Trusted improvement method of router
A router and trusted technology, applied in the field of communication security of IP networks, can solve the problems of no trust management infrastructure and trust management technology remaining in modeling and optimization.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
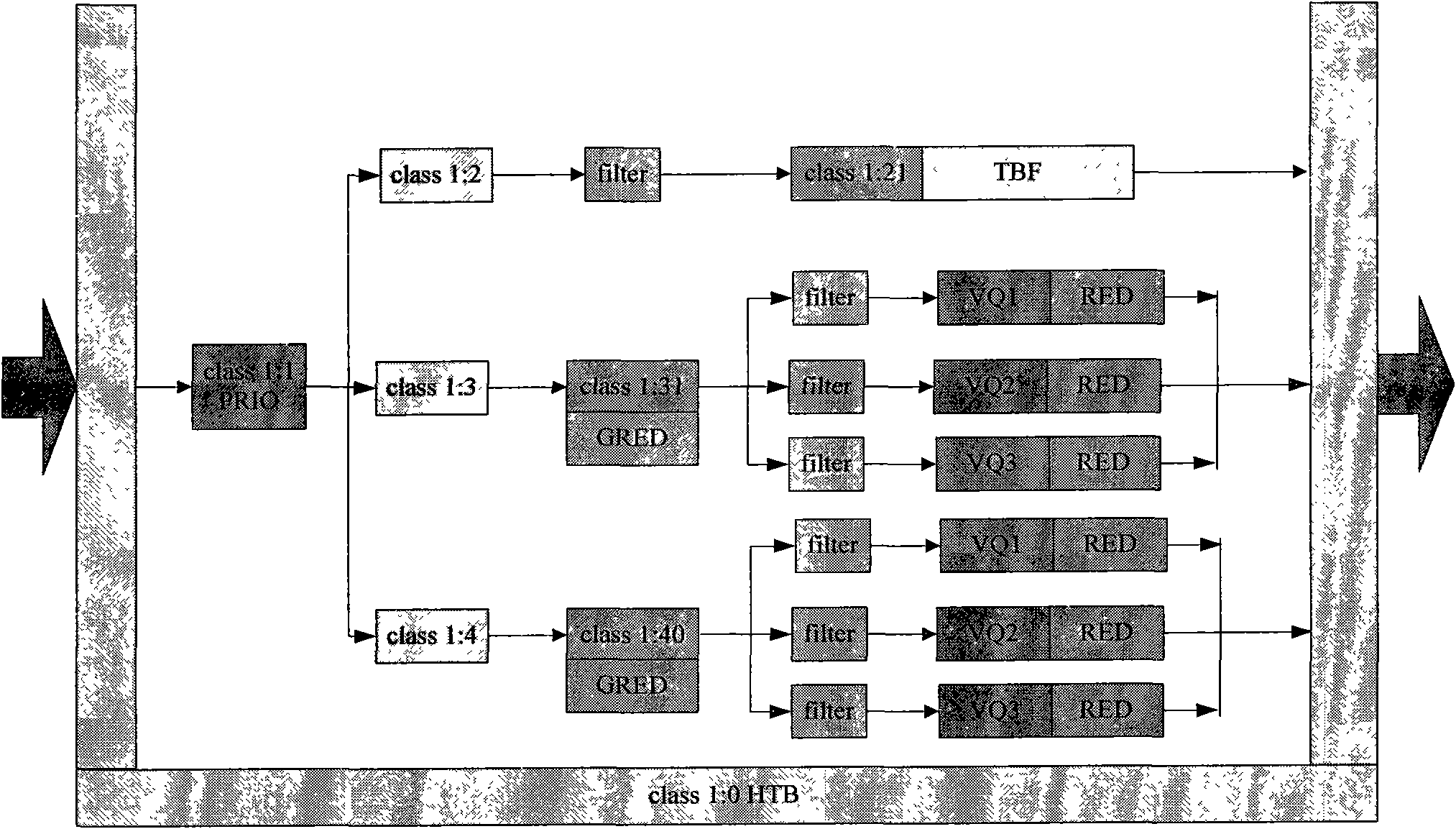
Image
Examples
Embodiment Construction
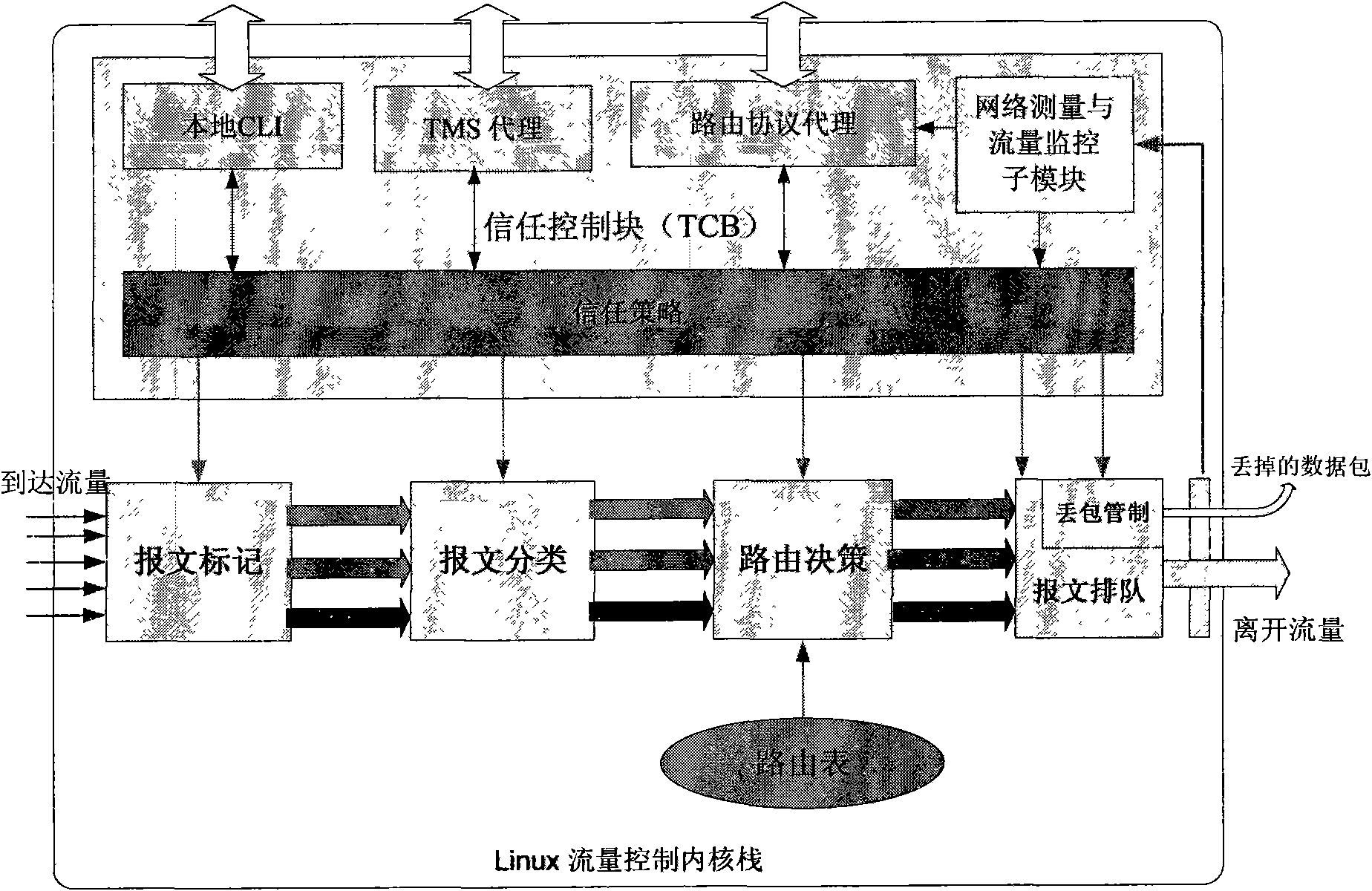
[0018] attached figure 1 It is an overall structure diagram of the present invention. The network measurement and traffic monitoring submodule of the trust control block (TCB) part is mainly aimed at routers that establish an adjacency relationship with this router, and the parameters mainly include: end-to-end reachability, end-to-end delay, end-to-end loss Packet rate, throughput rate, link traffic, etc. These parameters are obtained by using the fping tool, ntop, and the IP statistics function provided by linux itself. After obtaining these parameters, the router keeps a copy locally, and regularly uploads it to TMS for TMS and neighbor routers of this router to use when needed.
