Protection method for Gigabit passive optical network encryption service
A passive optical network, gigabit technology, applied in key distribution, which can solve the problems of ONU's failure to decrypt downlink data, lack of instructions and regulations, and out-of-sync keys.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
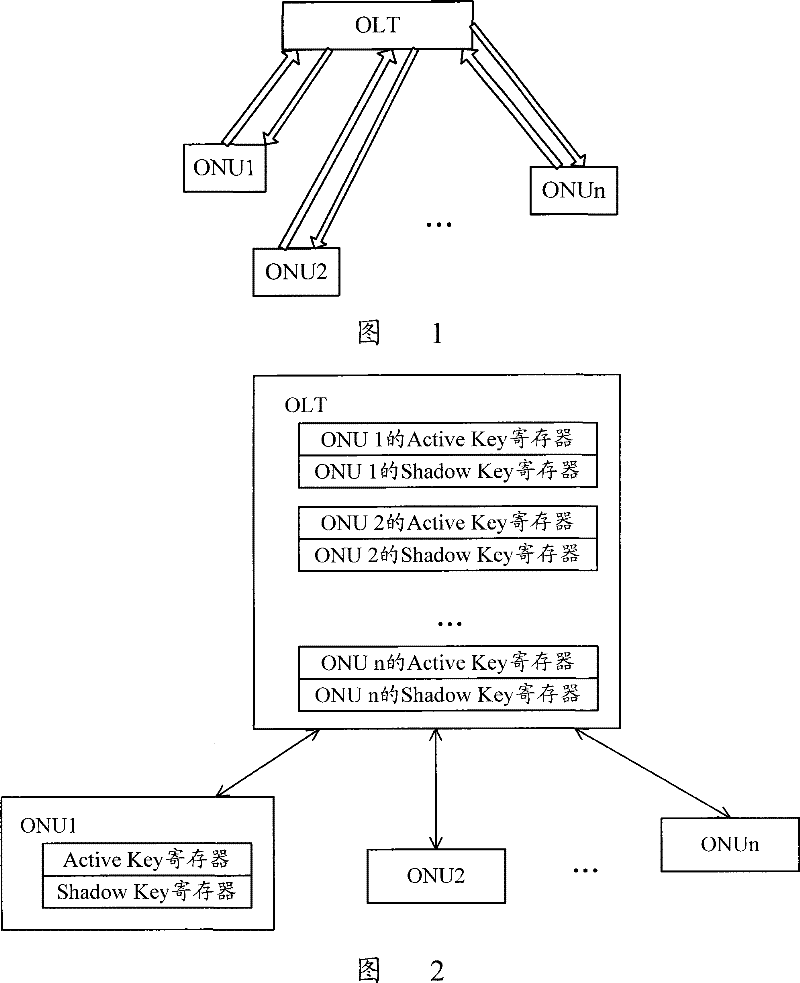
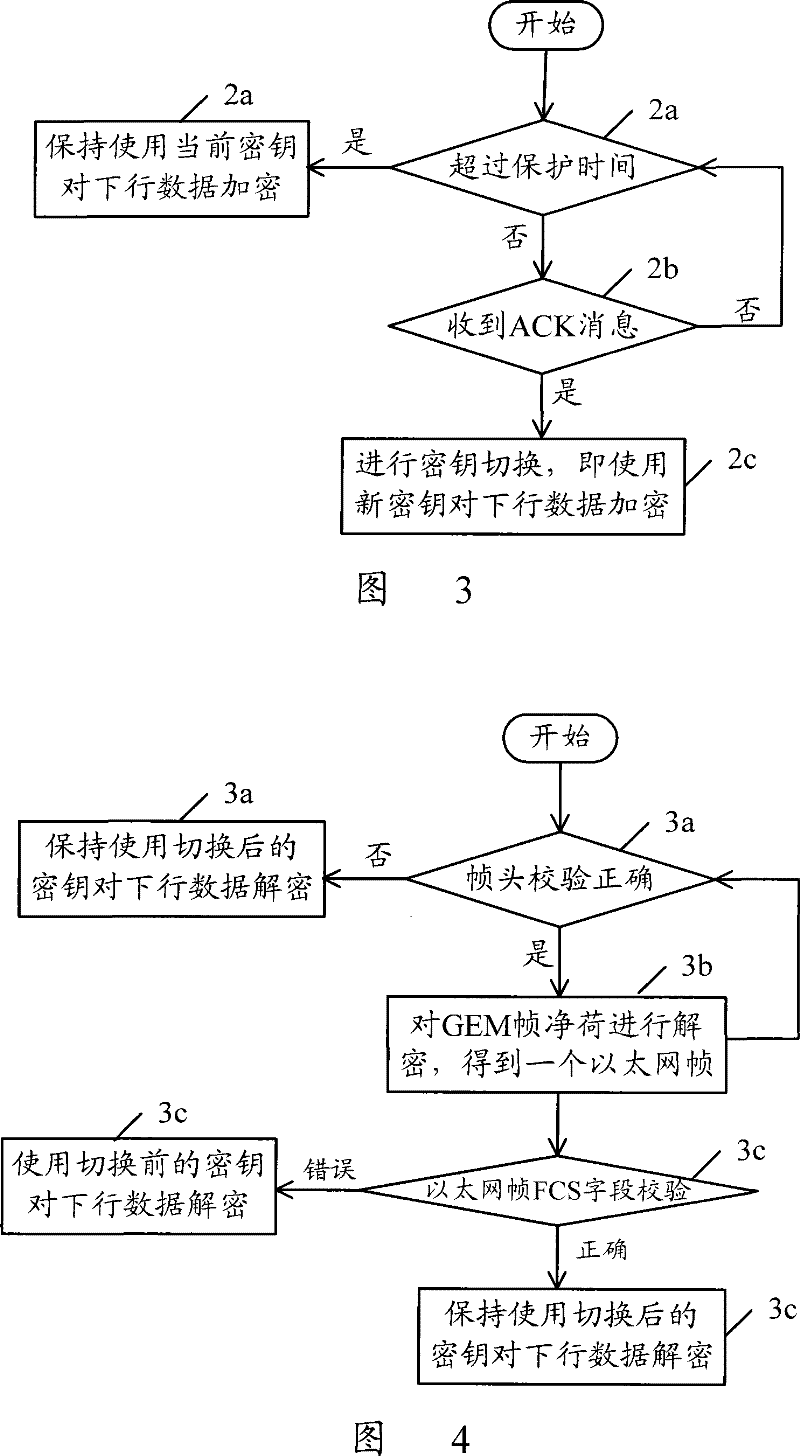
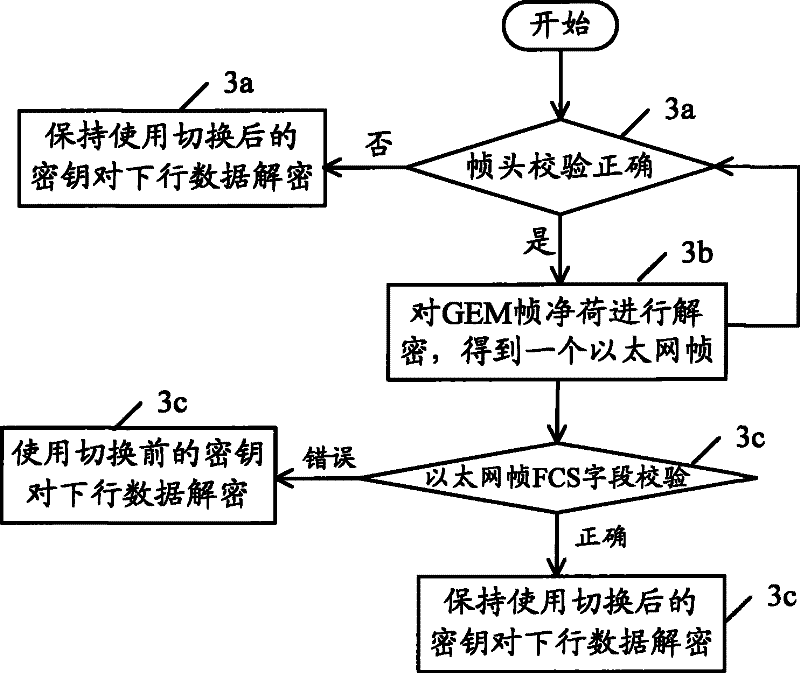
[0023] The basic idea of the present invention is: in the GPON system, after the OLT sends the Key_switching_time message to the ONU, and receives the Acknowledge message from the ONU, it is ready to switch the key; otherwise, it does not switch the key. After receiving the Key_switching_time message, the ONU performs key switching when the multiframe number of the message arrives. If the verification of the ATM cell header / GEM frame header is correct after switching, and the ATM cell payload / GEM frame payload is decrypted and corrected If there is an error in the verification, take protective measures by yourself: re-enable the key used before the key switch for decryption.
[0024] Utilize the flow process of GPON encryption service protection method of the present invention, comprise the following parts:
[0025] After the OLT sets the protection time and sends the key switching message to the ONU according to the procedure specified in G.984, the OLT determines whether t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com