Methods and systems for cross site forgery protection
一种应用层、应用防火墙的技术,应用在传输系统、数字数据保护、仪器等方向
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] In order to read the following description of various specific embodiments, the following sections of the specification and their respective descriptions are useful:
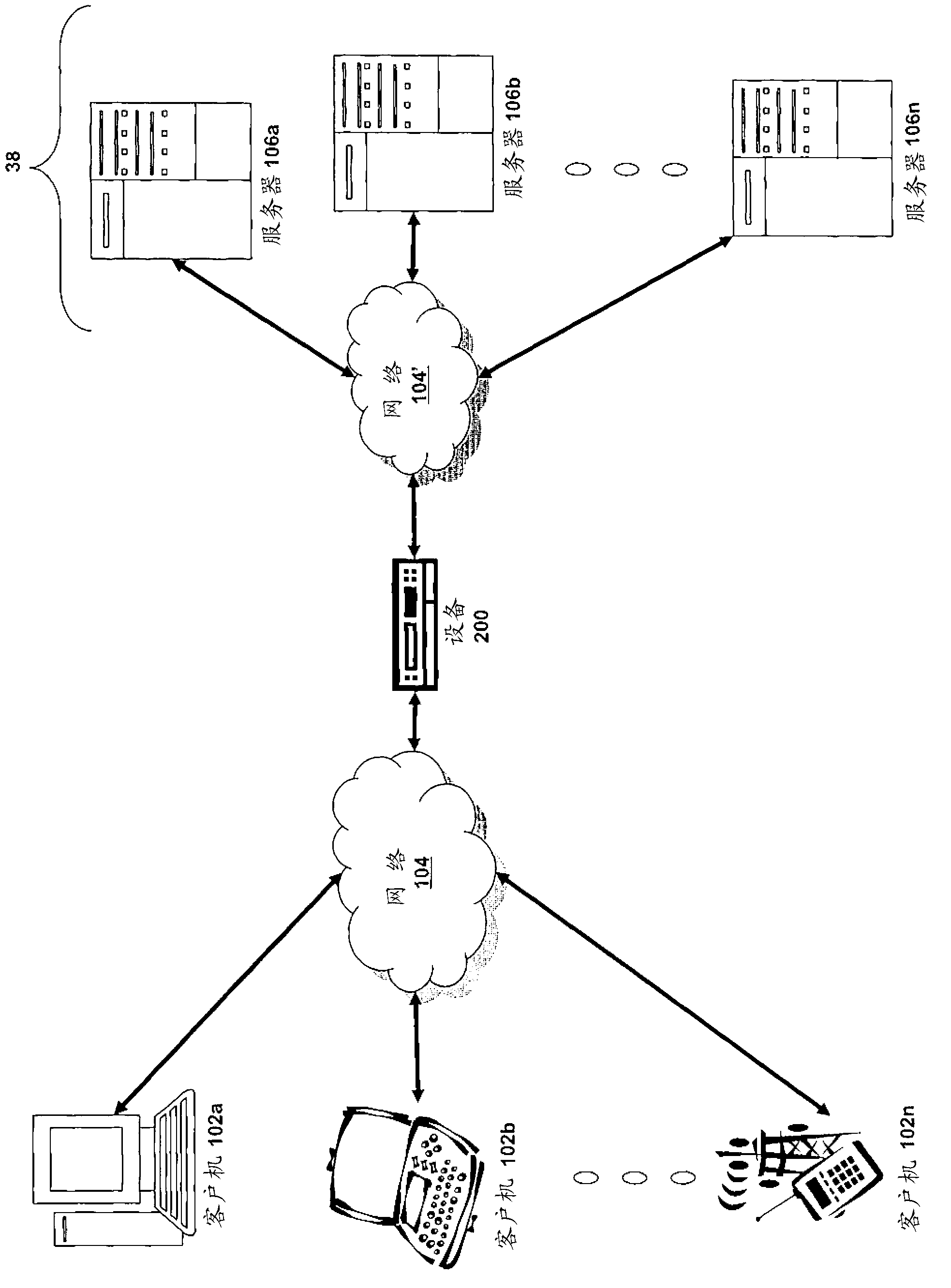
[0040] - Part A describes network and computing environments that are useful for implementing the embodiments described herein;
