Method for realizing L2TP user access backup and network system
A technology for accessing networks and users, which is applied in the field of data communication, and can solve problems such as complex implementation, not supporting L2TP user access backup, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
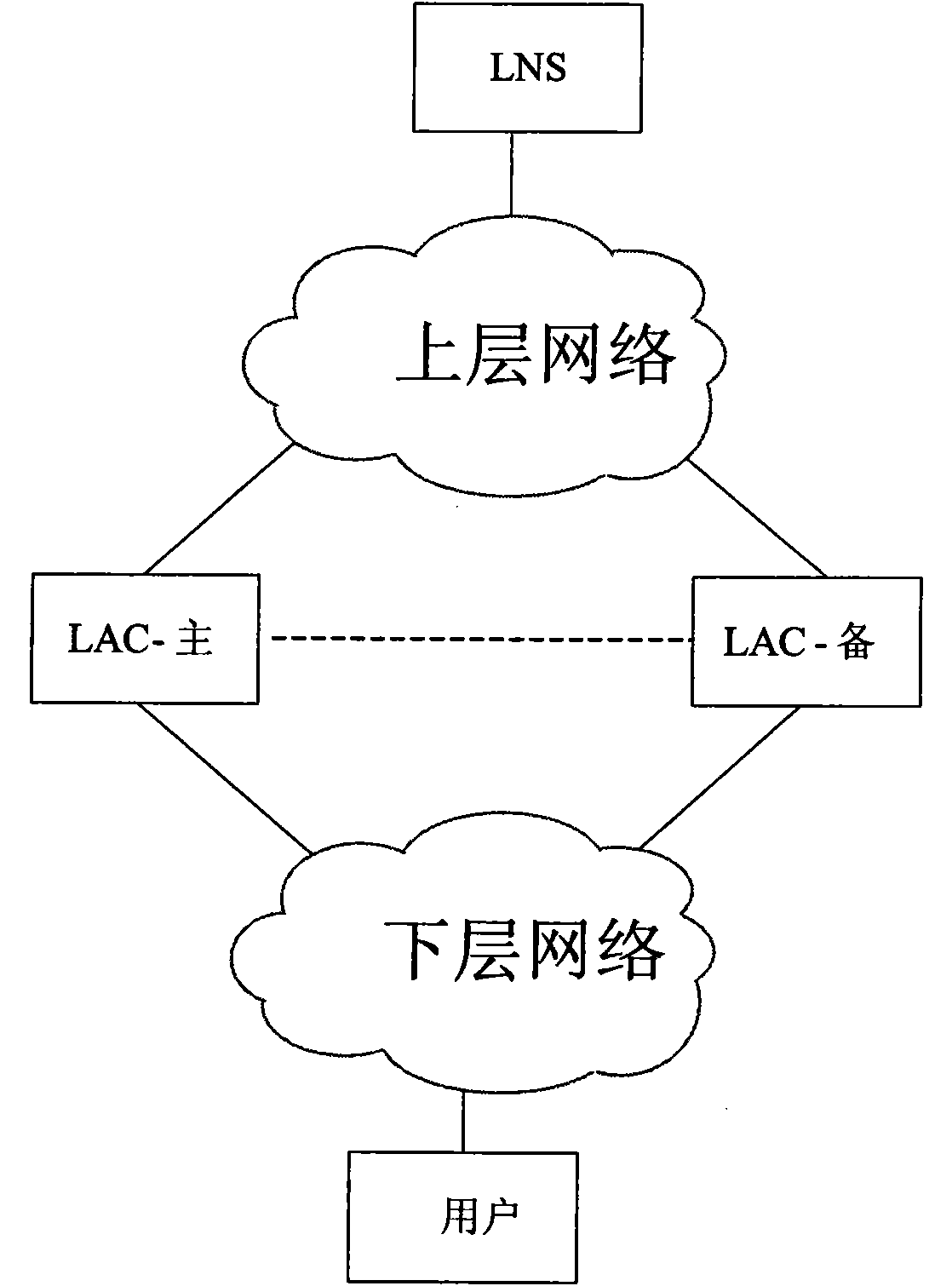
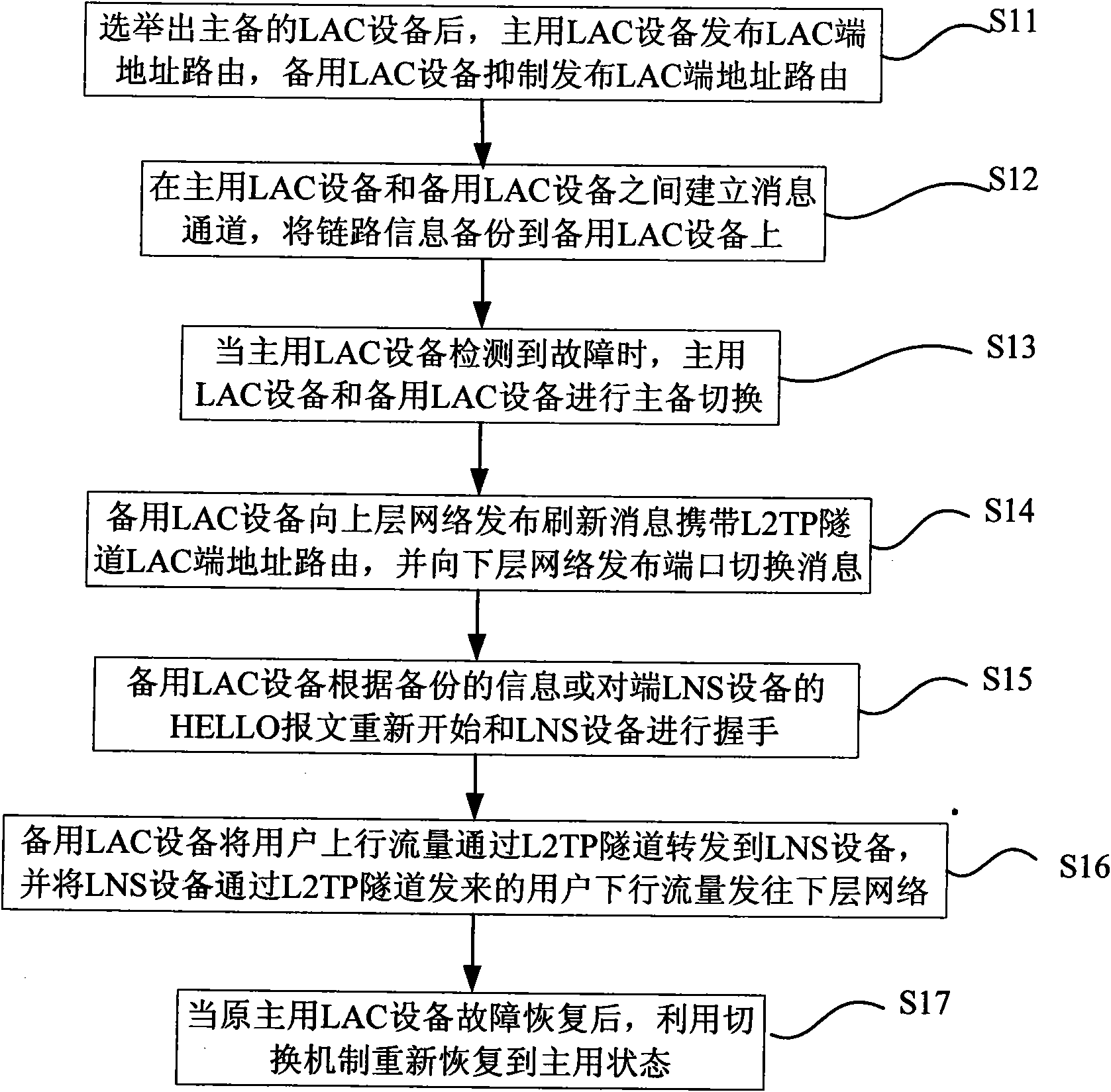
[0075] The BFD protocol is used to detect the link status between the two LAC devices, and VRRP is used to switch the active and standby status of the LAC device to realize L2TP user backup. This method implements L2TP user access backup. Among them, LAC1 is the active device, and LAC2 is the backup device.
[0076] Step A1, establishing a TCP (Transmission Control Protocol, Transmission Control Protocol) connection between LAC1 and LAC2 as a message channel for backing up online L2TP user information and corresponding L2TP tunnel information and L2TP session information;
[0077] Step B1, running the BFD protocol on the active and standby LAC devices respectively to detect the network connectivity between the active and standby LAC devices, between the LAC1 device and the lower network, and between the LAC2 device and the lower network;
[0078] Step C1, run VRRP between LAC1 and LAC2, and associate with the corresponding downlink state;
[0079] Step D1, configure LAC2 on ...
Embodiment 2
[0086]The BFD protocol is used to detect the link state between two LAC devices, and the LAC device state is switched by VRRP to realize L2TP user backup. The HELLO message of the switched LAC is generated according to the backup Ns and Nr information to realize the L2TP user Access backup. Among them, LAC1 is the active device, and LAC2 is the backup device.
