Virtual leased line network service protection method and operator edge device
A technology for operator edge and service protection, applied in the field of communications, it can solve the problems of asynchrony and inability to know the status of access links, and achieve the effect of improving utilization and ensuring synchronization.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be described in detail below with reference to the accompanying drawings and specific embodiments.
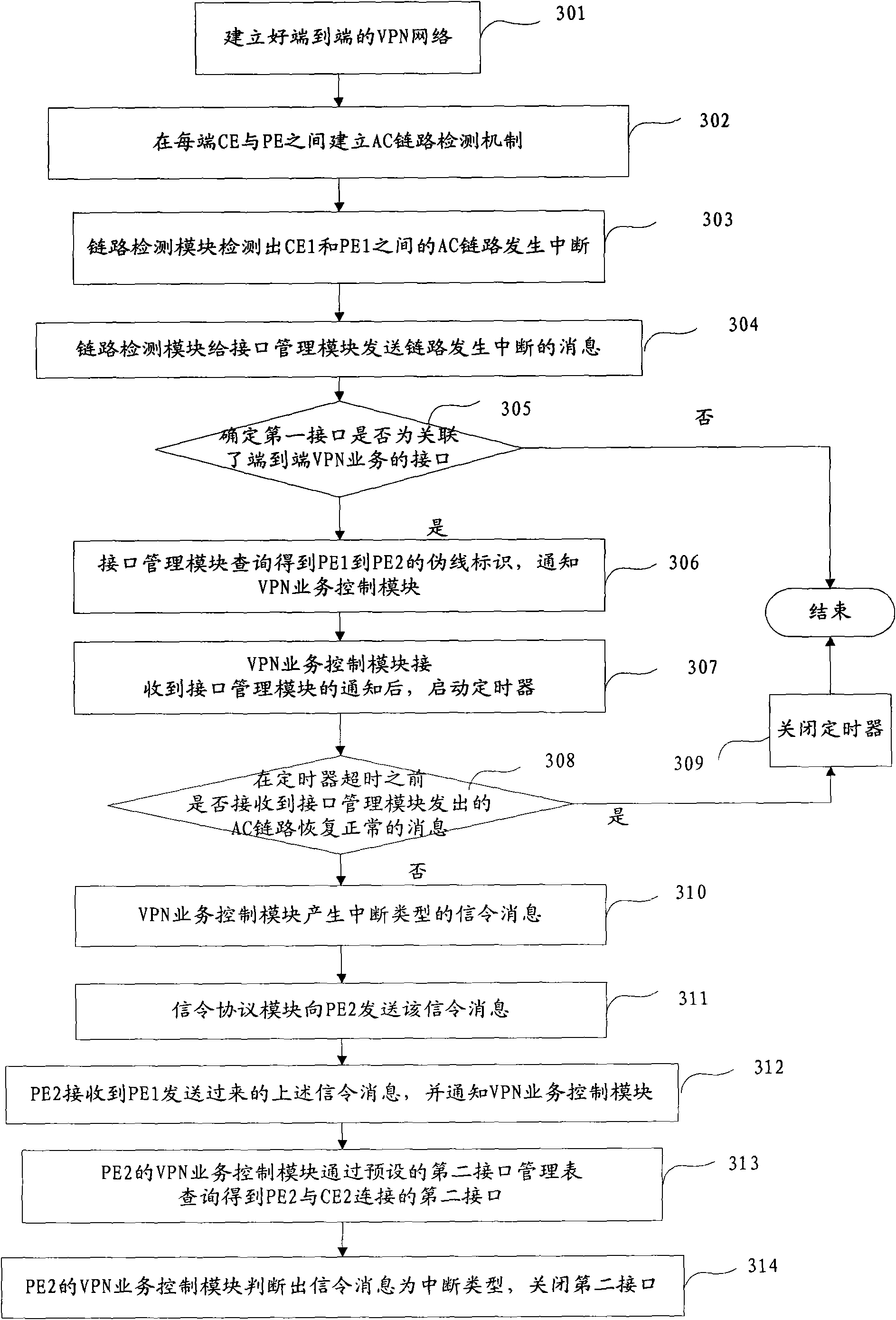
[0050] figure 2 It is a schematic flowchart of a method for protecting virtual leased line network services according to an embodiment of the present invention. Such as figure 2 , the method of this embodiment comprises the steps:
