Method and system for configuring information delivery
A technology of information delivery and identity information, applied in the field of information management, to achieve the effect of reducing development and testing costs and improving work efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0048] Such as figure 1 As shown, it is the flow of the method for configuring information delivery described in Embodiment 1 of this application, including:
[0049]Step 101, the server searches for the configuration file information of the user according to the identity information of the logged-in user received from the client, and reads the delivery configuration authority of the user from the configuration file information.
[0050] Different information resources are provided by different information service providers, and are published and displayed through the information platforms (such as: Internet platforms, TV stations in various regions). Take the advertising information resources in the website as an example: the website receives and displays the advertising information resources provided by different advertising service providers. For different advertising service providers, there are different types of Order information, that is to say, the order information d...
Embodiment 2
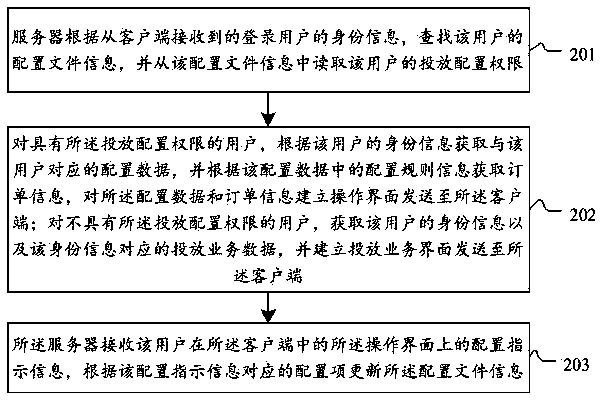
[0062] Such as figure 2 As shown, it is the flow of the method for configuring information delivery described in Embodiment 2 of the present application, including:
[0063] Step 201, the server searches for the configuration file information of the user according to the identity information of the logged-in user received from the client, and reads the delivery configuration authority of the user from the configuration file information.
[0064] In step 201, the server searches for the configuration file information of the user according to the identity information of the logged-in user received from the client, specifically: after the server receives the user login instruction sent by the client, obtains the user's identity information, The identity information searches for the user node corresponding to the identity information in the user database, and extracts the configuration file information of the user from the user node.
[0065] It should be noted that, in step 201...
Embodiment 3
[0074] Combine below Figure 3a to Figure 4b , to describe in detail the specific application of the method for configuring information delivery:
[0075] exist Figure 3a and 3b In , after the leader A of the No. 1 delivery group logs in, he can configure delivery services for the personnel in the No. 1 delivery group in the visible operation interface. specifically:
[0076] When the group leader A logs in, the server searches for the corresponding configuration file information based on the group leader A's identity information, reads the user's delivery configuration authority from the configuration file information, and learns that the group leader A has the Delivery configuration permissions.
[0077] According to the identity information of the group leader A, the corresponding configuration data including business line information, market type information and member information in the delivery group is obtained, wherein, in Figure 3a In the business line query me...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com