A detection method for Internet of Things packet drop attack and Internet of Things tree system
A tree-shaped system and detection method technology, applied in the field of communication, can solve problems such as increasing communication overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
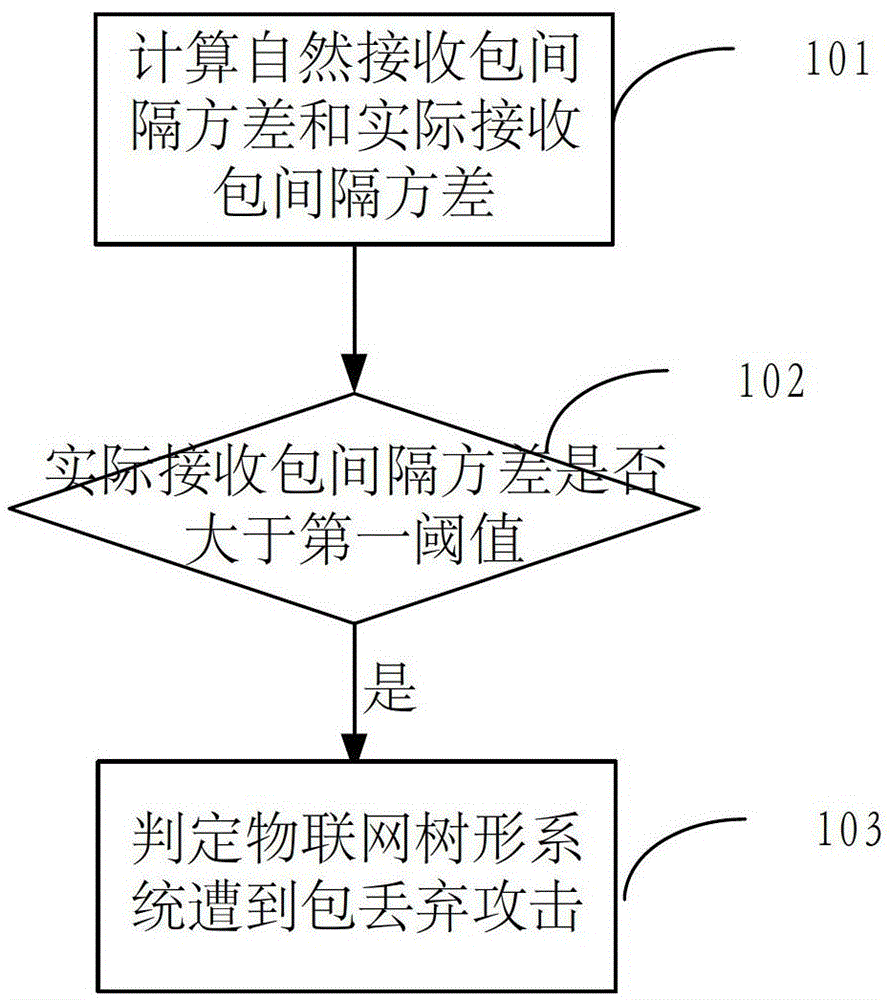
[0028] Natural packet loss rate: Defined in the normal operation of an IoT tree system, the probability of packet loss caused by the node's own capabilities, channel characteristics, information interaction methods, and the external environment rather than external or internal attacks is called natural packet loss rate. Packet loss rate. In a normal system, the default natural packet loss rate should be the default operating environment, and the packet loss rate will not affect the performance of the entire system. The natural packet loss rate in the present invention is represented by P.
[0029] In the solution of the present invention, the attacker of the packet discarding attack can obtain the communication key in the network, and can make the captured node actively select the packet sent downstream, and discard the packet with a certain probability according to the Gaussian random function. The discarding process Without distinguishing the source of the data packet, that...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com