[0041] - Part B describes an embodiment of a system and method for delivering a computing environment to a remote user;
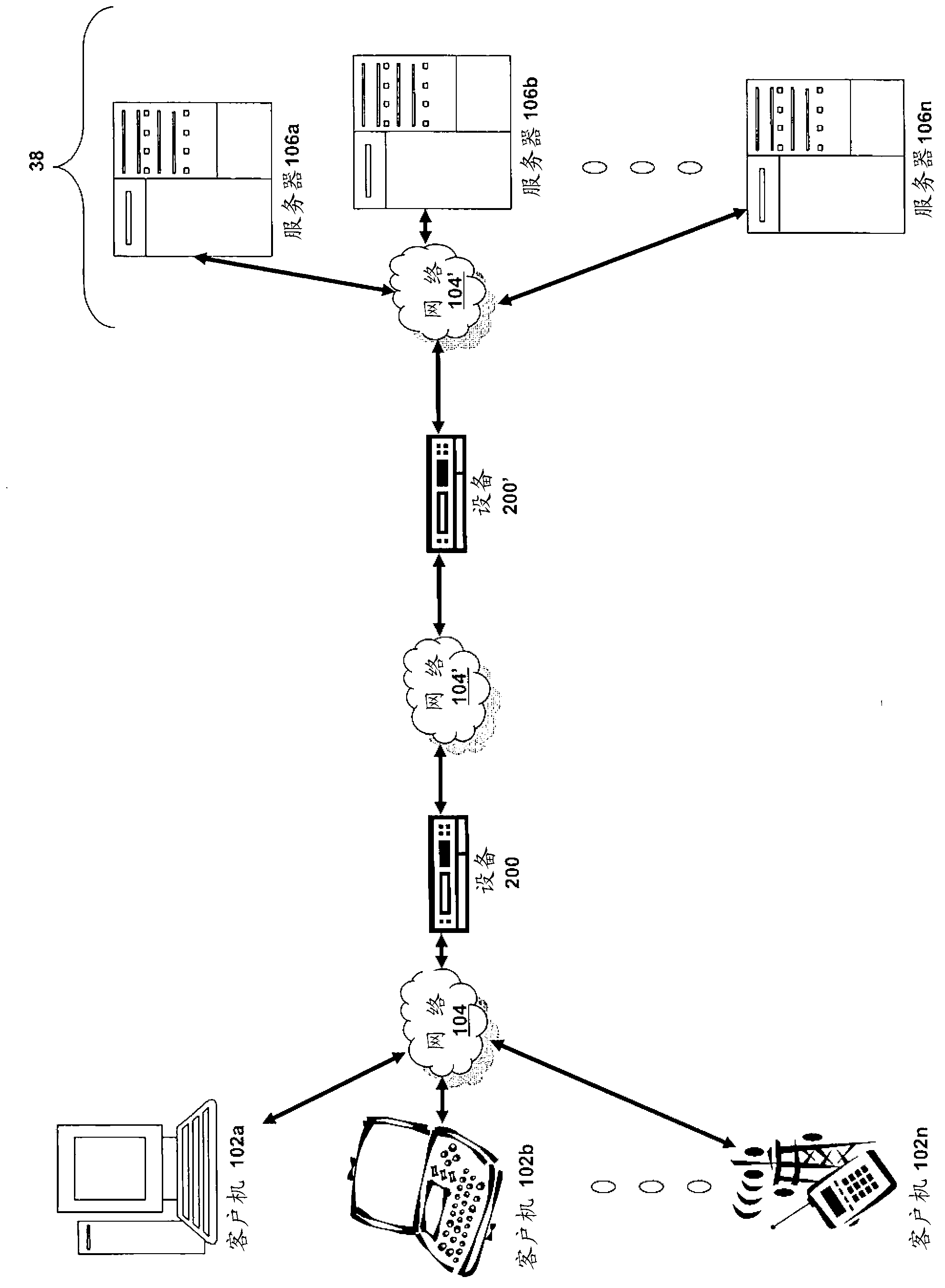
[0042] - Part C describes embodiments of systems and methods for accelerating communication between clients and servers;
[0043] - Section D describes an embodiment of a system and method for virtualizing an application delivery controller.
