Webpage tamper proofing method realized by windows driver layer
An anti-tampering, driver layer technology, applied in the direction of instruments, program/content distribution protection, electronic digital data processing, etc., to achieve the effect of low resource occupation and fast response speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0017] The present invention will be described in detail below with reference to the drawings and specific embodiments.
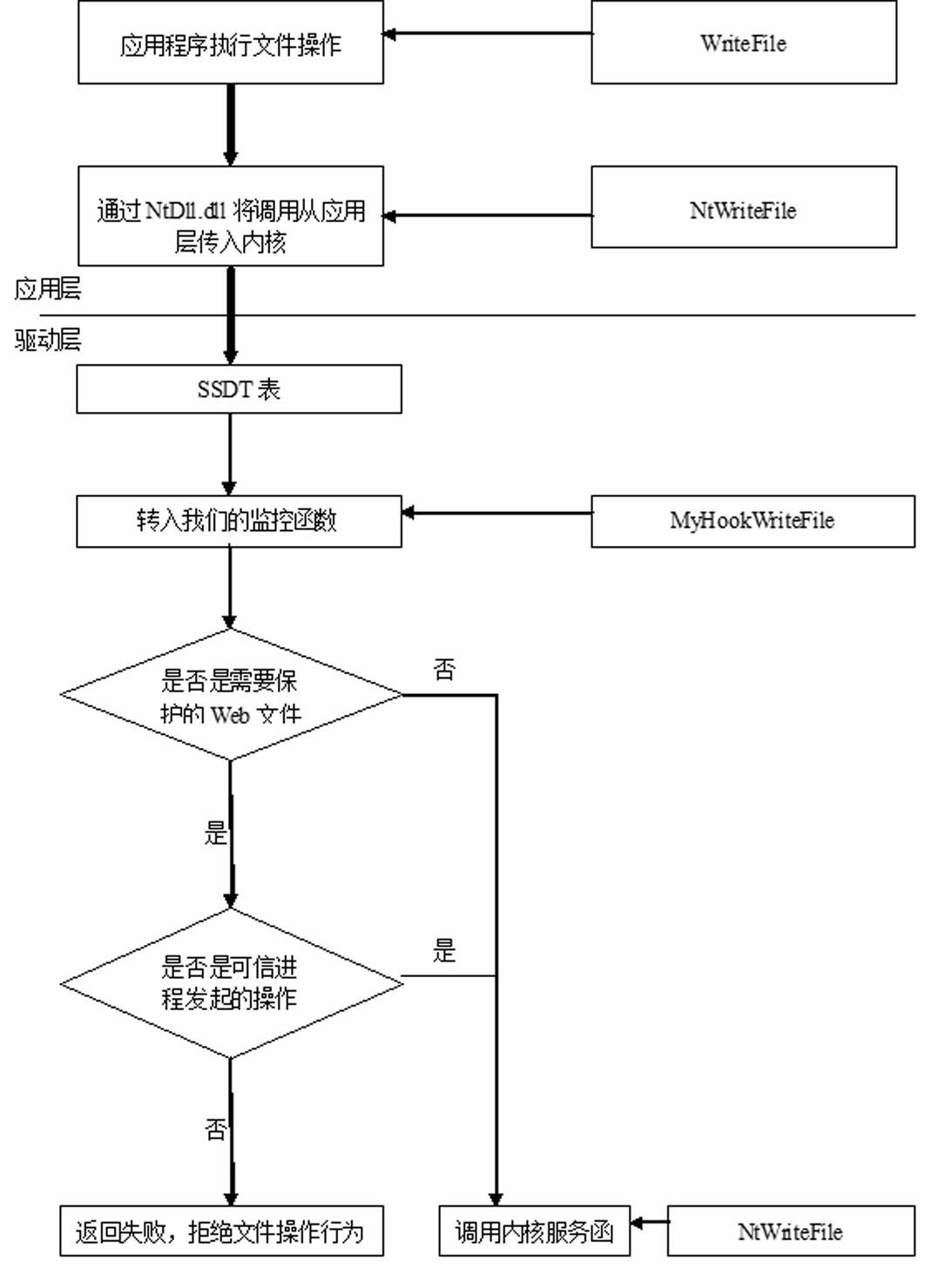
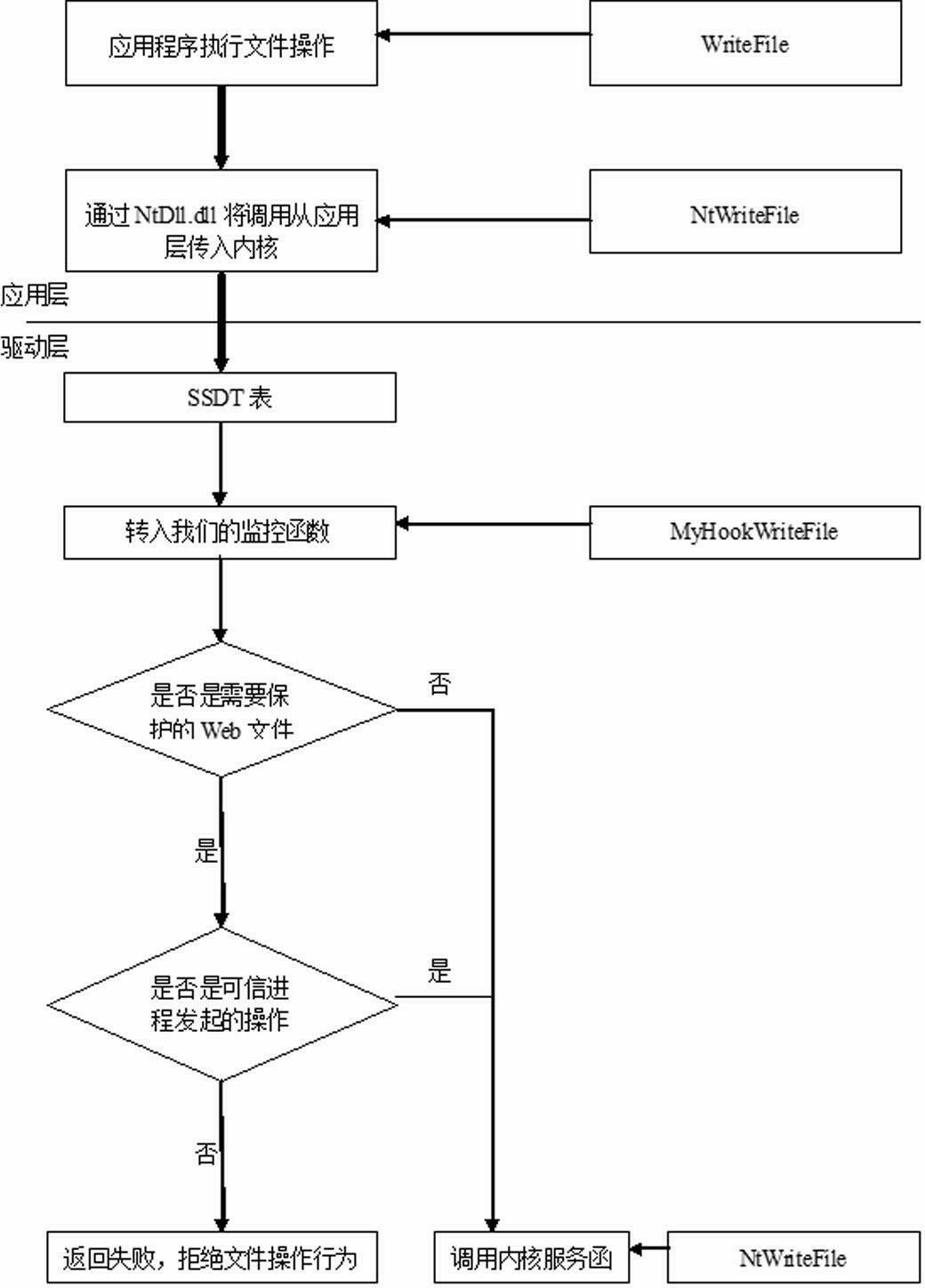
[0018] The webpage tamper-proof method implemented from the driver layer using Windows SSDT HOOK. The full name of SSDT is System Services Descriptor Table. This table is a link between Ring3's Win32 API and Ring0's core API. SSDT is more than just It only contains a huge address index table, which also contains some other useful information, such as the base address of the address index, the number of service functions, etc. By modifying the function address of this table, you can hook common Windows functions and APIs, thereby To achieve the purpose of filtering and monitoring some system actions of interest, in Windows operating systems above NT 4.0, there are two system service description tables by default. These two scheduling tables correspond to two different types of system services. The schedule tables are: KeServiceDescriptorTable and KeServiceDescr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com