Malicious website detection method and device
A malicious website and detection method technology, applied in the direction of platform integrity maintenance, etc., can solve the problems of timeliness and accuracy rate decline, and achieve the effect of reducing the possibility of false positives, low efficiency, and high accuracy rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
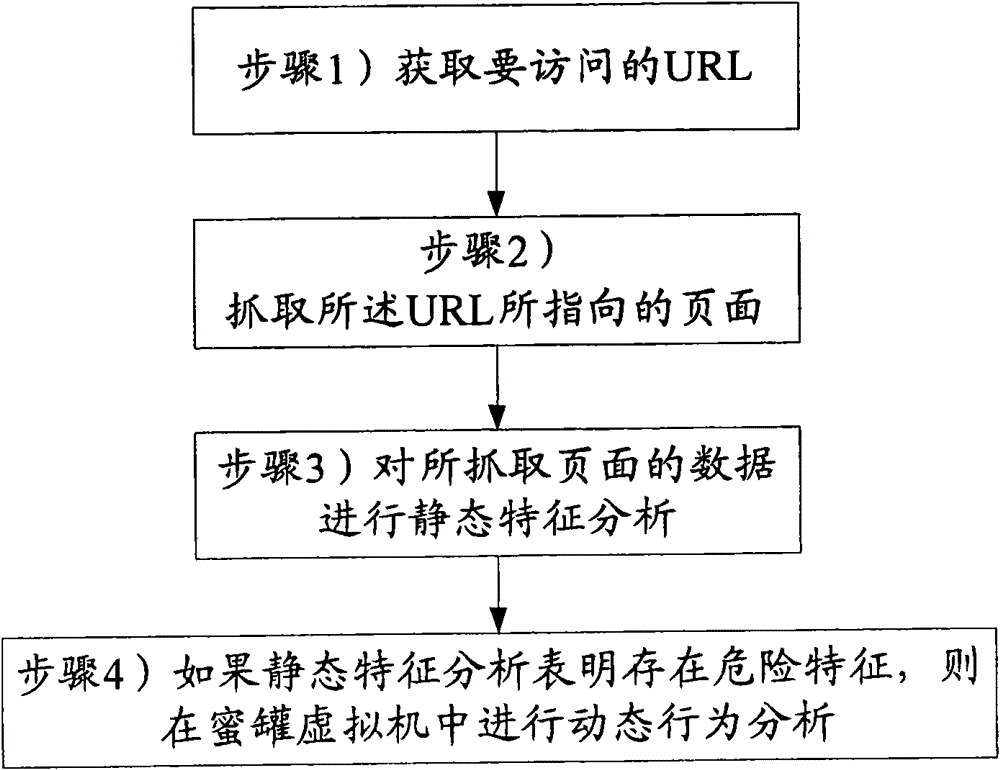
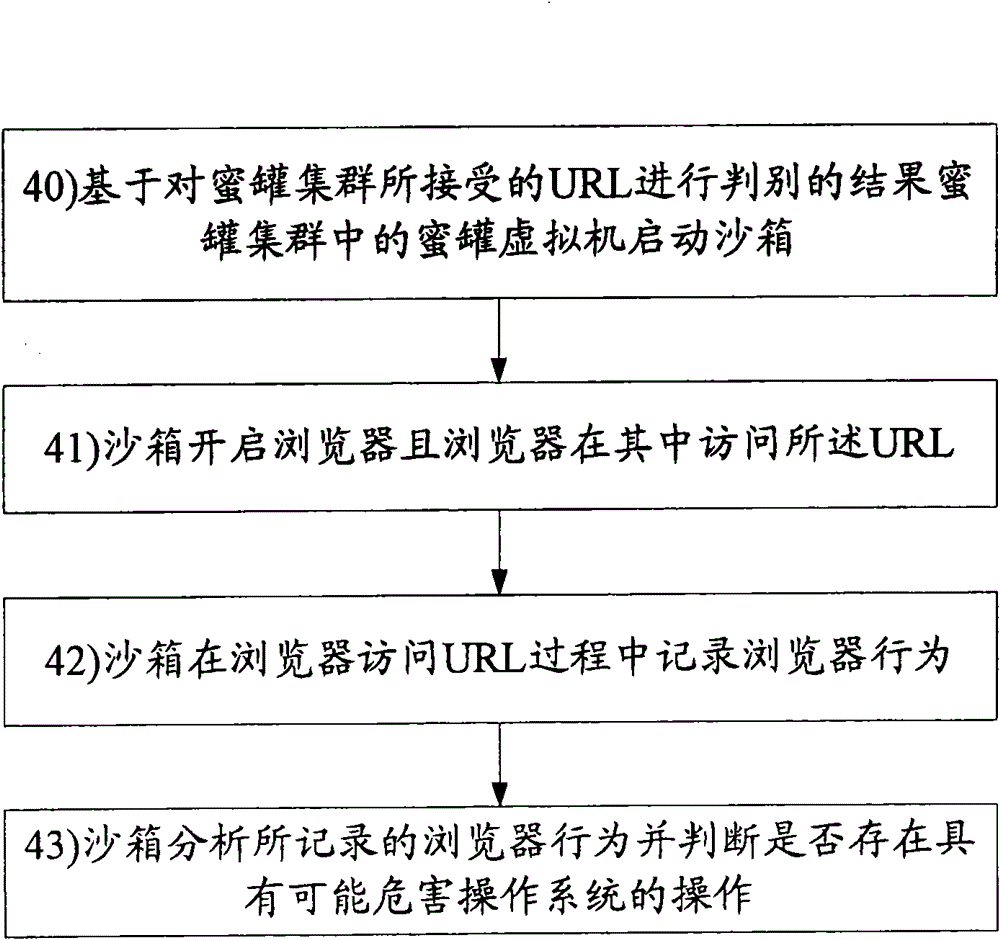
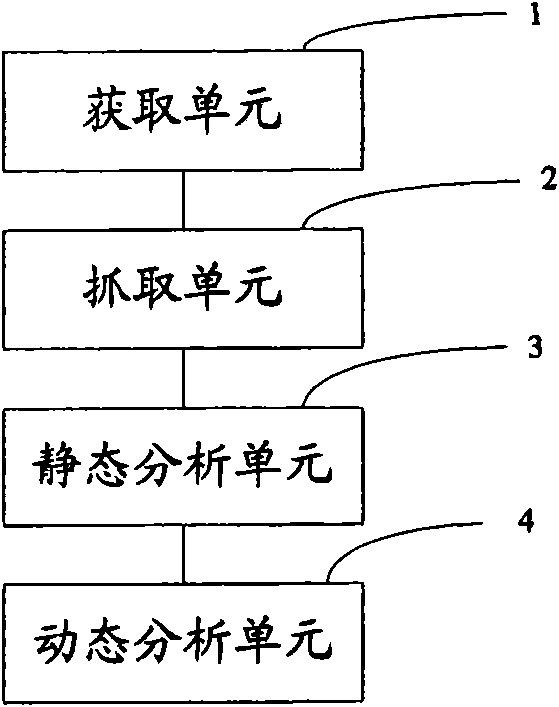
[0050] Specific examples of the present invention will be described in detail below, but the present invention is not limited to the following specific examples.
[0051] First, the technology adopted in the present invention is introduced.
[0052] ·Honeypot Technology
[0053] Honeypot technology is essentially a derivative developed due to the development of virtual machine technology. For example, the VMWARE virtual machine software produced by the famous VMware virtual machine technology company. Its characteristic is that it can build a technology that can be controlled without affecting the real machine but can be restored to the normal state arbitrarily according to the needs of users. Using the technology of virtual machine, when the operation that may affect the real machine, the virtual machine technology will be used to build the honeypot.
[0054] ·Sandbox technology
[0055] Sandbox technology, English name sandbox. This technology is now used in computer se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com