Method for visual cryptography and counterfeit prevention of patterns
A visual encryption and pattern technology, applied in the field of anti-counterfeiting, can solve the problems of long development cycle, inconvenience for consumers, failure of anti-counterfeiting patterns, etc., and achieve the effect of low cost, easy identification and convenient production
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
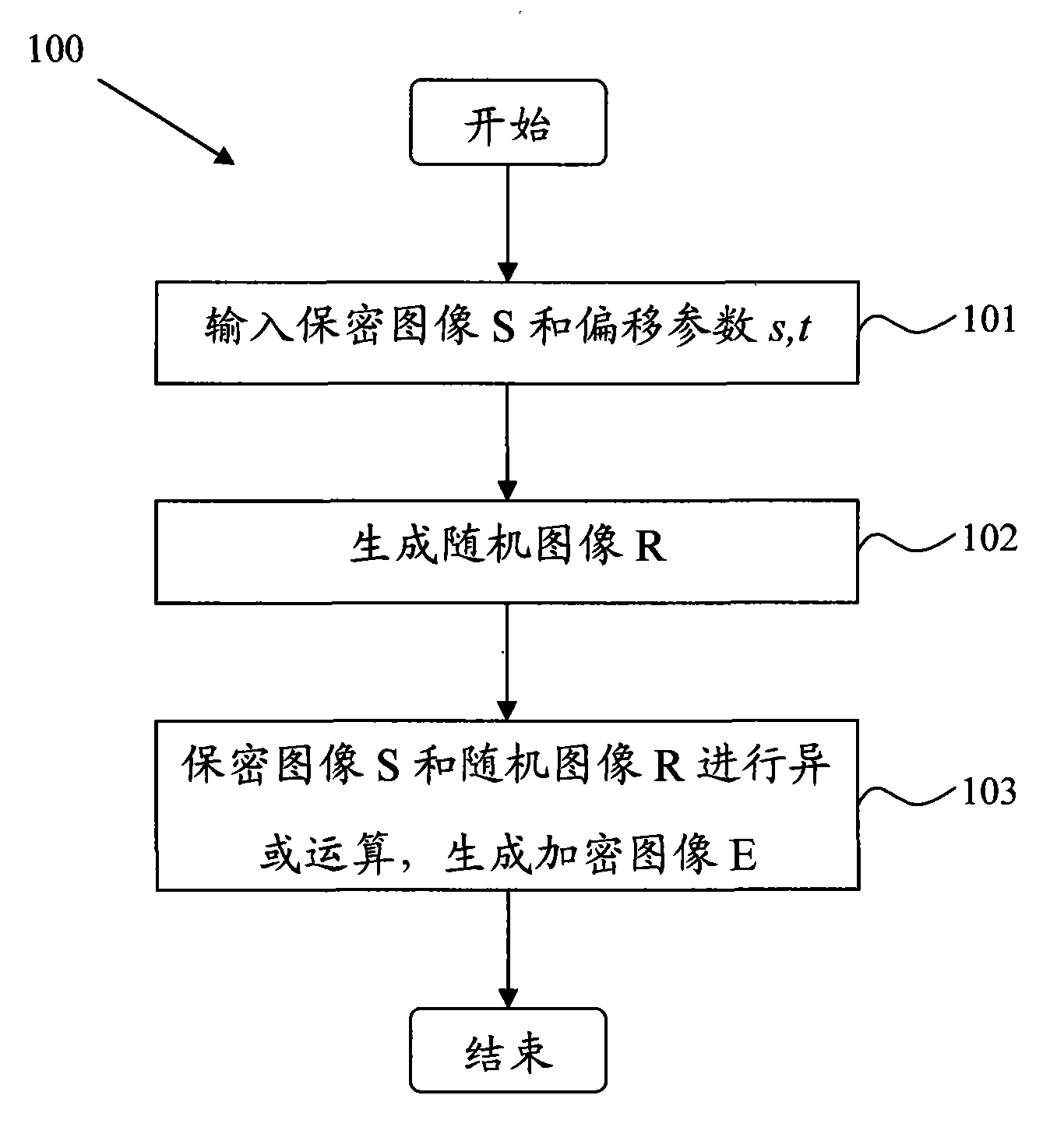
[0039] figure 1 A flow chart of a visual encryption anti-counterfeiting method 100 for generating a pattern of a second-order encrypted image E according to the first embodiment of the present invention is shown. Such as figure 1 As shown, first in step 101, generate (or input) a second-order secret image S with the size of row×col. The gray level of the secret image S is 2, that is, the secret image S has only two colors: black and white. The secret image S can be represented as a (row)×(col) matrix. The elements in this matrix are 0 and 1, where 0 represents a white pixel in the secret image S, and 1 represents a black pixel in the secret image S. According to another embodiment of the present invention, the security image S can be input from an image source (such as a memory or an image extraction device (such as a camera)), or can be directly generated by a machine or a human on demand.
[0040]And, in step 101, offset parameters s, t are determined (or input). Here, ...
