Safety isolation method for virtual network and physical network of cloud computing
A technology of virtual network and physical network, applied in the field of cloud computing virtual network and physical network isolation security, can solve problems such as security risks, physical network and virtual network are not isolated, and restrict cloud computing maturity.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] The present invention will be further described below in conjunction with the accompanying drawings.
[0032] Such as figure 2 As shown, the present invention discloses a security method for isolating a cloud computing virtual network and a physical network,
[0033] The methods include:
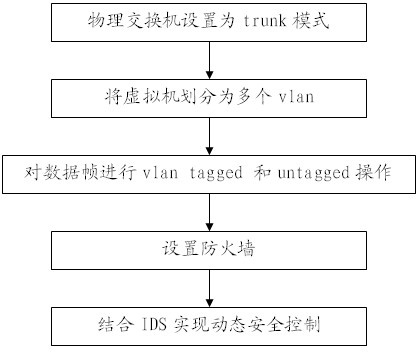
[0034] 1) Set the interface connected to the physical network card of the physical switch to trunk mode;
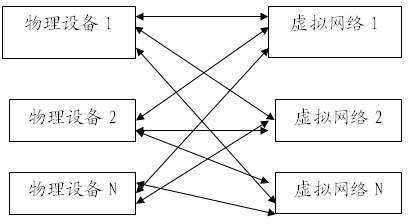
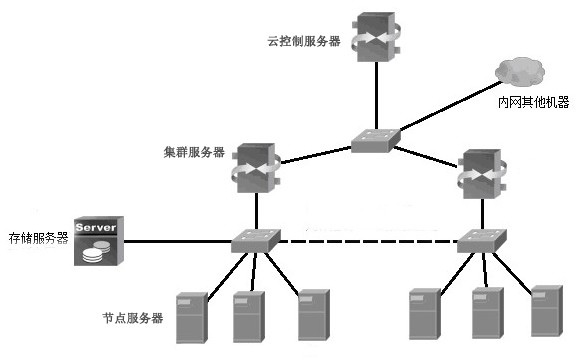
[0035] 2) The node server divides one or more virtual machines contained in multiple different vlans through the virtual network bridge and virtual switch, and performs vlan tagged and untagged operations on the data frames sent from the physical network card of the node server. The data frame identifies the data frame according to the vlan id information of the corresponding tag header, and realizes the isolation of the two-layer network;
[0036] Layer 2 network isolation can perform VLAN tagged and untagged operations on data frames through the VLAN function provided by th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com