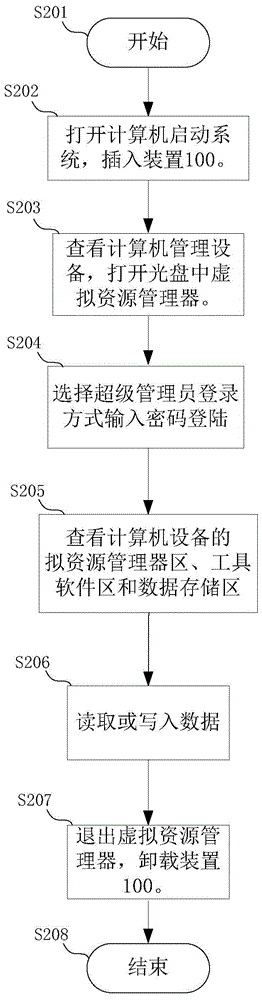
[0049] Such as figure 2 As shown, this embodiment mainly describes the common mobile storage mode.
[0050] Step S201, start.
[0051] In step S202, the computer is turned on, and the operating system of the computer runs normally, and the device 100 is inserted.
[0052] Step S203, check the computer equipment, add a virtual resource manager CD drive letter, and open the virtual resource manager in the CD.
[0053] Step S204, after the virtual resource manager 12a runs, select the super administrator login method, input the correct password, and after the virtual resource manager 12a interacts with the off-chip data storage module 20, obtain the data of the tool software unit 21 and the data storage unit 22 , and re-enumerate and load the removable storage device.
[0054] Step S205, check the computer equipment, there are three drive letters displayed in the operating system of the computer, which are virtual resource manager area, tool software area and data storage are...
Embodiment 2
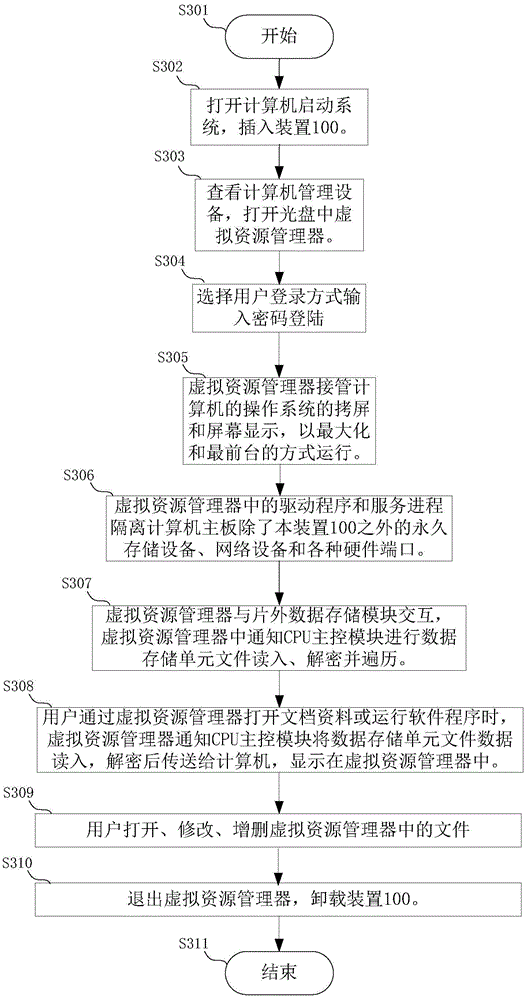
[0059] Such as image 3 As shown, this embodiment mainly records the security and anti-leakage mode.
[0060] Step S301, start.
[0061] Step S302, turn on the computer, the operating system of the computer runs normally, and insert the device 100 .
[0062] Step S303, check the computer equipment, add a disk drive letter in the virtual resource manager area, and open the virtual resource manager in the CD.
[0063] Step S304, after the virtual resource manager 12a is running, select the user login method and input the correct password.
[0064] Step S305, the virtual resource manager 12a takes over the screen copying and screen display of the operating system of the computer, and runs in a maximized and foreground mode.
[0065] Step S306, the driver and service process in the virtual resource manager 12a isolates the permanent storage device, network device and various hardware ports on the computer motherboard except the device 100, including hard disk, optical drive, ne...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com