Network data control device and network data control method for controling network data that generates malicious code in mobile equipment
A technology for network data and control devices, which is applied in security devices, electrical components, transmission systems, etc., and can solve problems such as network data occupation bandwidth, Internet network bandwidth loss, and network speed reduction.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] Hereinafter, preferred embodiments of the present invention will be described with reference to the accompanying drawings.
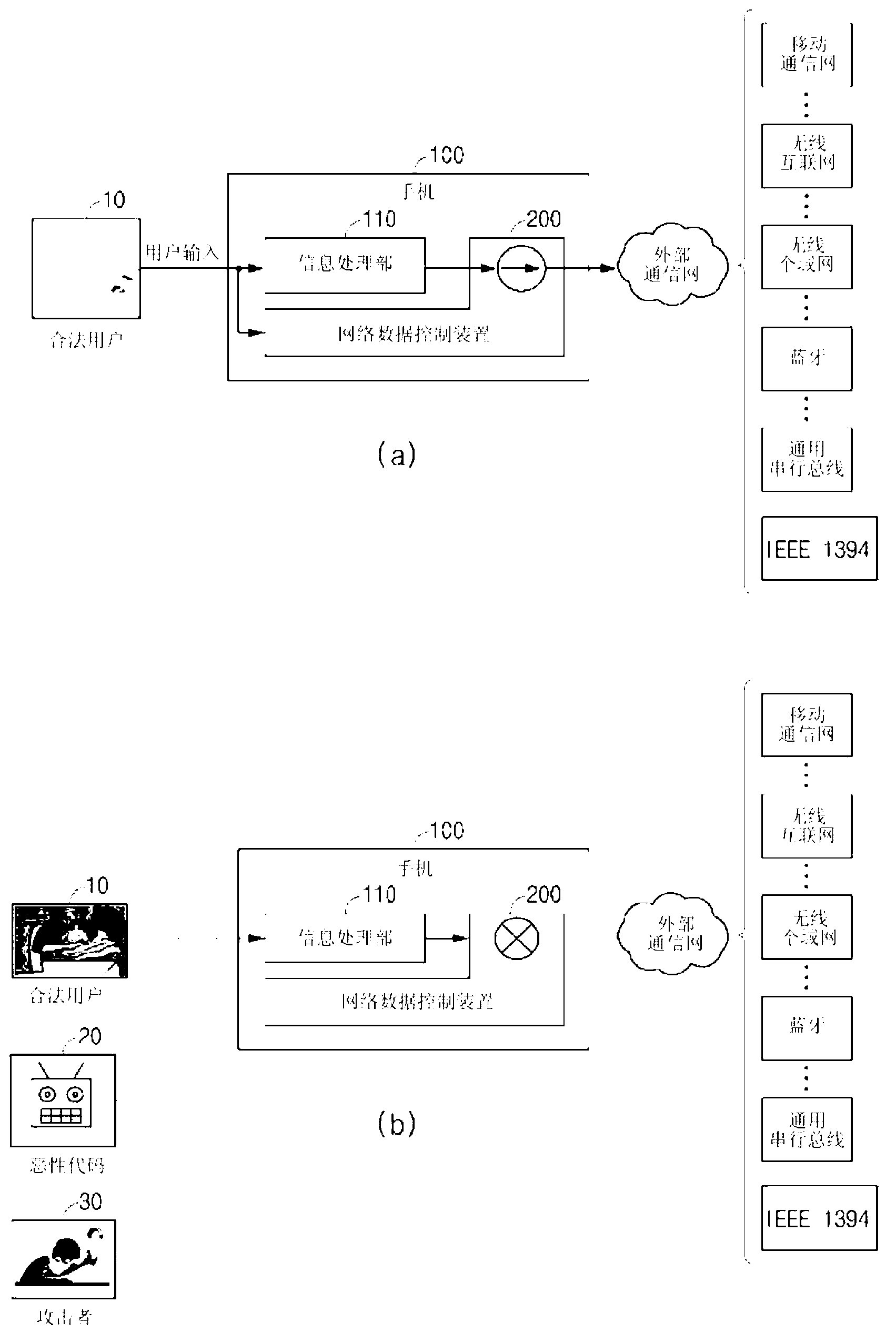
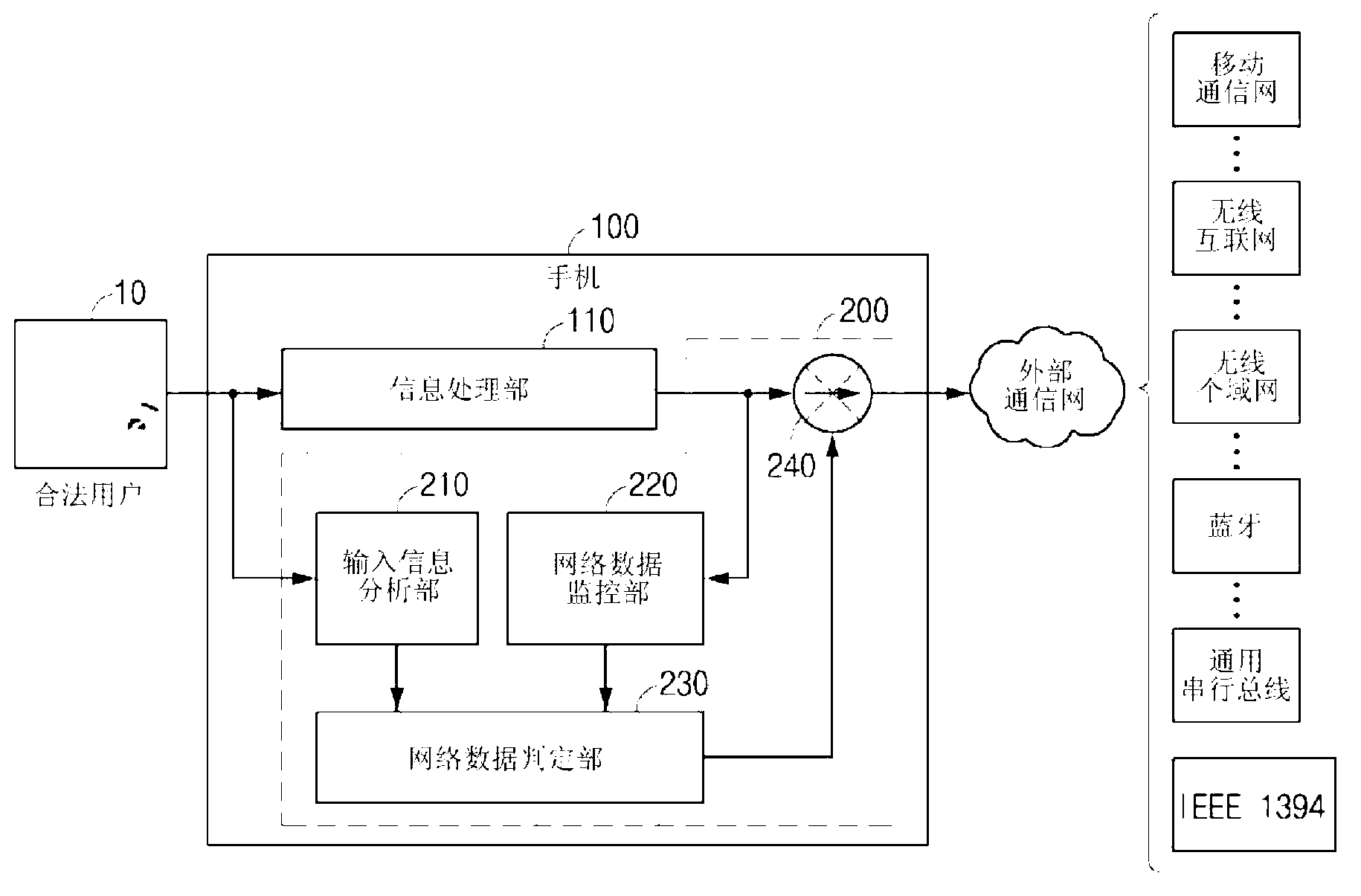
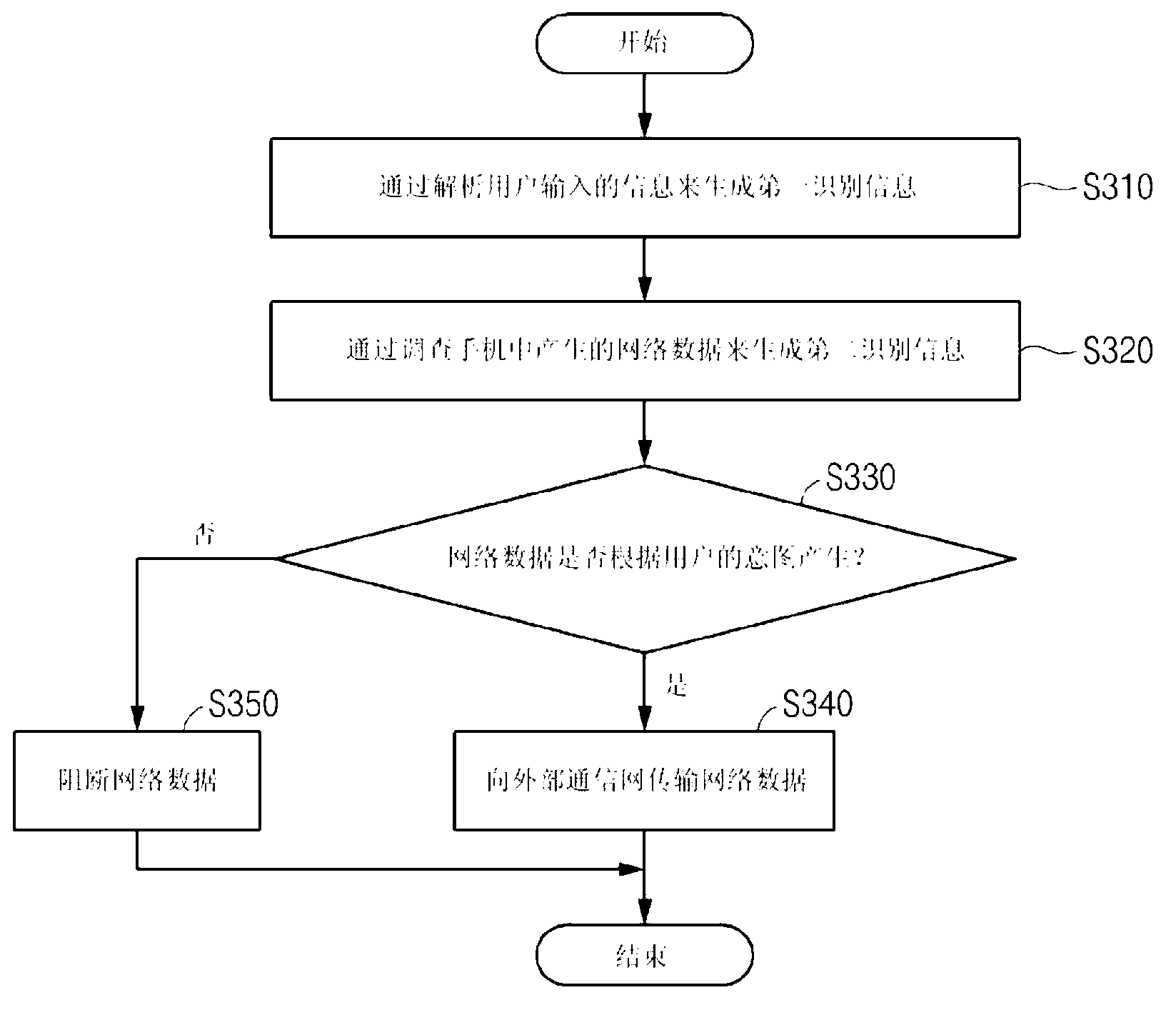
[0048] figure 1 It is a diagram illustrating the concept of a network data control method executed by a network data control device (hereinafter, simply referred to as "network data control device") that controls network data generated by malicious code in a mobile phone according to a preferred embodiment of the present invention.
[0049] The network data control device of the present invention can be implemented on the mobile phone 100 through software, or can be implemented on the mobile phone 100 after being implemented in hardware such as an ASIC chip.
[0050] refer to figure 1 (a) Observing the normal network data processing process, it can be seen that when the legitimate user 10 uses the mobile phone input device to input information, the information processing unit 110 that realizes the original function of the mobile phone 100 execute...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com