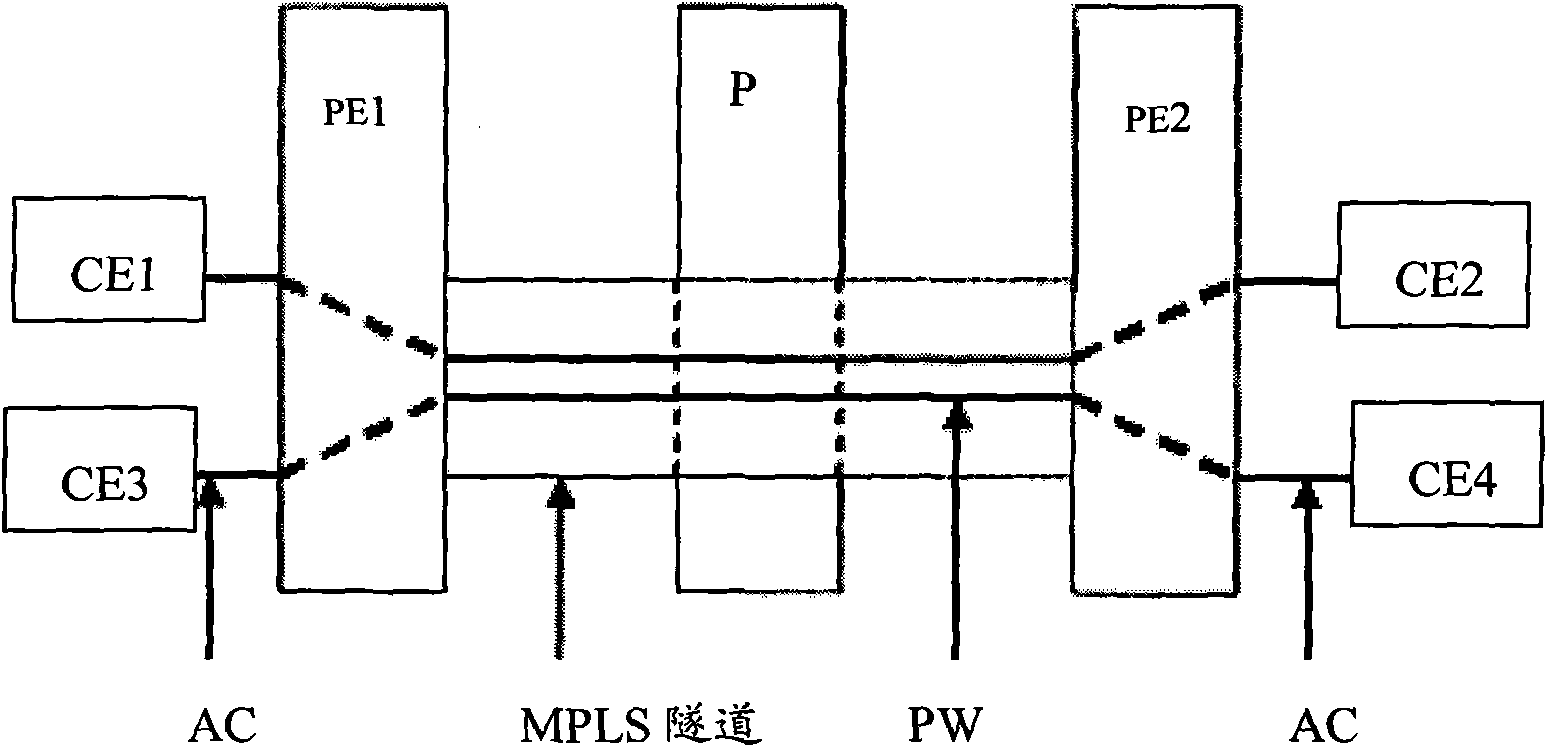
[0051] Step 201, the local operator edge device PE1 detects that the access link between PE1 and the local user edge device CE1 is interrupted;
[0052] Step 202, PE1 obtains the pseudowire identifier between PE1 and the remote operator's edge device PE2;
[0053] In this step, specifically, according to the preset first interface management table, PE1 determines that among the interfaces between PE1 and CE1, the first interface corresponding to the access link is associated with the end-to-end virtual private netwo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com