Monitoring method and monitoring system
A technology for monitoring systems and verifying passwords, which is applied to instruments, electrical digital data processing, and platform integrity maintenance. status, the effect of preventing malicious theft
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
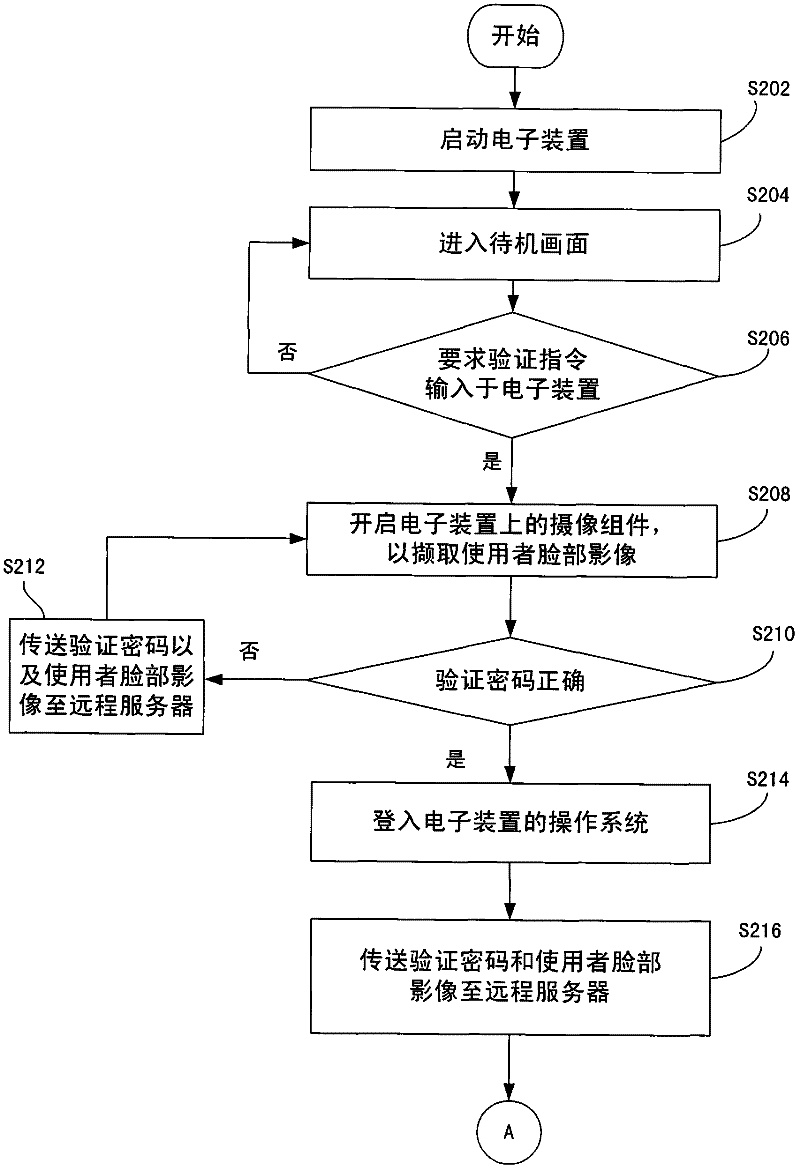
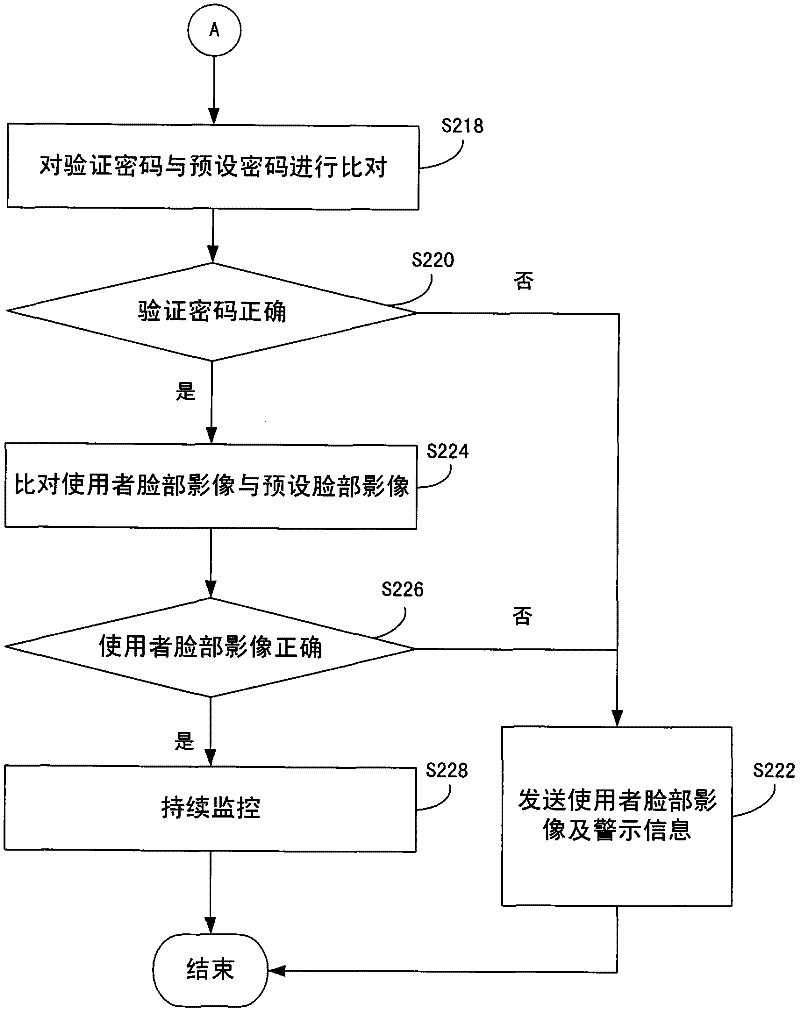
[0030] The following exemplified embodiments are described in detail in conjunction with the accompanying drawings, but the provided embodiments are not used to limit the scope of the present invention, and the description of the structure and operation is not used to limit the order of its execution, and any recombination of components The structure of the resulting device with equal efficacy is within the scope of the present invention. The drawings are for illustration purposes only and are not drawn to original scale.
