Theftproof method using network isolation transformer characteristics in network equipment
A technology of network isolation and network equipment, applied to anti-theft alarms, instruments, alarms, etc., can solve the problems of no anti-theft methods, etc., and achieve the effect of solving anti-theft problems, convenient installation, and powerful anti-destructive functions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] The specific implementation manner of the present invention will be described below in conjunction with the accompanying drawings.
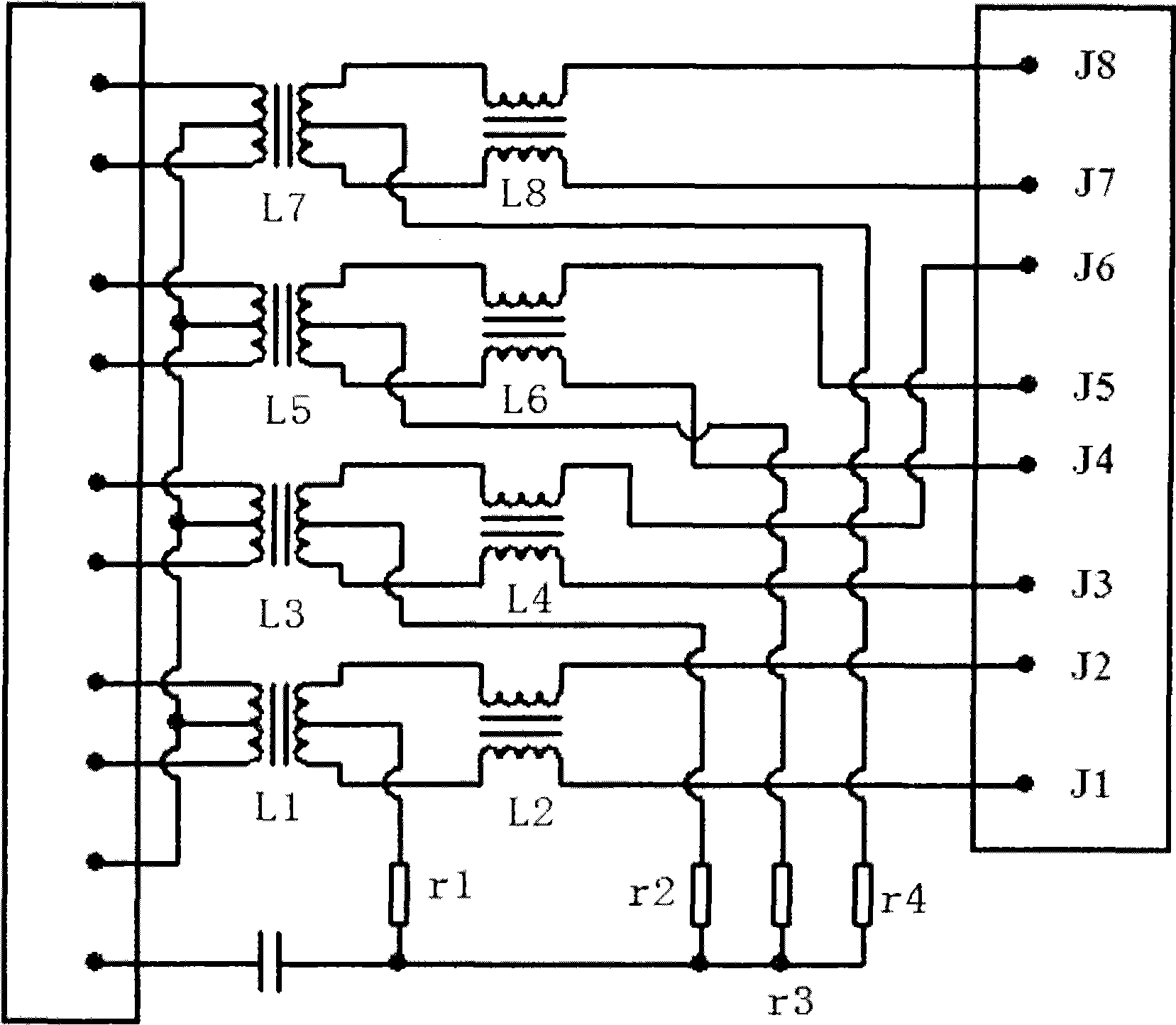
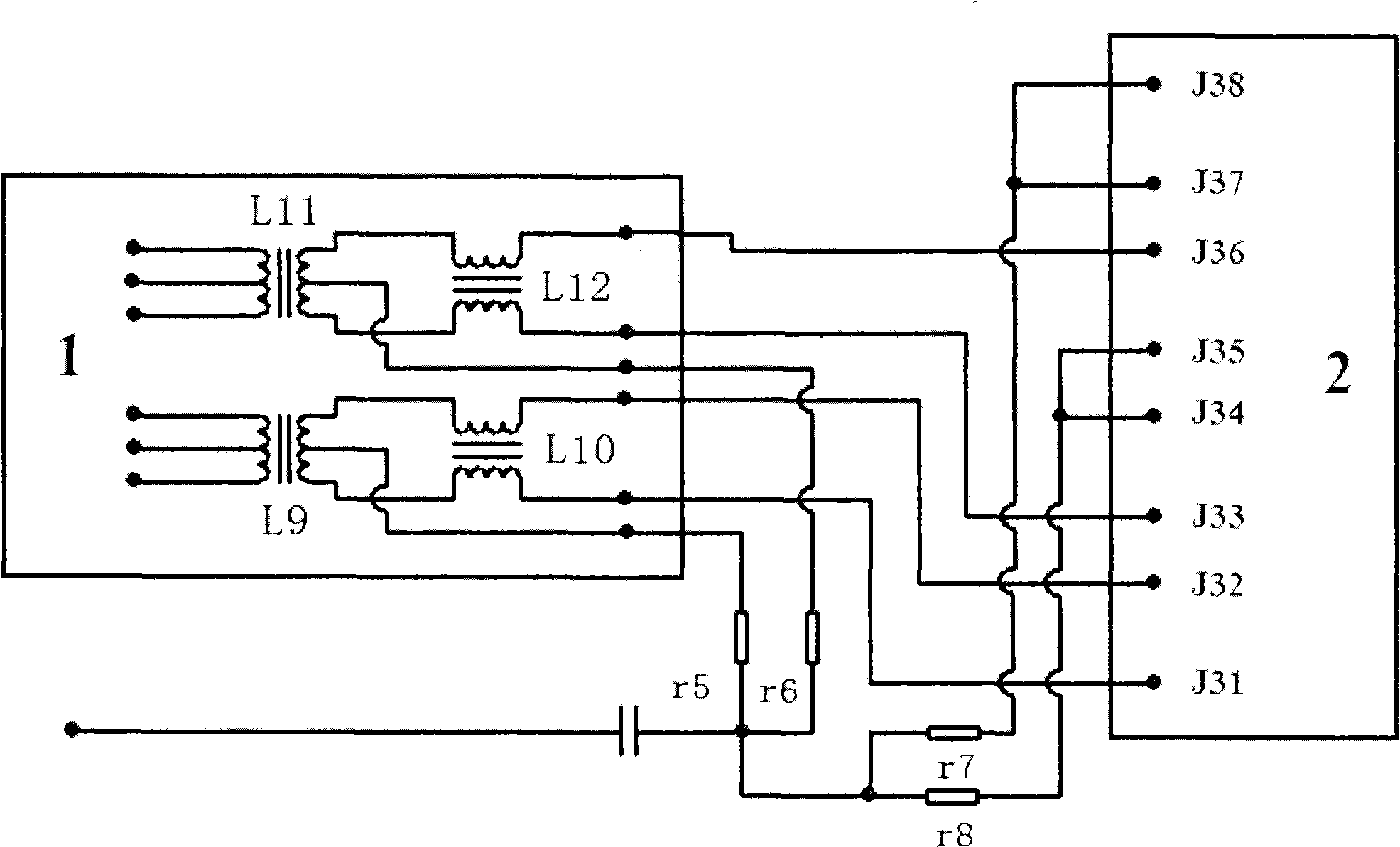
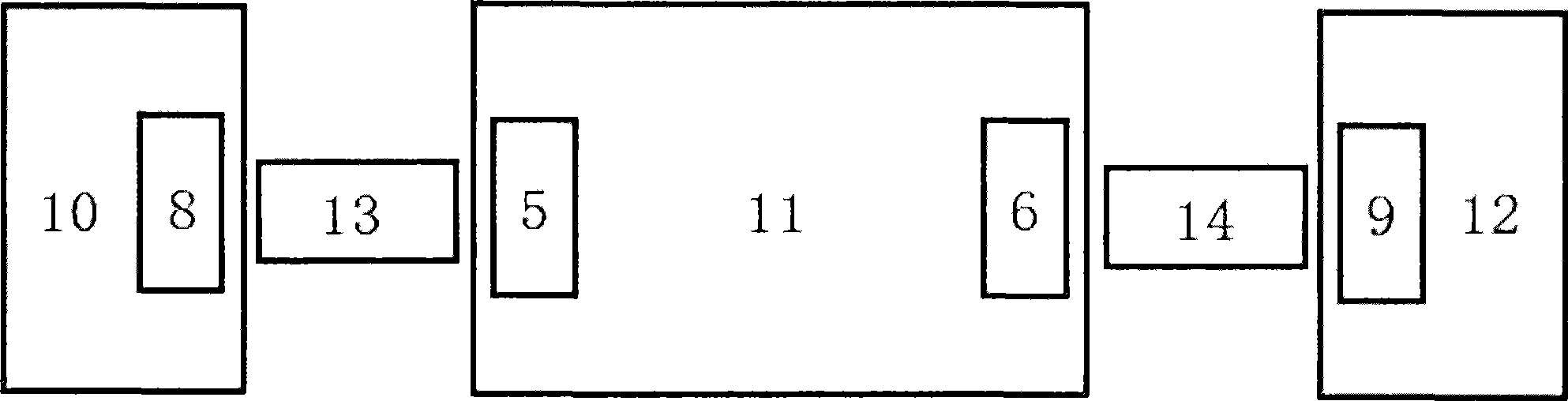
[0020] Such as figure 1 As shown in , it is a schematic diagram of a network isolation transformer included in the network port, and the network isolation transformer contains a resistor network inside. J1, J2, J3, J4, J5, J6, J7, and J8 are the pins of the network port with network isolation transformer. The network isolation transformer is also called the network transformer. It is a magnetic component that connects the Ethernet chip (10 / 100 / 1000) and the terminal network port (RJ45). Its main functions are signal transmission, impedance matching, waveform repair, Clutter suppression and high voltage isolation. The network isolation transformer and the network port can be two independent components, or an integrated component with a network isolation transformer in the network port. The internal circuits of different types of network ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com