Computer information privacy detection method based on network
A detection method and information confidentiality technology, which is applied in the field of information security, can solve the problems of large influence of inspectors on inspection results, lack of sensitive information supervision, unified inspection, and difficulty in covering information security, and achieve the effect of improving awareness of confidentiality and prevention
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
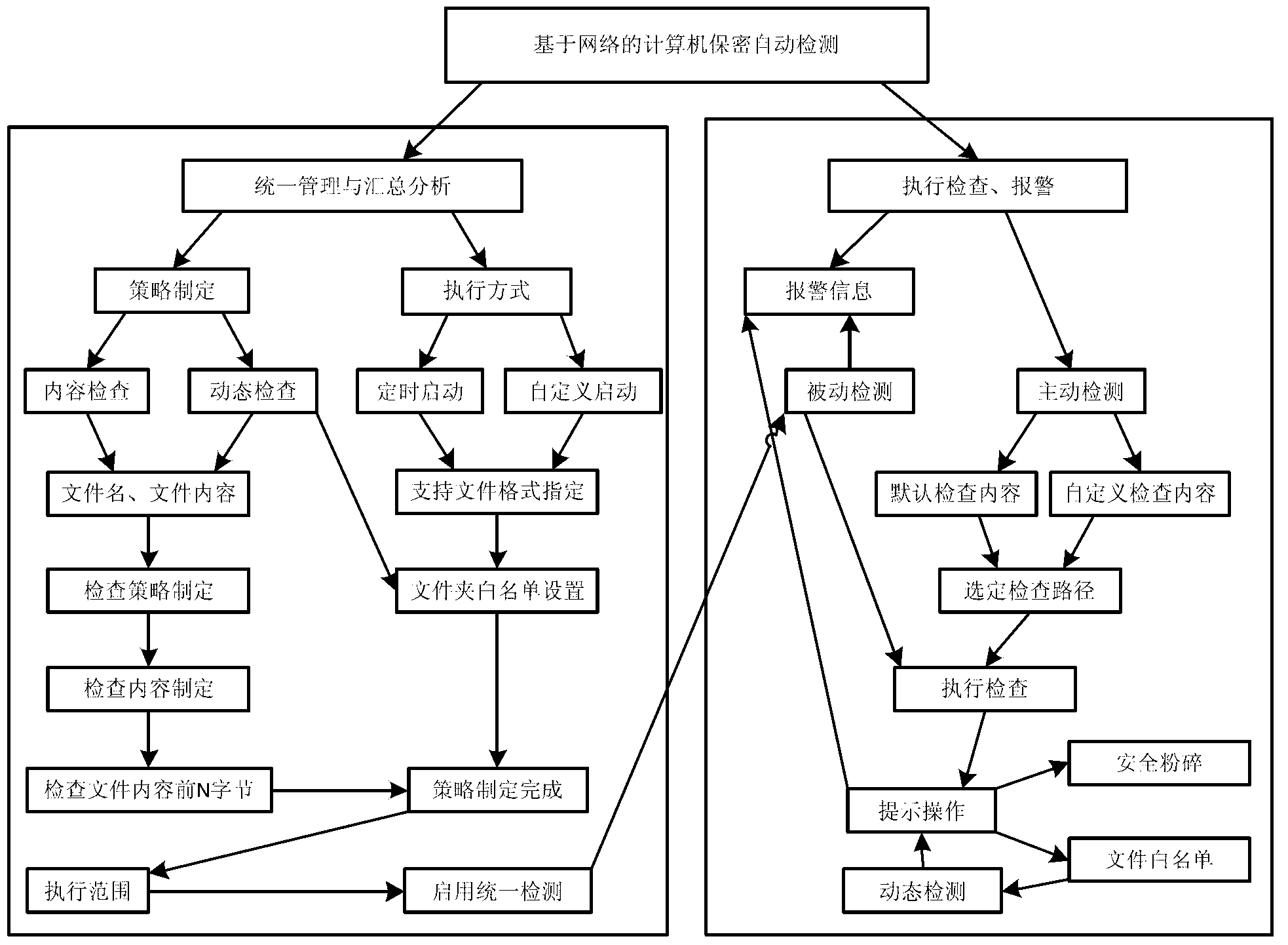
[0025] The present invention will be described in further detail below in conjunction with the accompanying drawings.
[0026] like figure 1 A network-based computer information security detection method is provided, the method comprising the following steps:
[0027] Step 1: The network server is associated with the computer client;
[0028] Step 2: Set the network server-side detection strategy;
[0029] Step 3: Determine the computer client detection strategy;
[0030] Step 4: File dynamic real-time monitoring and alarming.
[0031] In the step 1, a network server is set up, and the computer client is registered, so that the communication connection between the computer client and the network server is normal.
[0032] In said step 2, set a unified detection strategy on the network server side, perform background detection on the computer client according to the setting of the detection strategy, and satisfy different confidentiality levels through targeted formulation...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com