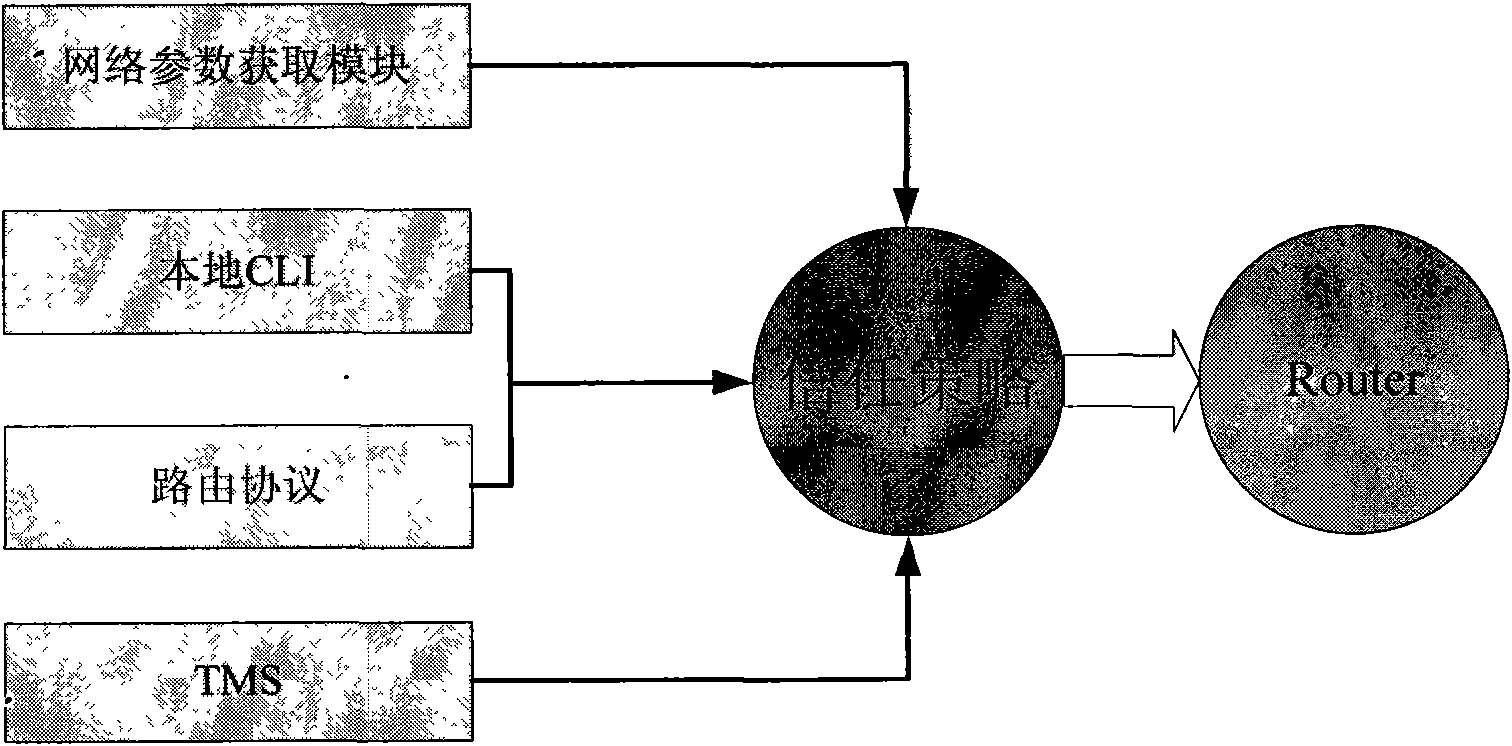
[0019] attached figure 2 is the trust policy formation diagram of the present invention. The trust policy of the trust control block is used to issue a specific routing policy to the trusted router to instruct it to perform flow control and routing. It is mainly based on the source of the da...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com