Method for safely accessing mobile credible terminal
A technology of terminal security and access method, applied in the field of trusted access, to prevent leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
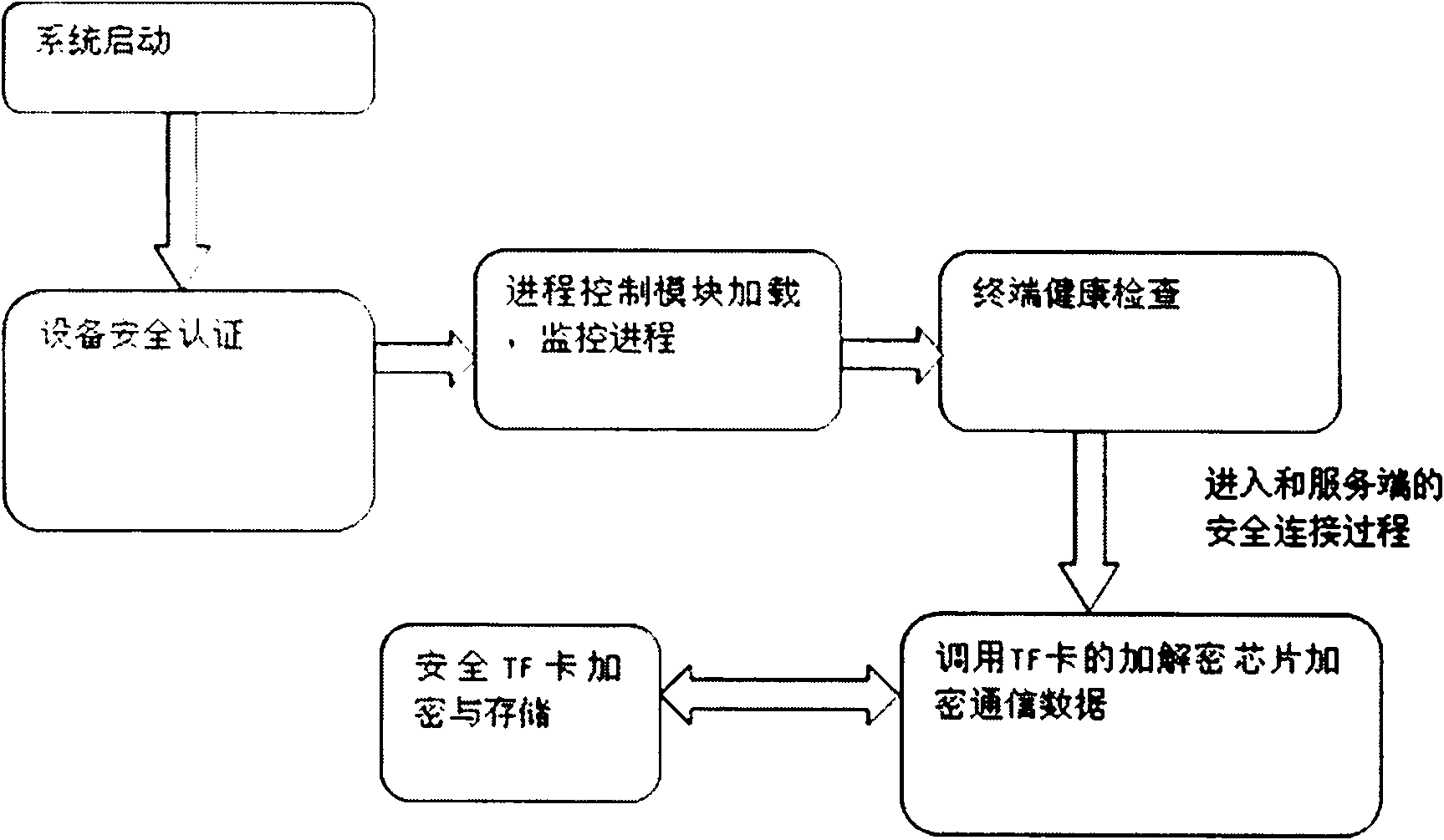
[0024] combine here figure 1 and figure 2 Describe the startup process and access server process of the mobile trusted terminal:
[0025] The user activates the mobile terminal through means such as password or fingerprint authentication.
[0026] The terminal loads the operating system and checks whether the operating system image has been changed to ensure safe startup.
