Multiband/Multilink Secure Key Generation and Delivery Protocol
A multi-link, link technology, applied in the field of security and encryption, which can solve problems such as key reuse attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] overview
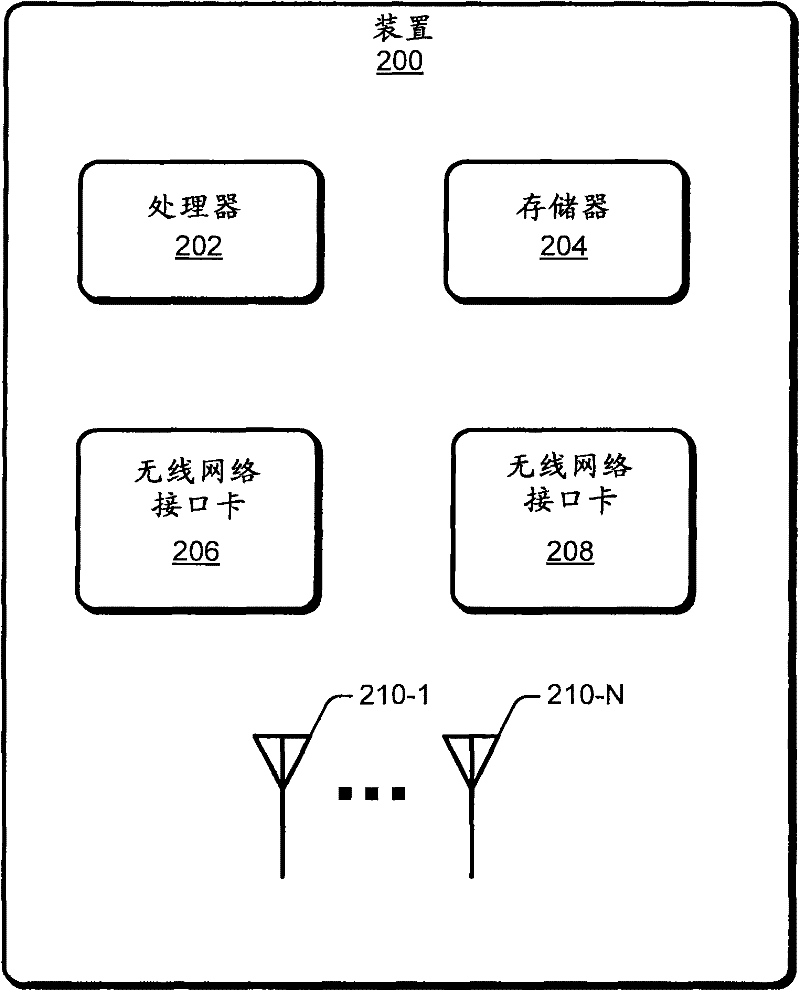
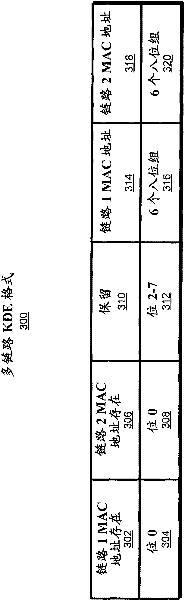
[0021] In a wireless communication device in which a device may operate as either or both a verifier or a supplicant, a secure key generation and delivery protocol is implemented for operation in multiple bands / multiple links. In one implementation, the IEEE 802.11 key management and delivery protocol can be extended to work in a multi-band environment, where a different cipher suite can be used in each of the different frequency bands. For example, the techniques and mechanisms can be implemented to be compatible with existing IEEE 802.11 key generation and delivery protocols used in the 2.4 / 5GHz bands of operation. Additionally, provision is made for concurrent operation or dynamic switching between 2.4GHz / 5GHz and 60GHz multi-link operation. Specifically, a single 4-way handshake between devices is used to allow interfaces of different frequency bands (eg 2.4 / 5GHz and 60GHz) to obtain keys.
[0022] network implementation
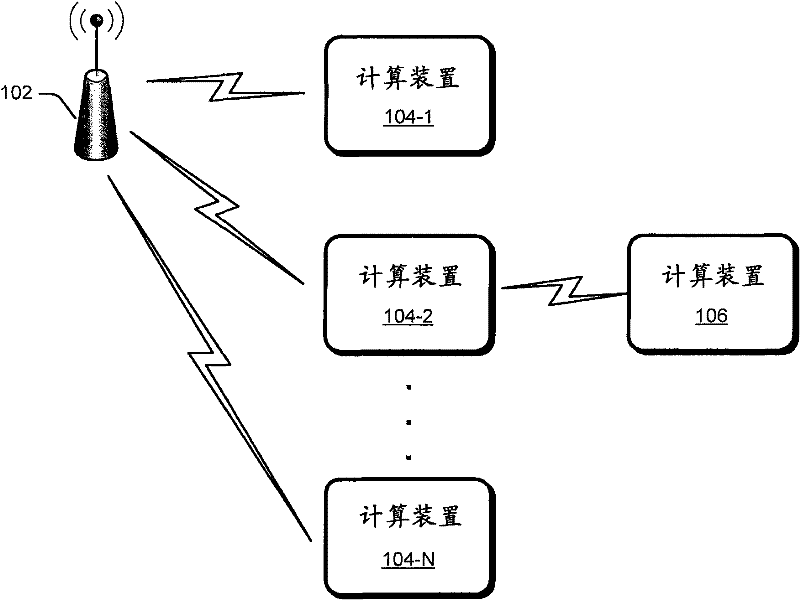
[0023] figure 1 An exemp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com