Level-driving security demand analysis method
A requirement analysis and leveling technology, applied in the field of trusted computing, can solve problems that affect the accuracy of software security requirements, unusable civilian systems, and frequent user participation, so as to reduce security vulnerabilities, reduce possibilities, and improve security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
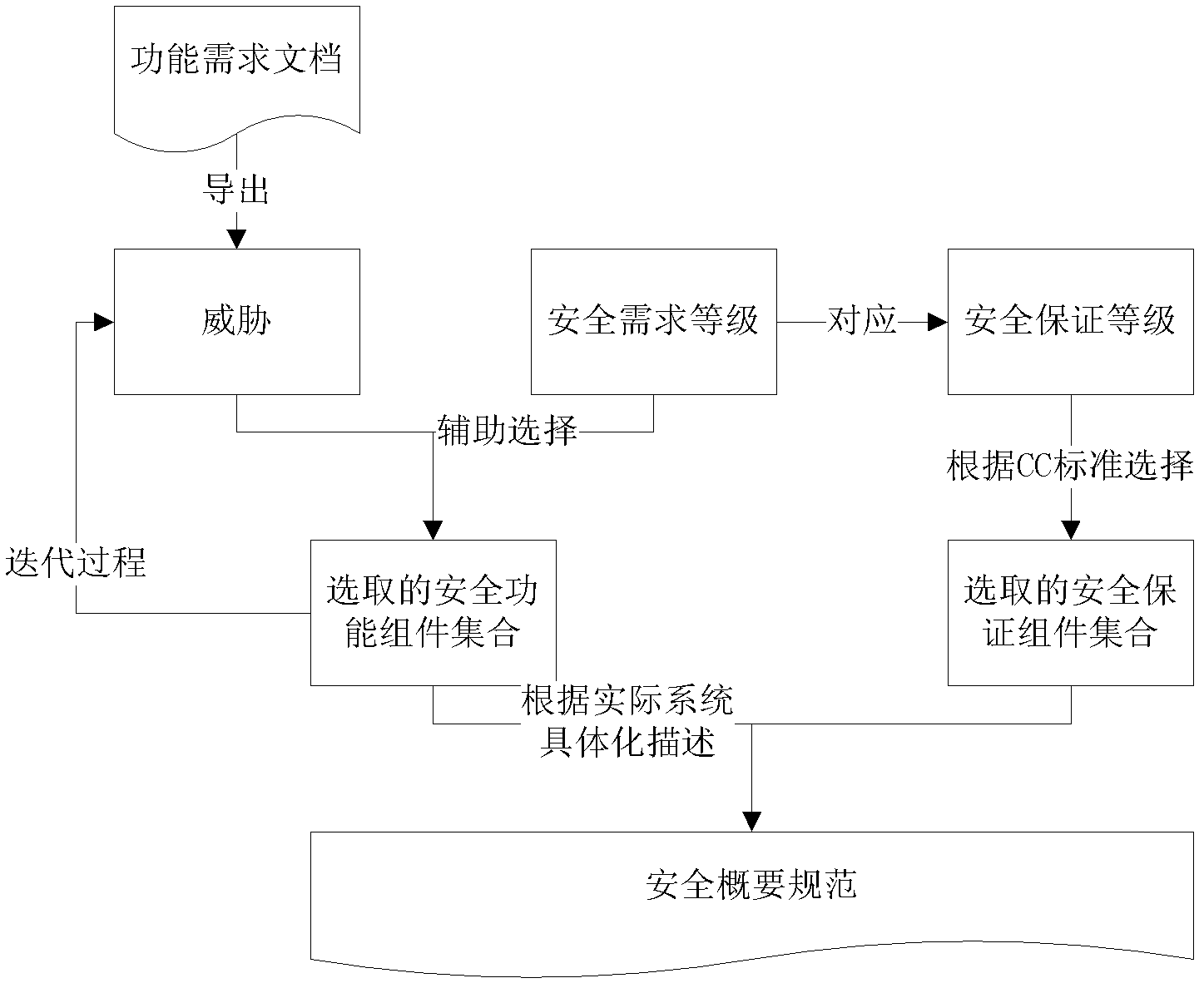
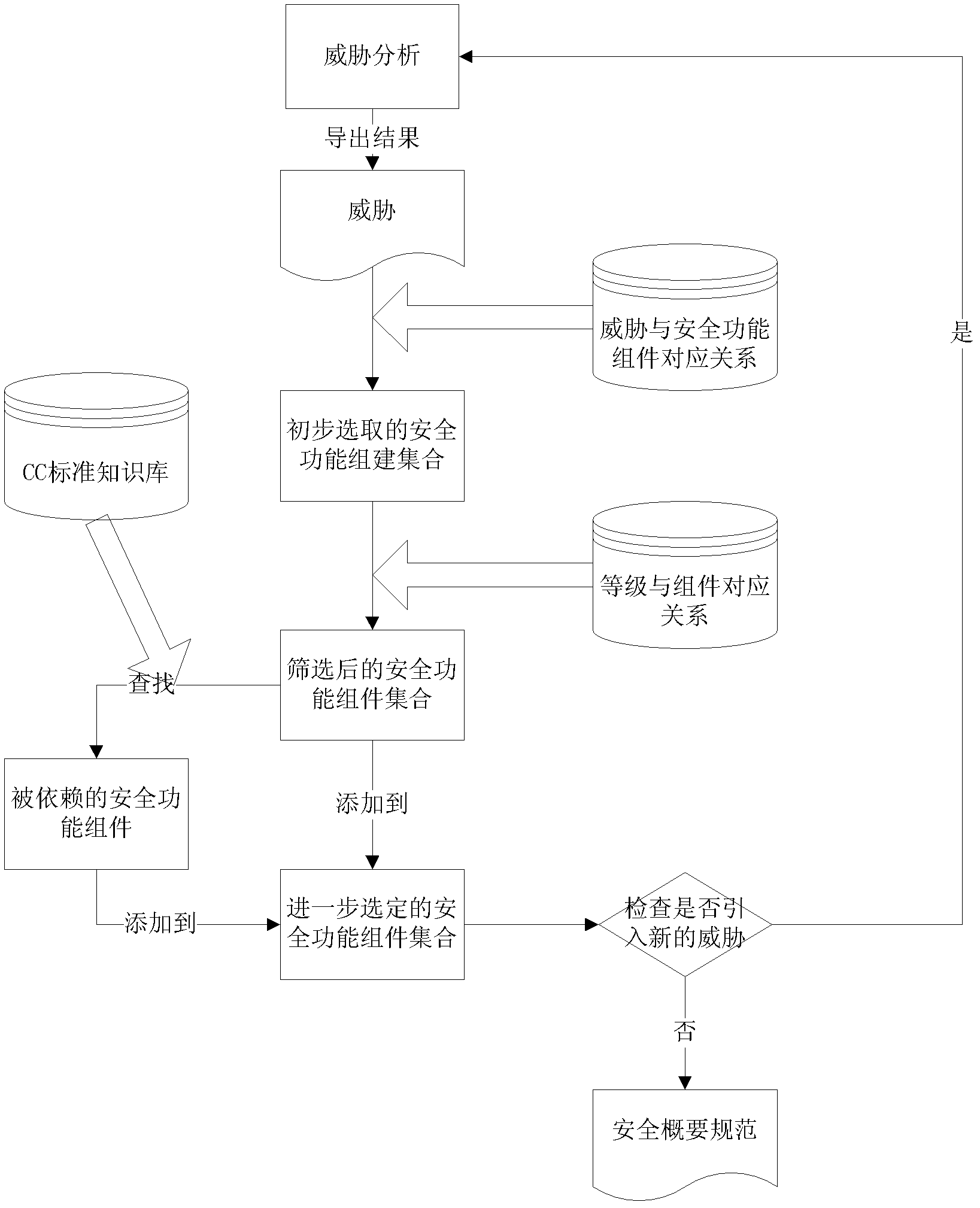
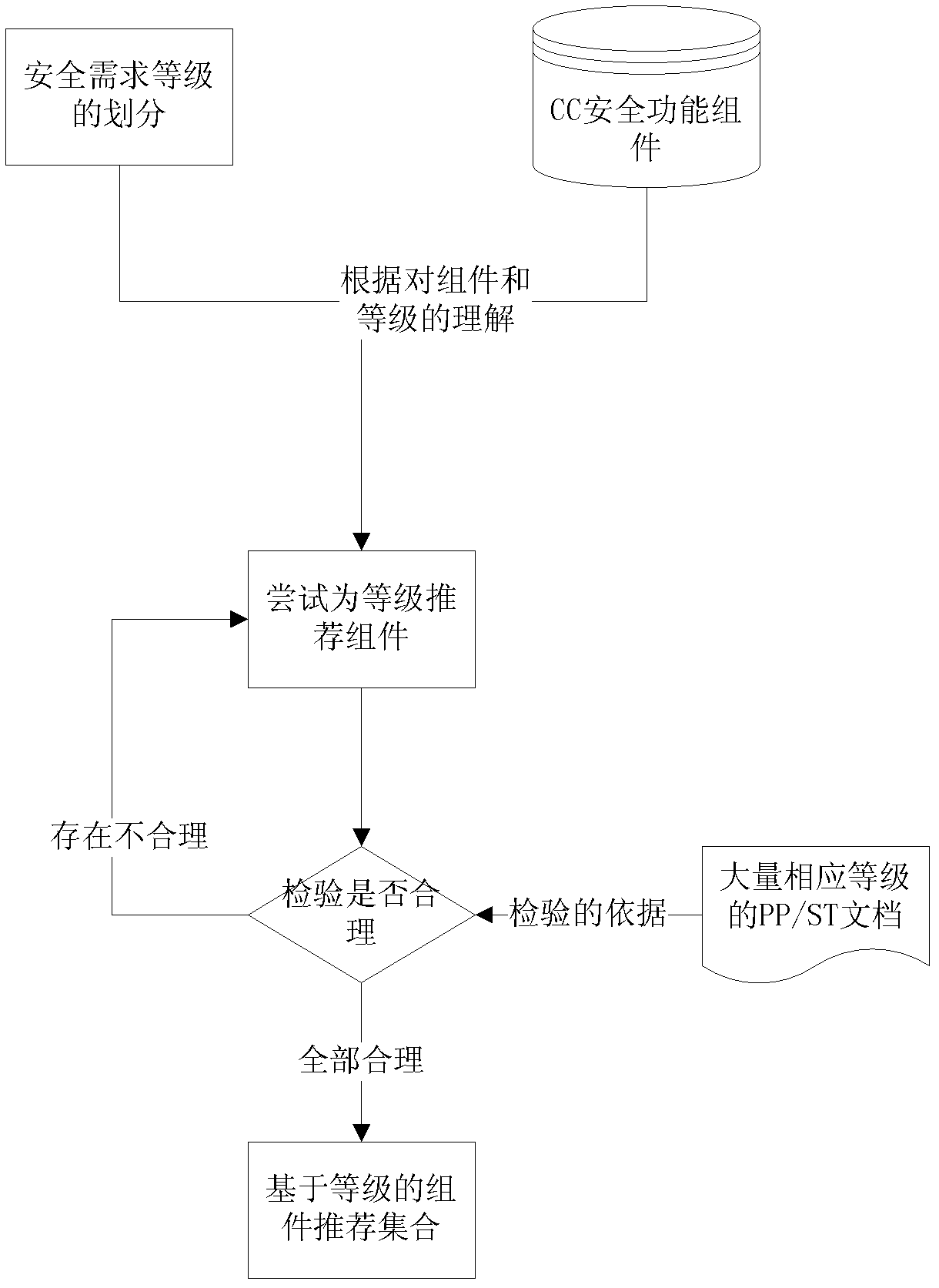
[0031] The overall technical solution flow of the present invention is shown in accompanying drawing 1, comprises two processes, first is the division of safety requirement level and the establishment of the corresponding relationship between level and safety function component, this process is the construction of knowledge base, can be finished after Applied as empirical knowledge in concrete each concrete development. Then, in the development of a specific system, according to the level of security requirements put forward by the user for the system, the security function components selected according to the threat are screened, and then the security requirements analysts consider the specific technology and security strategy, and the final selection Defined security functional components are described as security profile specifications. The following is a detailed introduction in conjunction with accompanying drawing 2, which is specifically divided into two processes:
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com