Method for setting permission password for mobile phone
A permission password and password technology, which is applied in the field of mobile phone permission password setting, can solve the problems of privacy leakage, lack of sincerity of the owner, and failure to refuse to borrow, etc., to achieve the effect of protecting privacy and protecting privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] The following will describe in detail with reference to the accompanying drawings in conjunction with the embodiments, so as to further explain the technical features and advantages of the present invention.
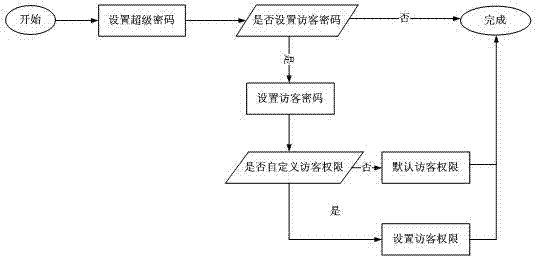
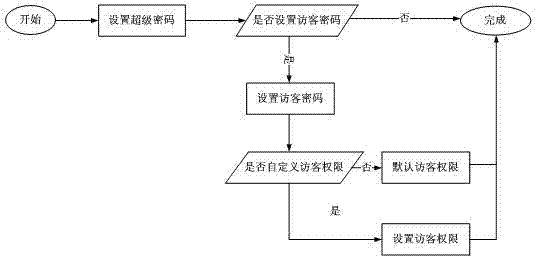
[0020] Method flow chart of the present invention is as figure 1 As shown, a method for setting a mobile phone authority password, the steps are as follows:
[0021] Step 1. Enter the authority password setting program;
[0022] Step 2. Set the highest authority password;
[0023] Step 3. Determine whether to set a visitor password, if yes, perform step 4, otherwise complete the permission password setting;
[0024] Step 4, execute the program of setting visitor password;
[0025] Step 5. Determine whether to customize visitor permissions, if yes, perform step 6.1, otherwise perform step 6.2;
[0026] Step 6.1, set visitor permissions, go to step 7;
[0027] Step 6.2, the visitor authority set by the default system, go to step 7;
[0028] Step 7. Complete th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com