Construction method for one-time anonymous signcryption of public key
A construction method and a one-time technology, applied in the field of information security, can solve the problems of exposing sensitive information of users, lack of traceability, and inability to determine the identity of malicious users
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0061] The technical solution of the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
[0062] 1. Description of symbols
[0063] The symbols involved in the text are shown in Table 1 below
[0064] Table 1 Symbol Description
[0065]
[0066]
[0067] Two, the embodiment
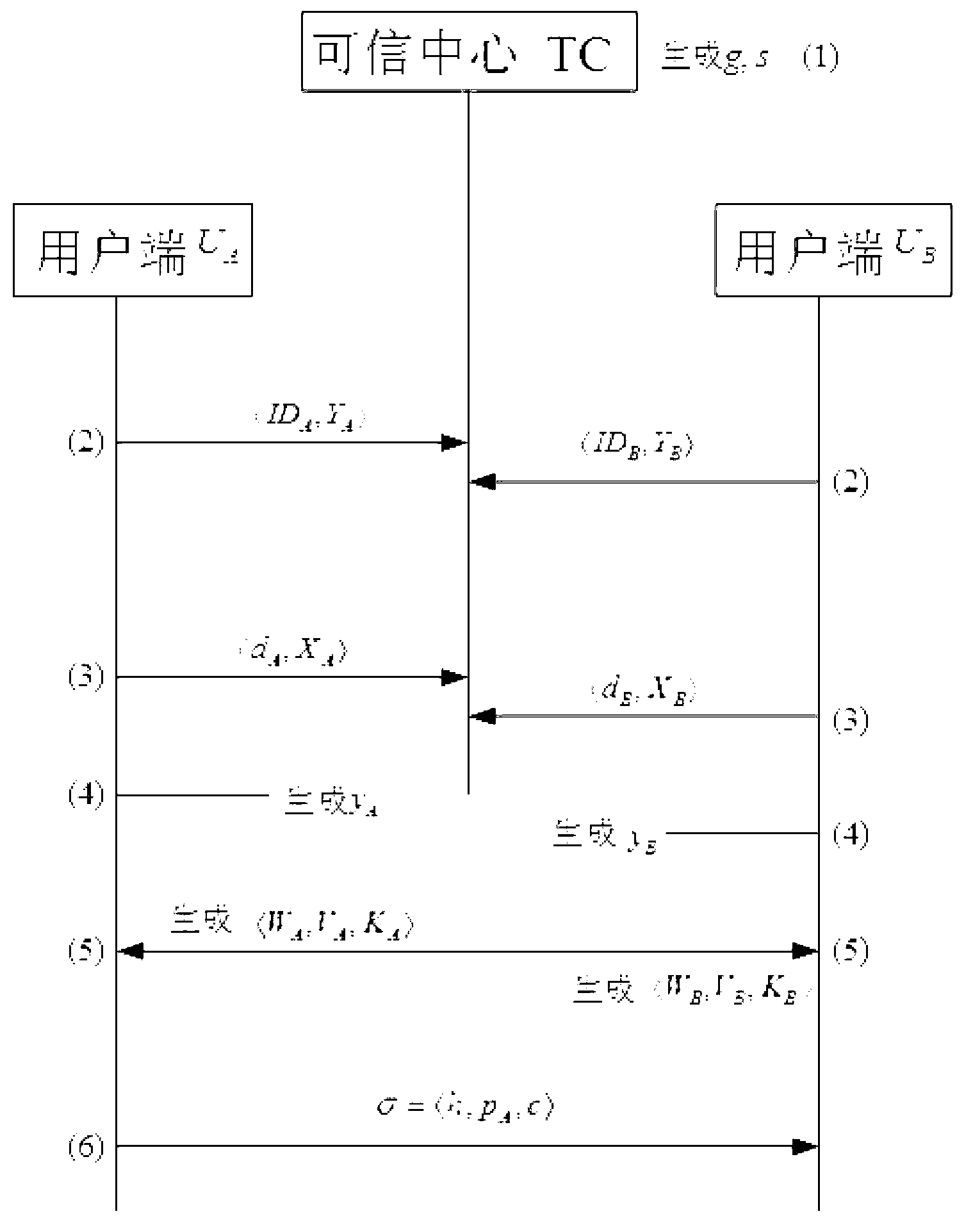
[0068] exist Figure 3 to Figure 7 Among them, for the convenience of explanation, i=A or B in the figure, that is:
[0069] Table 2 Figure 3 to Figure 7 Explanation of Chinese symbols
[0070]
[0071]
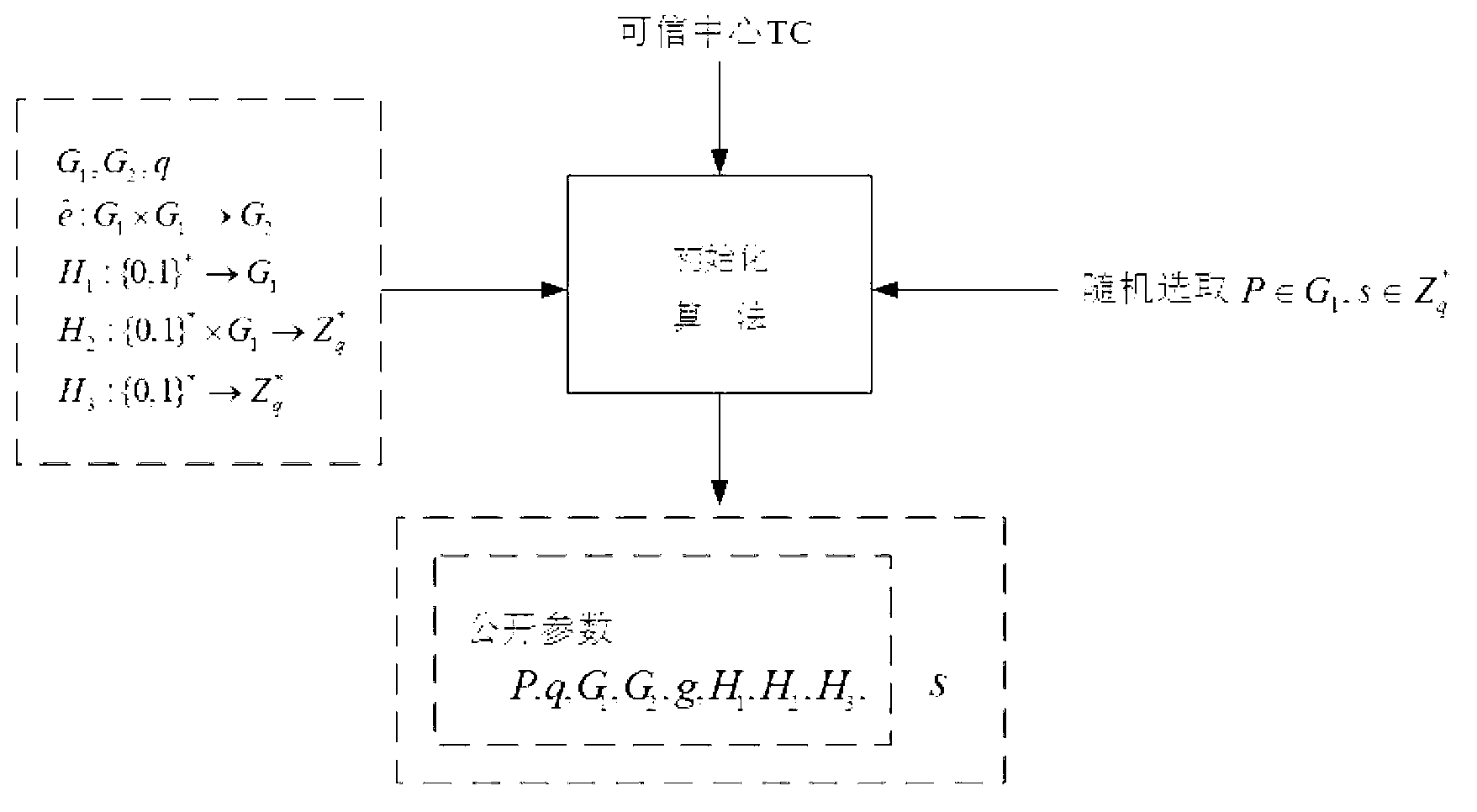
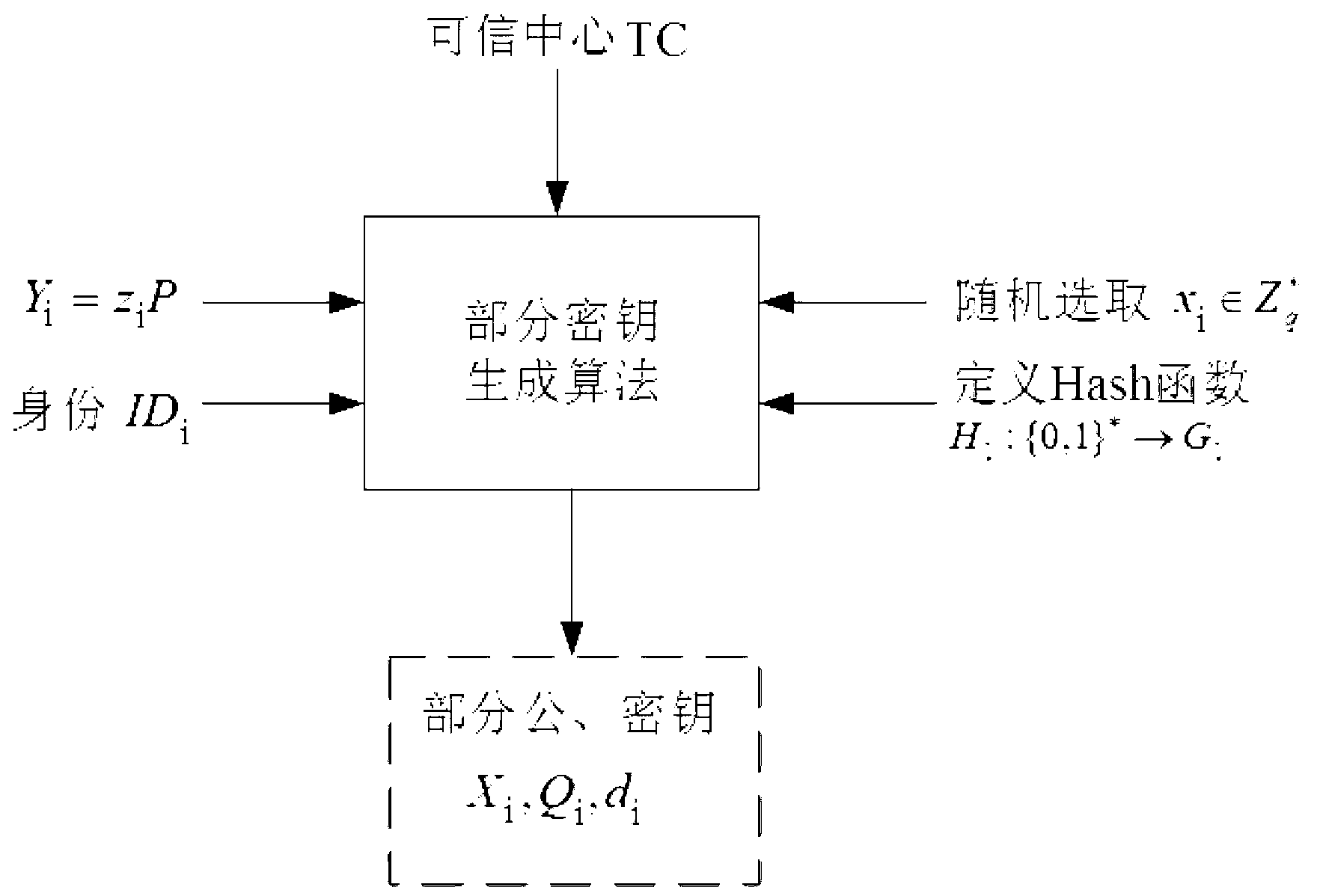
[0072] like figure 2 Shown: Let G 1 , G 2 are respectively the cyclic addition group and the cyclic multiplication group generated by P, P is a point on the elliptic curve, the elliptic curve is an algebraic curve, and the equation of the elliptic curve is: y 2 =x 3 +ax+b, where a and b are constants; the elliptic curve has no singularity, no sharp point or self-intersection. G 1 , G 2 The discrete...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com