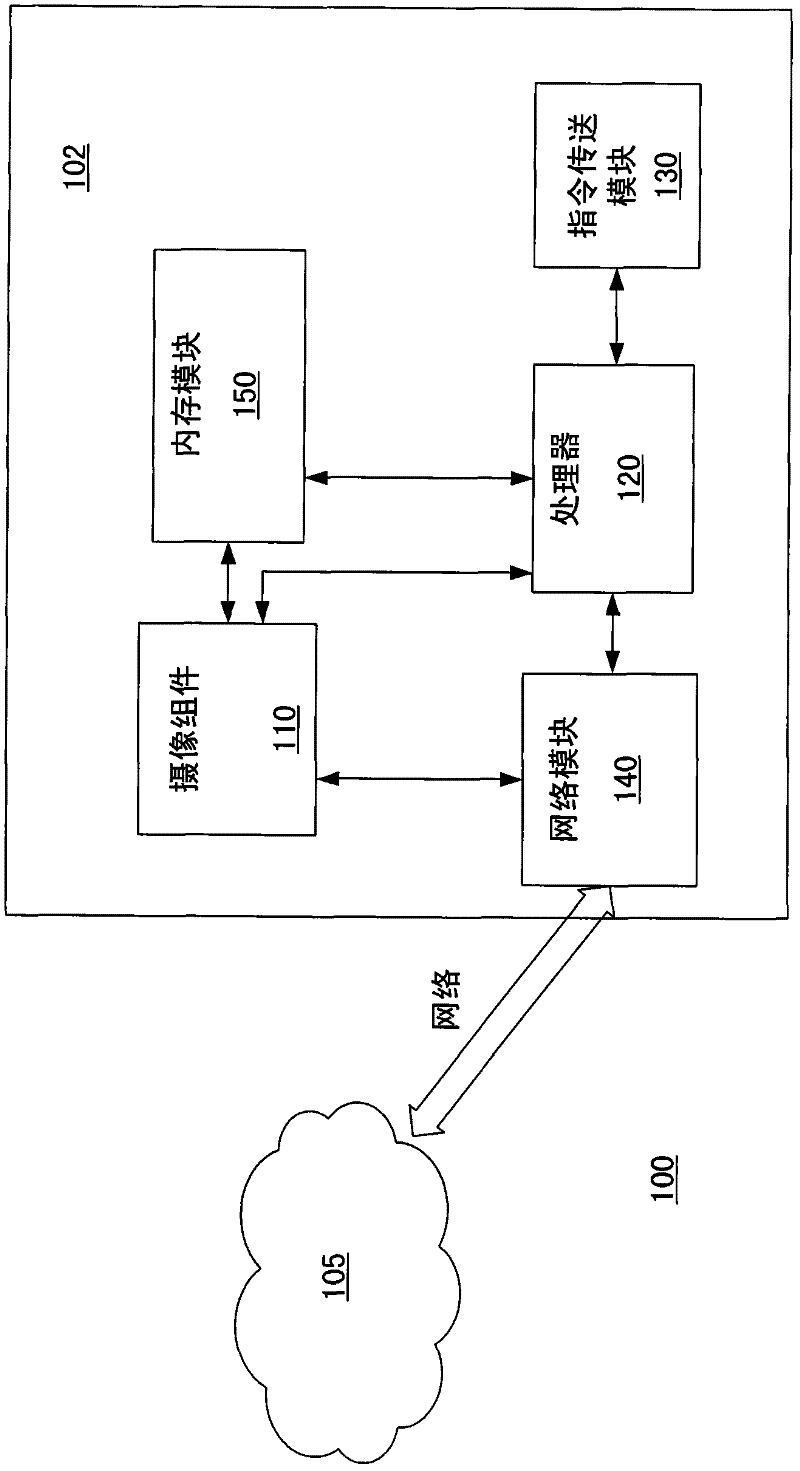
[0031] figure 1 A schematic diagram of a monitoring system is shown according to an embodiment of the present invention. The monitoring system 100 includes an electronic device 102 and a remote server 105 , wherein the electronic device 102 communicates with the remote server 105 through a network. Here, the electronic device 102 can be integrated and applied to notebook computers, tablet computers, desktop computers or other types of computers or mobile ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com