[0087] Step A2, establish a TCP connection between LAC1 and LAC2 as a message channel to back up the information of the online L2TP user and the corresponding L2TP tunnel information, L2TP session information, and the Ns and Ns of the HELLO message sent by each L2TP tunnel LAC1 Nr information;
[0088] Step B2, running the BFD protocol on the active and standby LAC devices respectively to detect the network connectivity between the active and standby LAC devices, between the LAC1 device and the lower network, and between the LAC2 device and the lower network;
[0089] Step C2, run VRRP2 between LAC1 and LAC2, and asso...
Embodiment 3
[0097] Three LAC devices, among which LAC1 and LAC2 are the main devices, and LAC3 is the backup device. The Ethernet OAM protocol mechanism is run between LAC1 and LAC3, and between LAC2 and LAC3 for link status detection. At the same time, VRRP (Virtual Router Redundancy Protocol, Virtual Router Redundancy Protocol) performs LAC device state switching, realizing the function of using one LAC device to back up L2TP users for multiple LAC devices.
[0098] Step A3, establishing a TCP connection between LAC1 and LAC3, and between LAC2 and LAC3 as a message channel for backing up online L2TP user information and corresponding L2TP tunnel information and L2TP session information;
[0099] Step B3, respectively run the Ethernet OAM protocol on the three LAC devices to detect connections between LAC1 and LAC3, between LAC2 and LAC3, between LAC1 and the lower network, between LAC2 and the lower network, and between LAC3 and the lower network network connectivity;
[0100] Step C3,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com