Method and system for preventing illegal terminal from accessing as well as terminal
An illegal terminal and terminal access technology, applied in transmission systems, electrical components, wireless communications, etc., can solve the problems of MTCServer information security hidden dangers, illegal intrusion, etc., to prevent malicious theft and ensure security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0079] The technical scheme of the present invention will be described in further detail below in conjunction with the accompanying drawings and specific examples, so that those skilled in the art can better understand the present invention and implement it, but the examples given are not intended to limit the present invention .
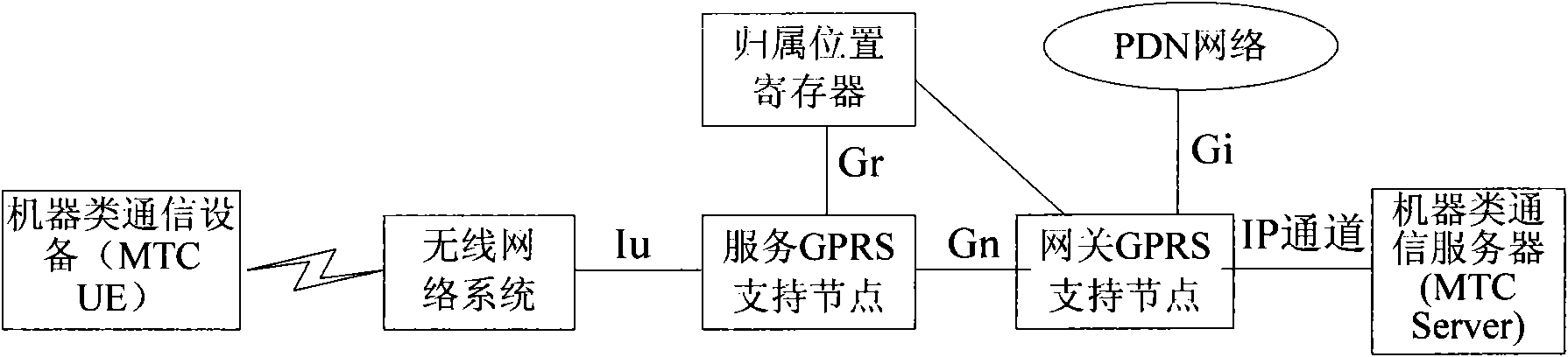