Embodiment 2
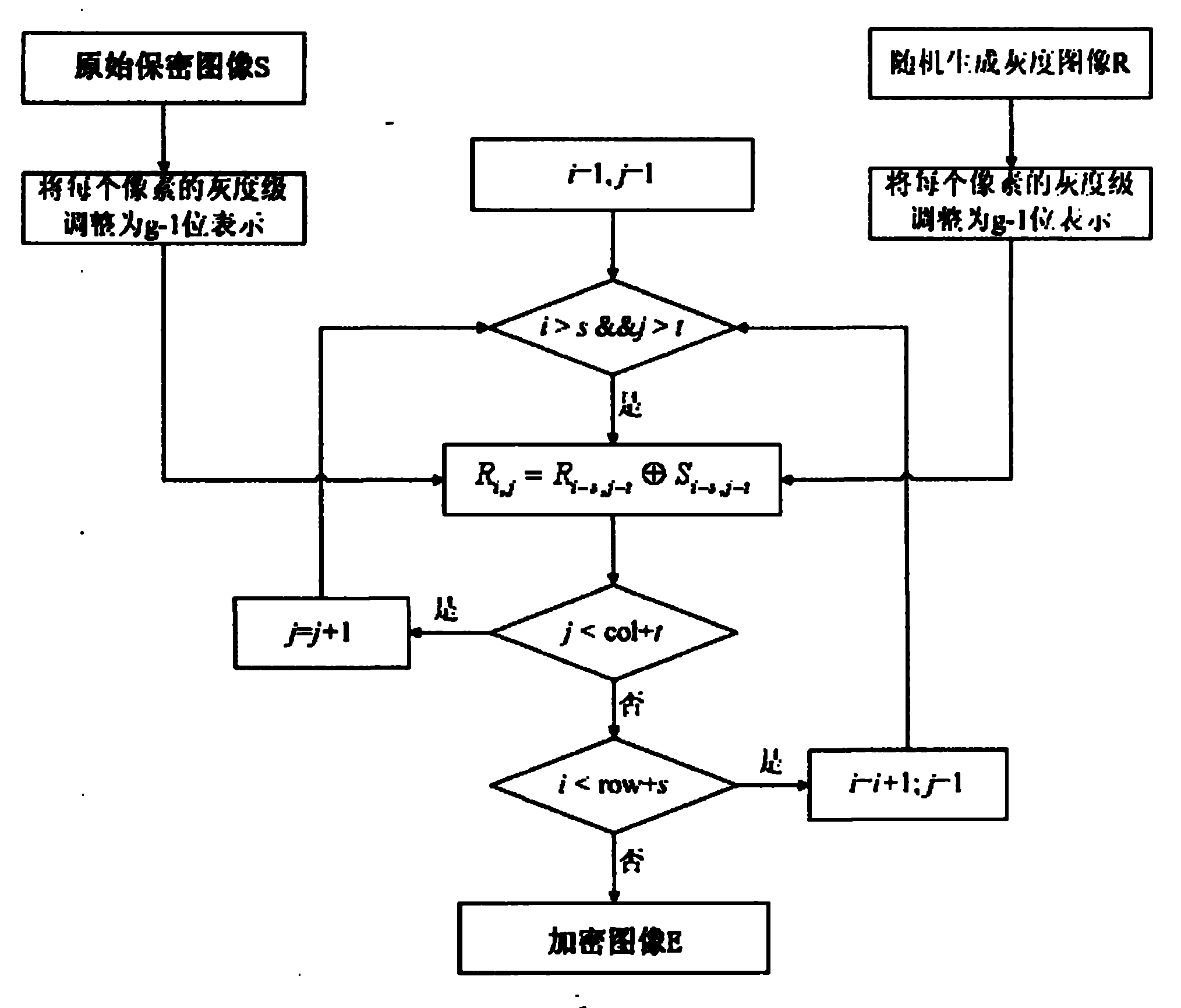
[0055] The computer program flow of the visual encryption anti-counterfeiting method for generating the pattern of the second-order encrypted image E according to the second embodiment of the present invention will be described below, wherein the offset parameters s=0, t=2. The computer program flow includes steps as follows:
[0056] Step 201: Obtain the following basic data: input a binary security image S, the security image has two colors, wherein 0 represents white pixels, 1 represents black pixels, the height (row) of the security image is 200, and the width (col) is 300; encrypt The image E is the offset s=0, t=2 required to restore the secret image S.
[0057] Step 202: Randomly generate a binary grayscale image R of 200×(300+2), wherein 0 represents a white pixel and 1 represents a black pixel;
[0058] Step 203: Starting from the third column in the random image R, process the elements in R column by column, let R(i, j) represent the pixel in row i and column j in R...
Embodiment 3
[0069] Figure 4 A specific encrypted image E realized according to the third embodiment of the present invention is shown. Such as Figure 4 As shown, the secret image S is a black and white binary image, the image size is 100×100, and the offset parameters s=12, t=12.
[0070] It can be seen that the logical XOR operation is performed by the secret image S and the random image R (such as image 3 shown) the obtained encrypted image E is only random black and white image information (such as Figure 4 In the shown encrypted image E), the original secret image S hidden in the encrypted image E cannot be distinguished from the naked eye. By overlapping the two encrypted images E, the original secret image S can be clearly restored. Since the encrypted image E has a good image hiding function, the anti-counterfeit element (such as a label, etc.) formed with the encrypted image E is difficult to be counterfeited, so that it can play a good anti-counterfeiting function.
[00...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com