Security event analysis method and system in cloud computing network
A cloud computing network and security event technology, applied in the field of cloud computing network-based security event analysis systems, can solve problems such as delayed attack discovery time, reduced system inspection efficiency, and reduced system inspection efficiency, so as to improve efficiency and speed up the overall The effect of matching efficiency, improving real-time and accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The present invention will be further described below in conjunction with the accompanying drawings.
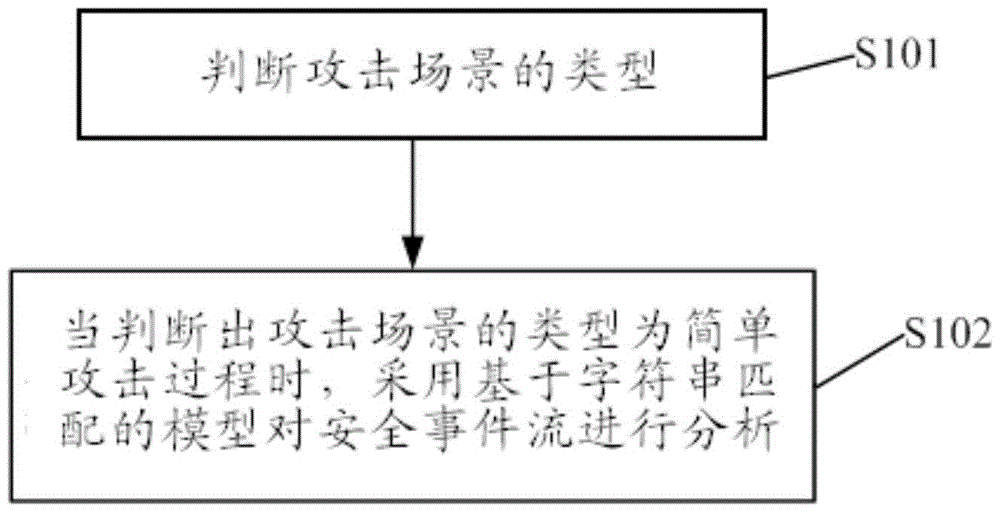
[0026] Such as figure 1 As shown, the security event analysis method in the cloud computing network of an optional embodiment of the present invention includes:
[0027] S101, judging the type of attack scenario;
[0028] S102. When it is determined that the type of the attack scenario is a simple attack process, analyze the security event flow using a character string matching-based model.
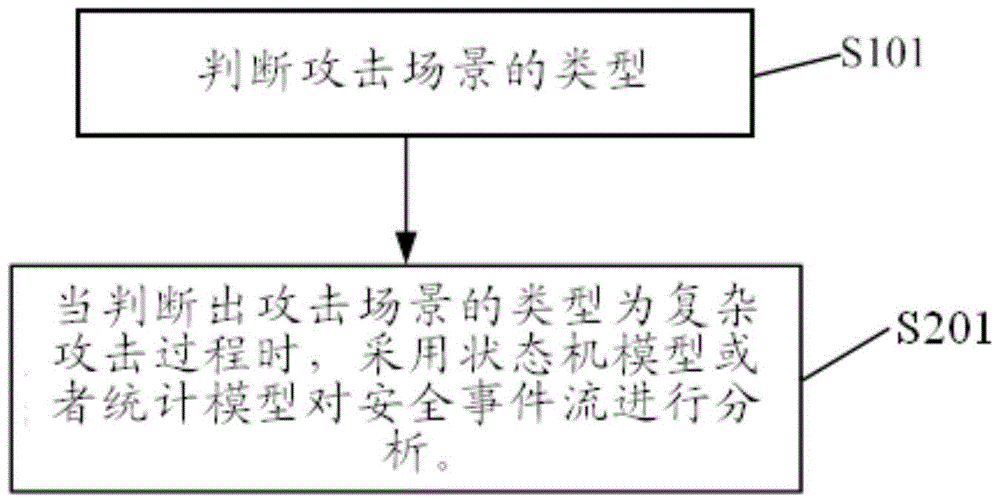
[0029] Such as figure 2 As shown, the security event analysis method in the cloud computing network of an optional embodiment of the present invention includes:
[0030] S202. When it is determined that the type of the attack scenario is a complex attack process, analyze the security event flow using a state machine model or a statistical model.
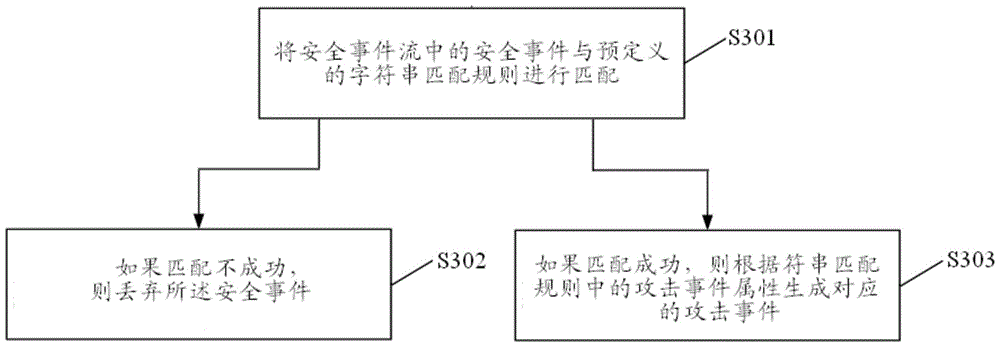
[0031] Specifically, the above attack scenario refers to a series of attack steps taken by the intruder to achieve the intrusion p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com