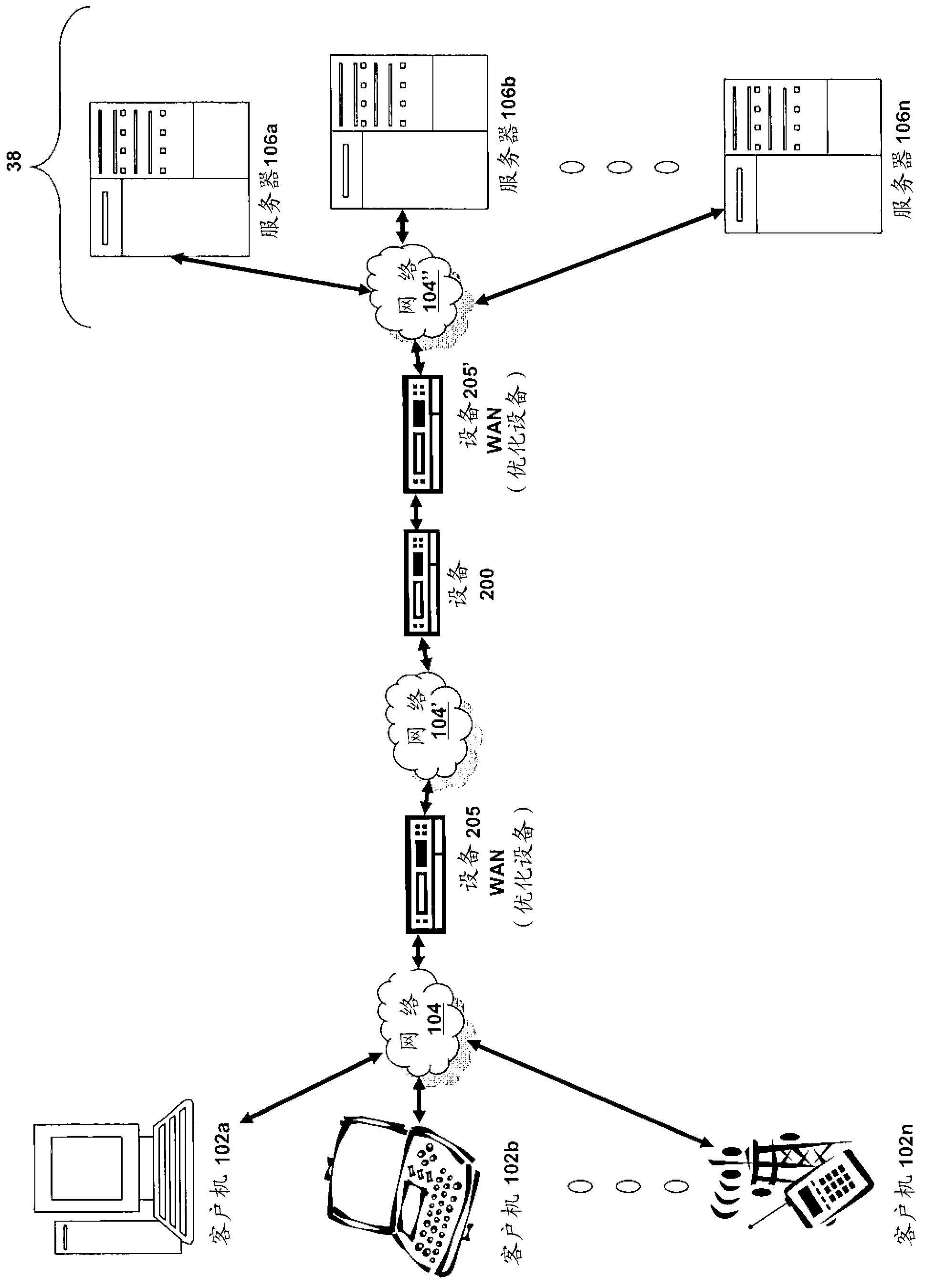
[0044] - Part E describes embodiments of systems and methods for providing multi-core architectures and environments;
[0045] - Part F describes embodiments of systems and methods for providing protection against cross-site forgery; and
[0046] - Section G describes embodiments of systems and methods for protectin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com