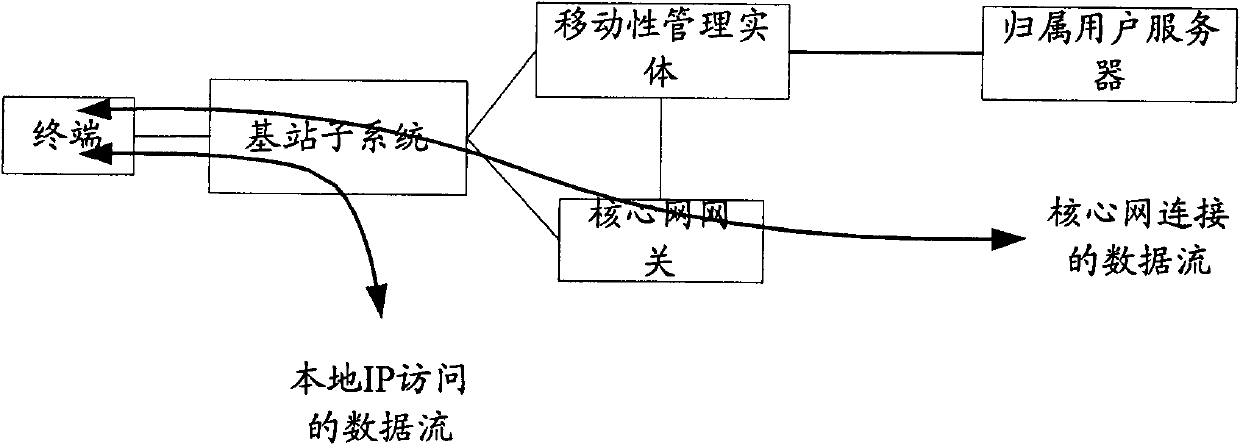
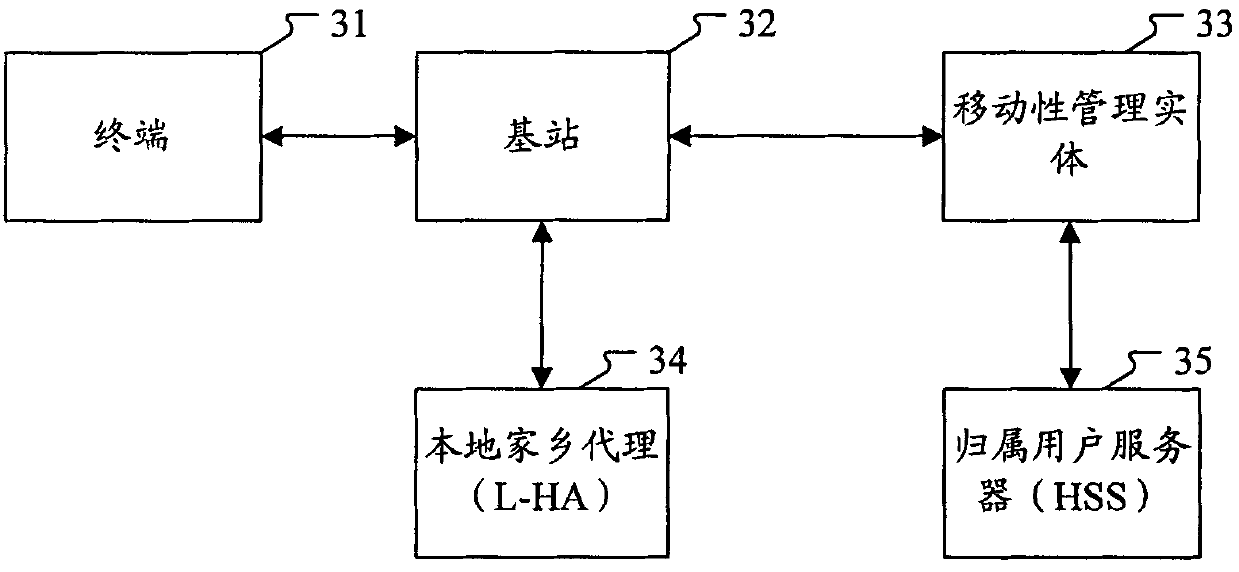
Local IP access method and system
An access method and local technology, applied in connection management, wireless network protocols, electrical components, etc., can solve problems such as service interruption and affect user experience, and achieve the effect of avoiding service interruption and improving user experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0112] In this embodiment, the user attach process is described, the base station is HeNB, and the mobility management entity is MME.
