Offline verification method for single sign on
A verification method and single sign-on technology, applied to electrical components, transmission systems, etc., can solve problems such as high service costs and delays, and achieve the effect of convenient service response
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
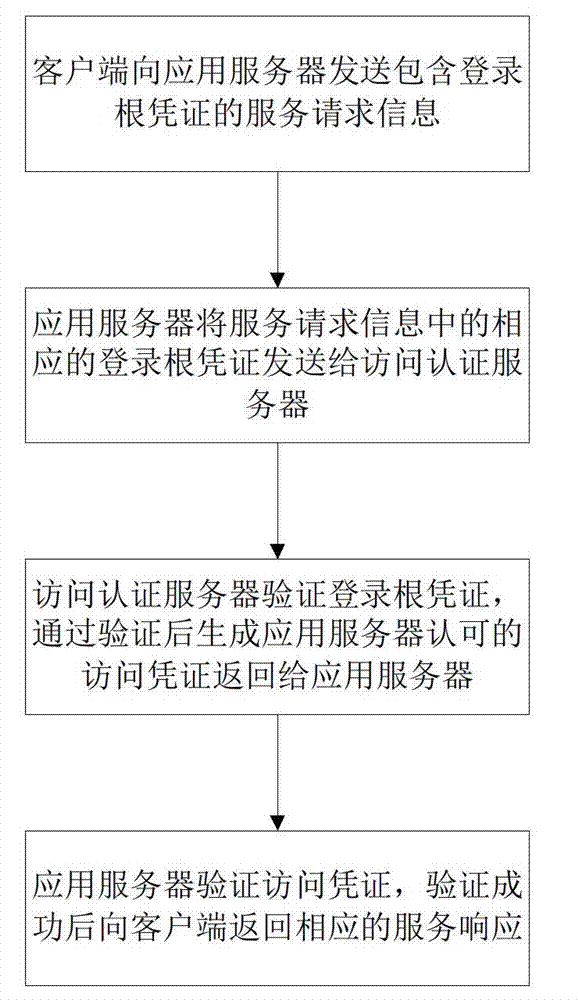
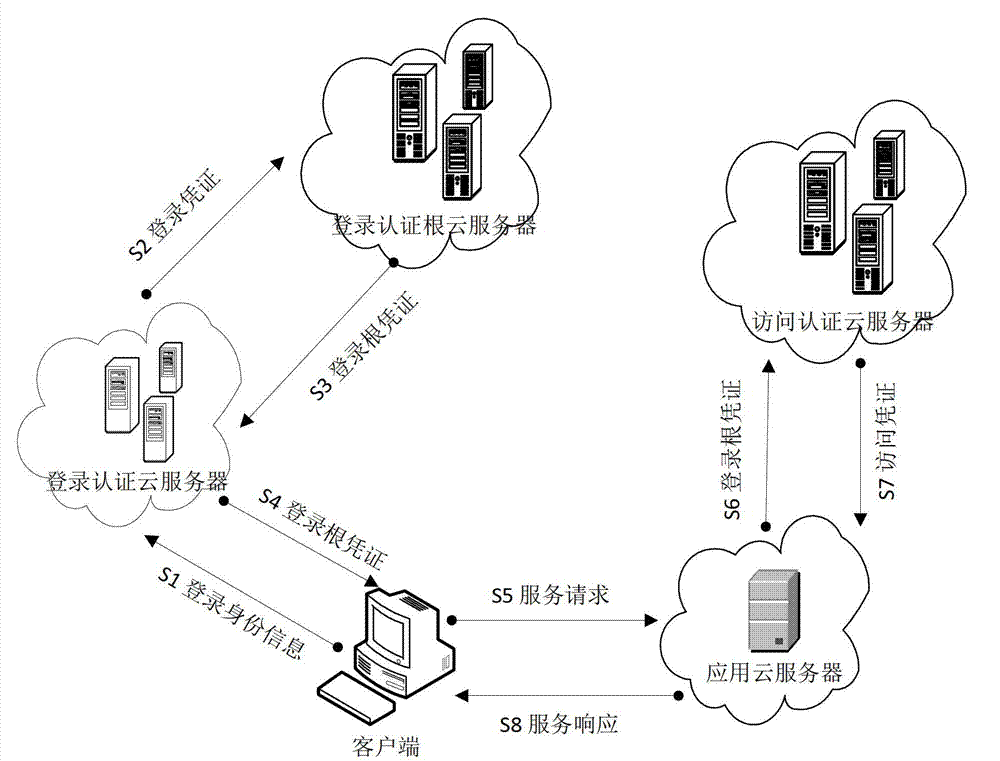
[0024] An off-line verification method for single sign-on, which is applied to an identity authentication system, and the identity authentication system includes a login authentication server, a login authentication root server, and an access authentication server. The premise of the offline verification of the method of the present invention is that the user has passed the first login authentication and has the corresponding credentials for service requests. Requested login root credentials, see figure 1 , the verification of the subsequent service request in the method of the present invention comprises the following steps:
[0025] The client sends service request information including login root credentials to the application server;
[0026] The application server sends the corresponding login root credentials in the service request information to the access authentication server;
[0027] The access authentication server verifies the login root credential, generates th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com