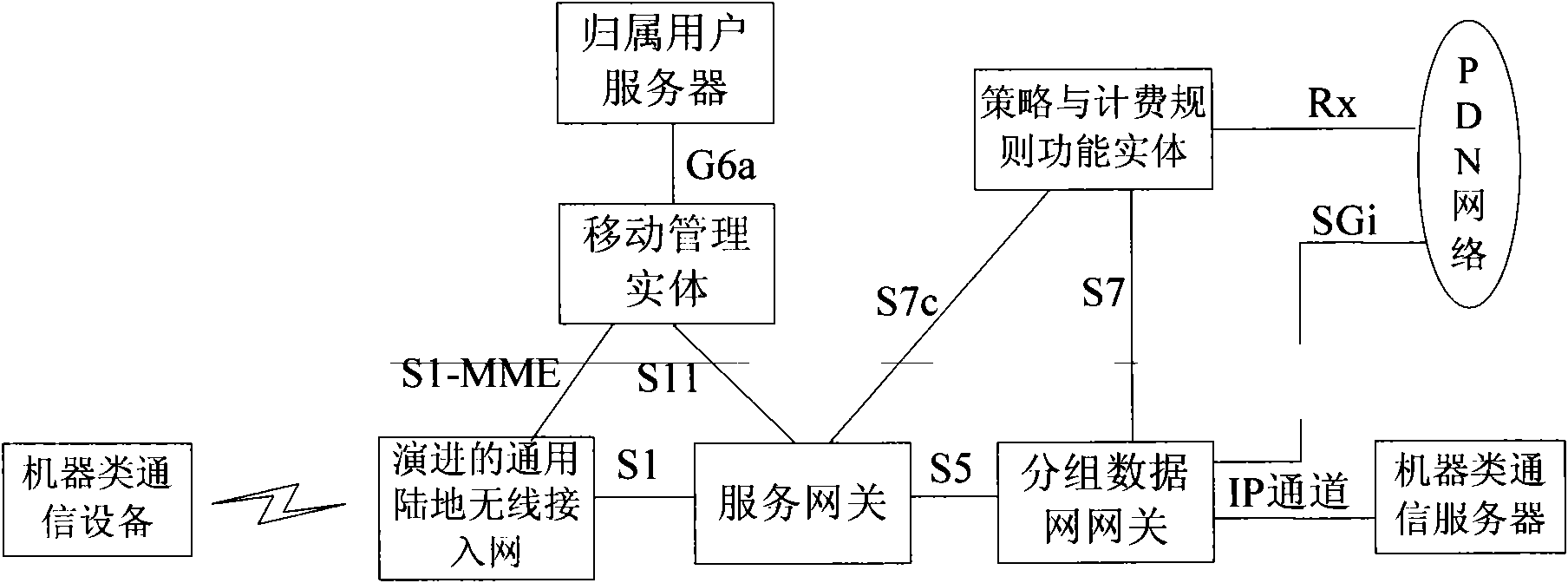
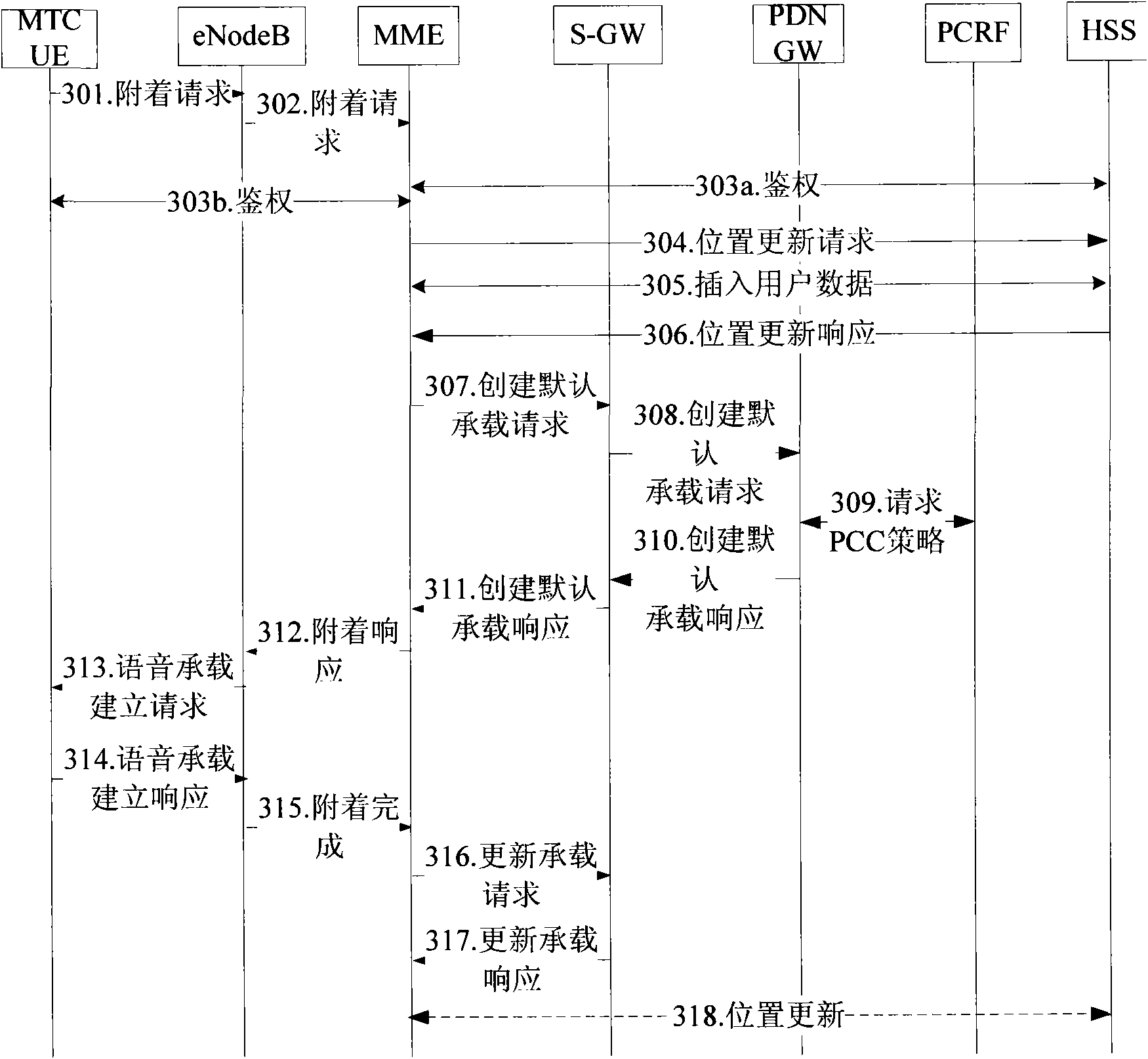
[0080] In the present invention, the terminal needs to carry device-related information, such as device type information, indicating whether the device is a machine-type device or a mobile phone-type device; or device access capability information, indicating whether the device has a machine-type access capability or a mobile phone-type access capability . After the SGSN / MME downloads the user subscription data from the user database, it can determine whether it is a machine type subscription or a mobile phone type subscription according to the user subscription data. There are many ways to judge, for example, you can sign up for M2M access capabil...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com