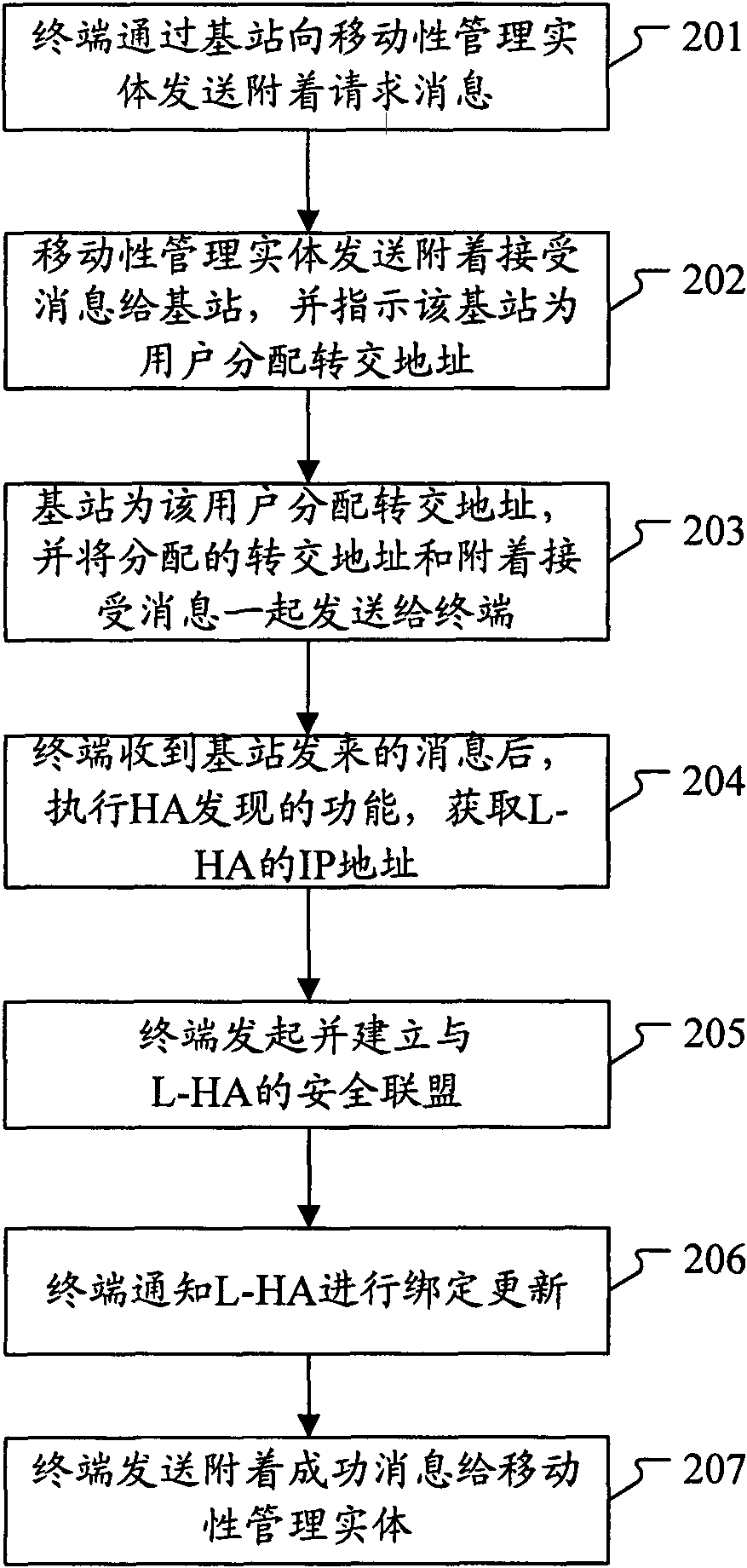
[0113] Figure 4 It is a schematic diagram of the user attachment process of the local IP connection in Embodiment 1 of the present invention, such as Figure 4 As shown, in Embodiment 1, the terminal is attached to the network, and establishing a LIPA connection generally includes the following steps:
[0114] Step 401: the terminal sends an attach request message to the MME through the HeNB.
[0115] The attachment request message generally carries the user's willingness: local IP access and use of mobile IP.
[0116] Step 402: the MME initiates authentication of the user, and verifies the legal identity of the user.
[0117] During this process, the HSS needs to generate relevant authentication vectors and send them to the MME, and the user needs to provide a valid identity. This step is optional.
[0118] Step 403: When the MME has no...
Embodiment 2
[0135] Figure 5 It is a schematic diagram of the user switching process of the local IP connection in Embodiment 2 of the present invention, such as Figure 5 As shown, the user switching process of the local IP connection in Embodiment 2 generally includes the following steps:
[0136] Step 501: The terminal establishes a LIPA connection for accessing an external network through a source base station.
[0137] Here, the specific access process is the same as that described in Embodiment 1.
[0138] Step 502: The source base station receives the radio signal measurement report provided by the terminal, decides to handover the user to the target base station, and sends a handover request to the source mobility management entity.
[0139] The handover request generally carries the identifier of the target base station and an indication of the allocated care-of address. In this embodiment, the mobility management entities are all MMEs.
[0140] Step 503: The source mobility ...
Embodiment 3
[0152] Figure 6 It is a schematic diagram of the local IP connection process flow diagram for the deactivation of the user of the local IP connection in Embodiment 3 of the present invention, such as Figure 6 As shown, the user deactivation of the local IP connection in Embodiment 3 of the present invention generally includes the following steps:
[0153] Step 601: The terminal decides to deactivate the local IP connection, and sends a binding update message to the L-HA, which carries a lifetime (lifetime) of zero.
[0154] Step 602: The L-HA deletes the binding relationship between the user's care-of address and the home address, and sends a binding confirmation message to the terminal.
[0155] Step 603: The terminal or L-HA initiates and deletes the security association.
[0156] This step is optional. If you do not delete in this process, you can wait for the SA lifetime to expire, and then delete the terminals and L-HA locally.
[0157] Step 604: The terminal sends ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com