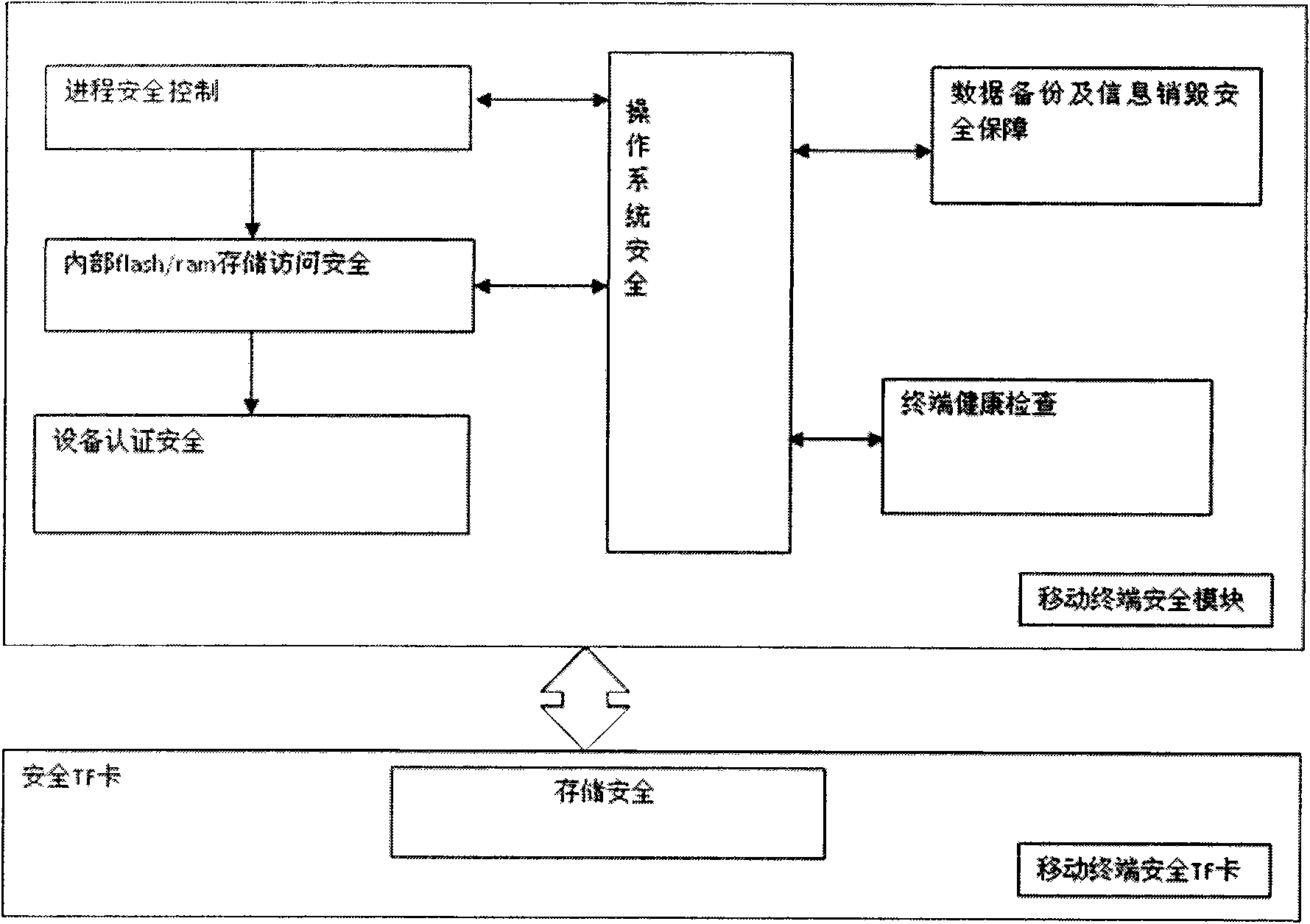
[0027] The process monitoring module solidified in ROM starts and loads to monitor other processes and module loading, and then checks the security of TF to decide whether to continue to start or stop.
[0028] After the terminal is started, before preparing to establish a secure connection with the server, start the terminal health check module, check the hardware information of the terminal, and perform a security scan, and prepare to submit the extracted information and security scan results to the server for further analysis.
[0029] The terminal checks the digital certificate in the secure TF memo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com