Network terminal management method
A management method and network terminal technology, applied in the field of network terminal management, can solve the problems of inaccessible terminal control and high management costs, and achieve the effects of accurate blocking and release, ensuring safety, and saving costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
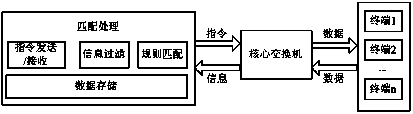
[0036] like figure 1 As shown, the working principle of the network terminal management method of the present invention is to store IP / MAC / PORT information and matching rules in the network, send instructions to the core switch, obtain switch information, perform matching processing, and send instructions to the core switch for management according to the matching results The switch port manages the network terminals connected to the switch through the core switch.
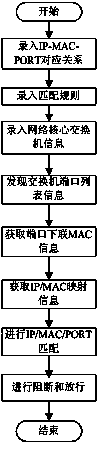
[0037] like figure 2 , image 3 As shown, the steps of network terminal management are: 1) Import IP / MAC / PORT information through EXCEL / XML / TXT files, and manually edit and manage; 2) Set the matching rule as: IP-MAC-PORT complete match; 3 ) Manually edit the core switch subnet IP address, subnet mask, and read community word to be discovered, and obtain the core switch information through SNMP; obtain the core switch port list through SNMP; 4) obtain the downlink MAC address of the core switch port through ...
specific Embodiment approach 2
[0042] like figure 2 , image 3 As shown, the steps of network terminal management are: 1) Import IP / MAC / PORT information through EXCEL / XML / TXT files, and manually edit and manage, where PORT is the port name; 2) Set the matching rule as: IP-MAC -PORT complete match; 3) Manually edit the IP address of the core switch, Telnet port number, Telnet user name, Telnet password, operation command prompt, privileged mode command, privileged password, and privileged command prompt; 4) Obtain the core through Telnet Switch port downlink MAC address information; 5) Obtain the corresponding relationship between IP address and MAC through Telnet; 6) Obtain the set matching rules and obtain the set matching information; 7) For all the obtained IP, MAC, and PORT, according to the matching The rules are compared with the set matching information. If the matching information conforms to the setting, the matching is successful, and the release mark is carried out; if the matching information...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com