Security requirements query method, feedback method and device
A query method and security technology, applied in the field of communication, can solve problems such as the decline of data security, and achieve the effect of flexible selection and improved security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0065] In this embodiment, taking the CSU querying CTTP for CSPs that meet its own security requirements as an example, this embodiment of the present invention provides a method for querying security requirements, such as figure 1 shown, including:
[0066] S102: The CSU sends a security requirement query request to the CTTP, where the security requirement query request is used to instruct the CTTP to return to the CSU the CSP identifier of the CSP that meets the security requirements of the CSU;
[0067] S104: The CSU receives a response message returned by the CTTP, where the response message carries a CSP identifier;
[0068] S106: The CSU obtains the CSP identifier from the response message.
[0069] In this preferred embodiment, the CSU sends a security requirement query request to the CTTP, and the CTTP responds to the query request and returns to the CSU relevant information about CSPs that meet the security requirements of the CSU, so that the CSU can obtain potentia...
Embodiment 2
[0075] After the CSU obtains the CSP ID of the CSP that meets its security requirements returned by CTTP, or the CSU selects a CSP from the CSPs with high public recognition, it directly sends a security requirement query message to the selected CSP to confirm whether the CSP is genuine. meet the security requirements of CSP.
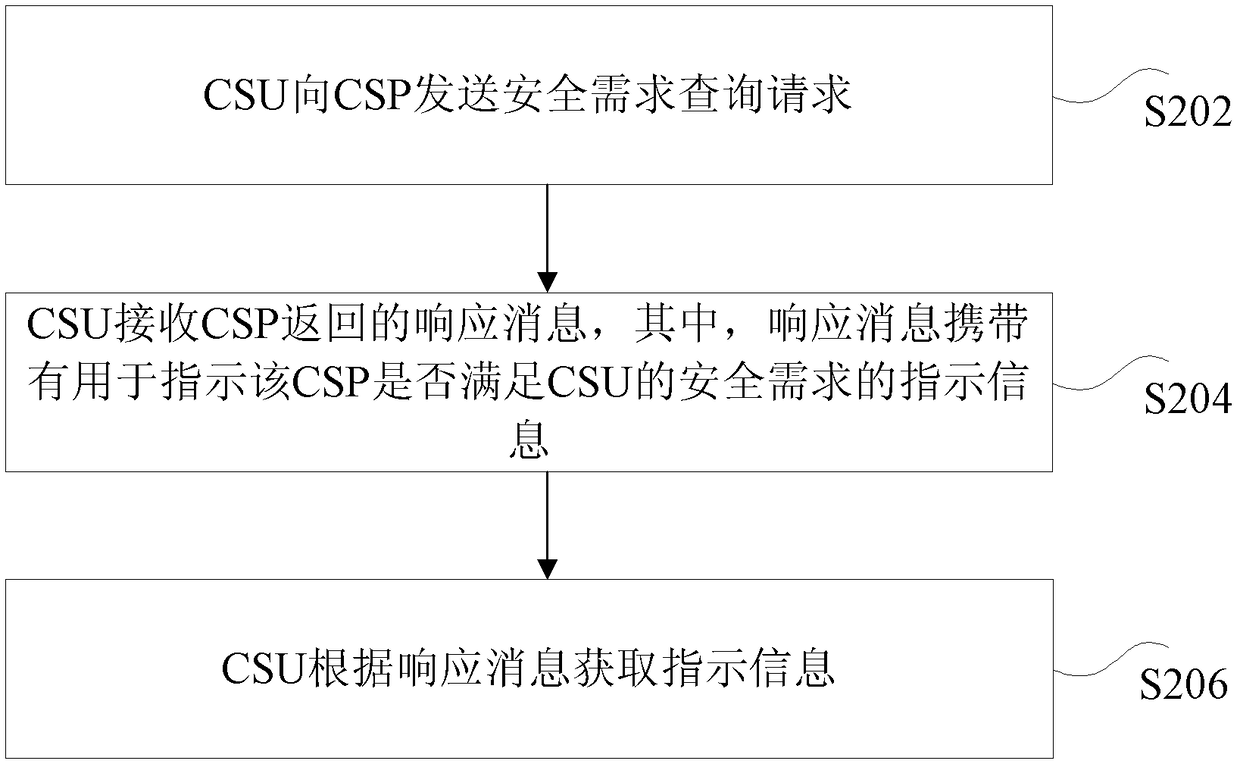
[0076] Based on the above purpose, the embodiment of the present invention provides a method for querying security requirements, such as figure 2 shown, including:
[0077] S202: The CSU sends a security requirement query request to the CSP;
[0078] S204: The CSU receives a response message returned by the CSP, wherein the response message carries indication information for indicating whether the CSP meets the security requirements of the CSU;
[0079] S206: The CSU acquires indication information according to the response message.
[0080] In the preferred embodiment described above, the CSU can directly send a security requirement query request t...
Embodiment 3
[0086] The embodiment of the present invention provides a safety requirement feedback method. In this embodiment, the CSP is used as the execution subject for description, as follows image 3 shown, including:
[0087] S302: The first CSP receives the first security requirement query request sent by the CSU;
[0088] S304: The first CSP returns a first response message to the CSU, where the first response message carries indication information for indicating whether the first CSP meets the security requirements of the CSU.
[0089] In the preferred embodiment described above, the CSU can directly send a security requirement query request to the selected CSP to confirm whether the CSP really meets the security requirements of the CSU, further ensuring that the selected CSP meets the security requirements of the CSU, and solves the problem of prior art Due to the fact that the CSU cannot quickly and correctly select the CSP that meets the security requirements, the data securit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com