Dynamic integrity protection method based on credible chip
An integrity measurement and chip technology, applied in the field of information security, which can solve problems such as service failure and security mechanism failure.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
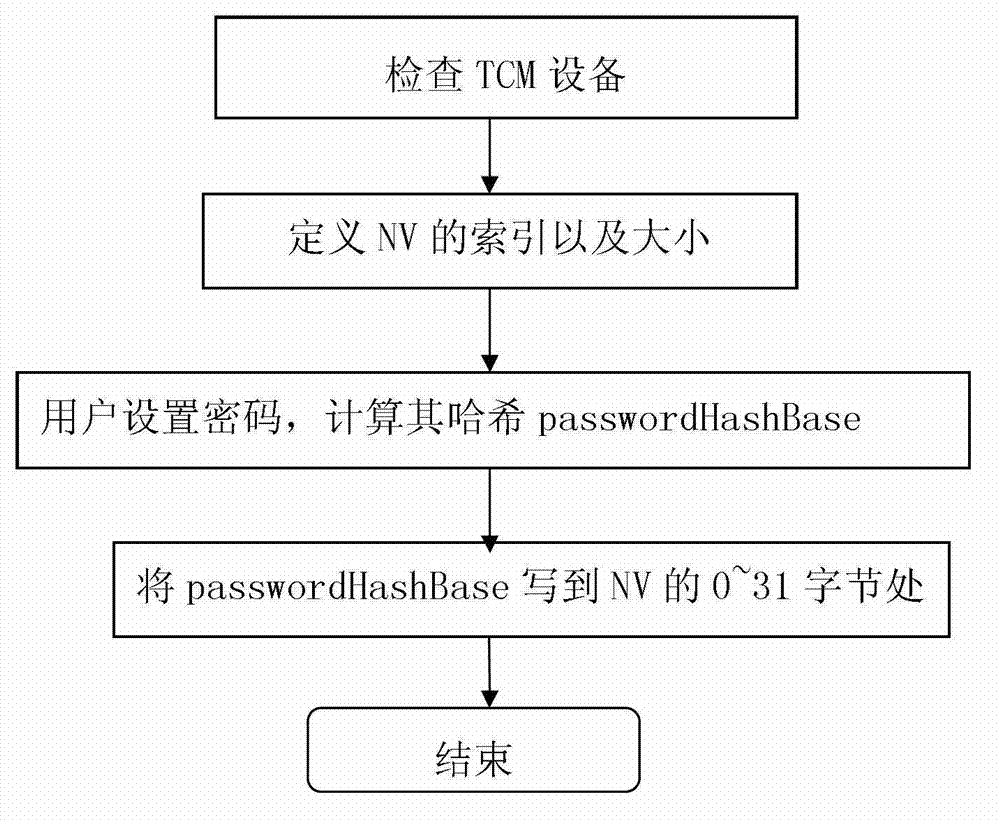
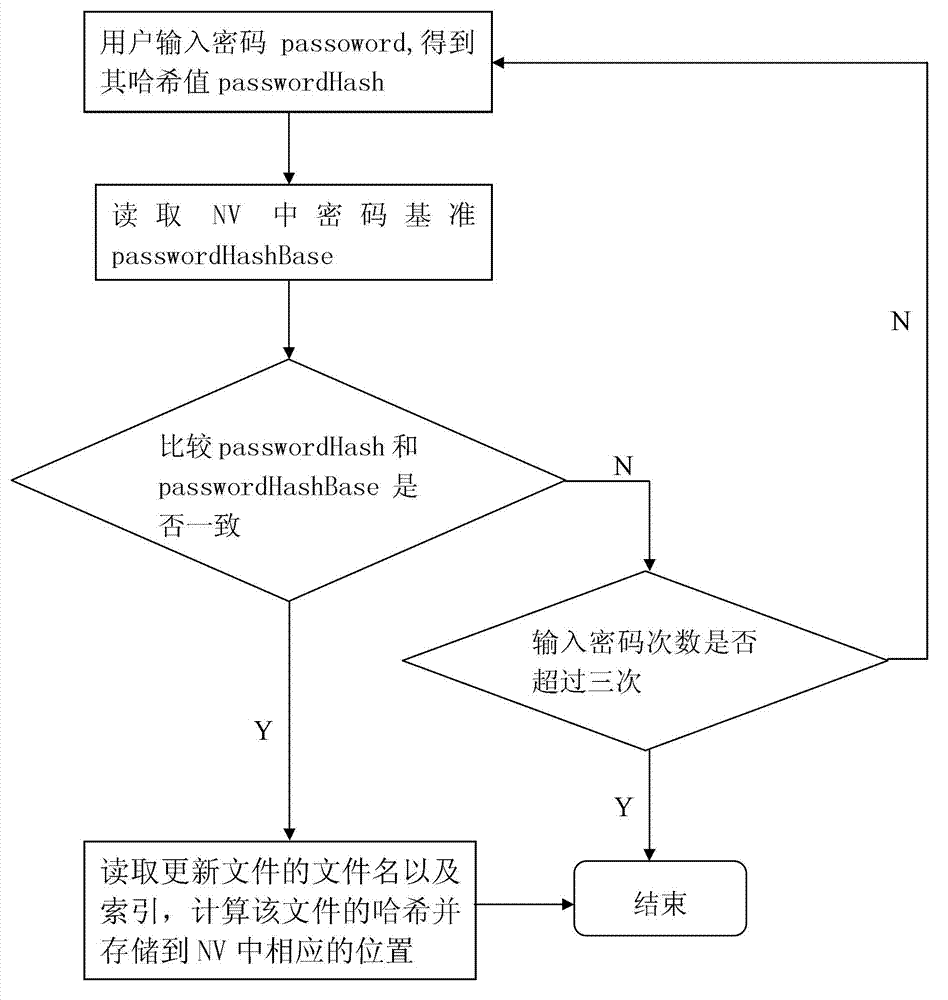
[0012] The present invention will be further described below with reference to the accompanying drawings and the specific implementation on the system with the TCM chip, but the scope of the present invention is not limited in any way.
[0013] The present invention mainly comprises following several parts, as figure 1 As shown, the benchmark update program is in the user state, and the data in the NV storage area can be read and written through the TCM driver. After the user updates the file, the benchmark of the NV storage area can be updated through this program. The measurement module is in the kernel state, calculates the hash value of the file when the file is loaded into the memory, and sends the calculated result to the verification module. The verification module can read the corresponding benchmark of the file in the NV storage area in the TCM through the TCM driver, then compare it with the measurement result, and send the comparison result to the measurement modul...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com