Two-level policy decision-based access control method and system
A policy decision-making and access control technology, applied in the field of access control in information security, can solve problems such as the impact of SAAM versatility, and achieve the effect of ensuring versatility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
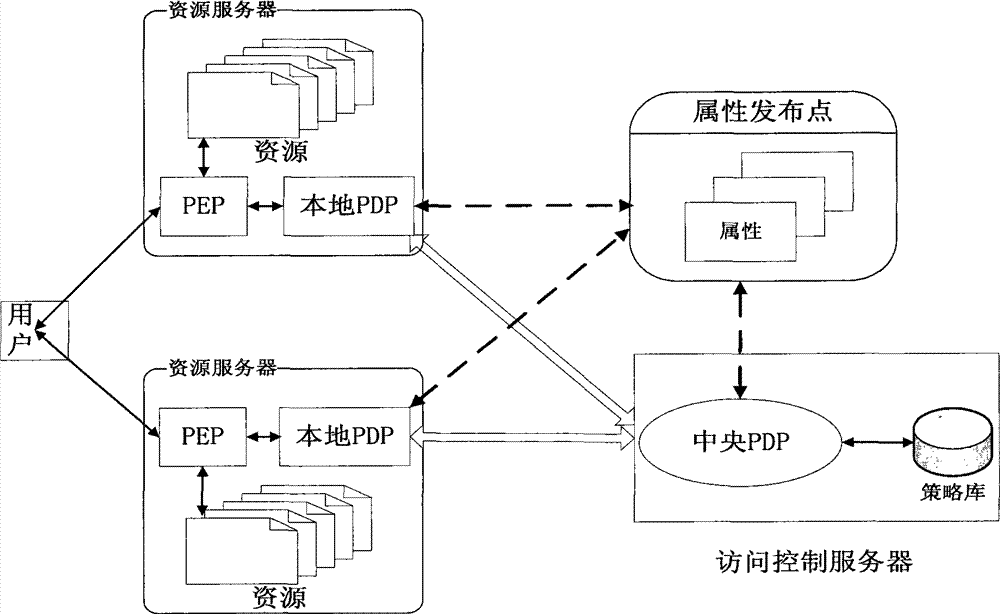
[0052] Below by example the present invention is described in more detail.
[0053] Such as figure 2 As shown, it is assumed that the PEP and local PDP in the access control system are deployed on the resource server (that is, at first a PEP and local PDP will be deployed on each resource server, and the local PDP deployed together with the PEP is the first level), The central PDP is deployed on the policy decision server (that is, the central PDP is the second level), the resource server is physically separated from the policy decision server, and the resource server has a certain computing power; the resource server is physically separated from the policy decision server Yes, over a network connection. When the user is authenticated and initiates an access request to the protected resources stored on the resource server, the execution flow of the access control system based on two-level policy decisions is as follows:
[0054] 1. After the PEP intercepts the user's access...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com