Method and device for authorising conditional access
A technology for conditional access and authorization devices, applied in user identity/authority verification, electrical components, digital computer components, etc., can solve problems such as shutdown
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
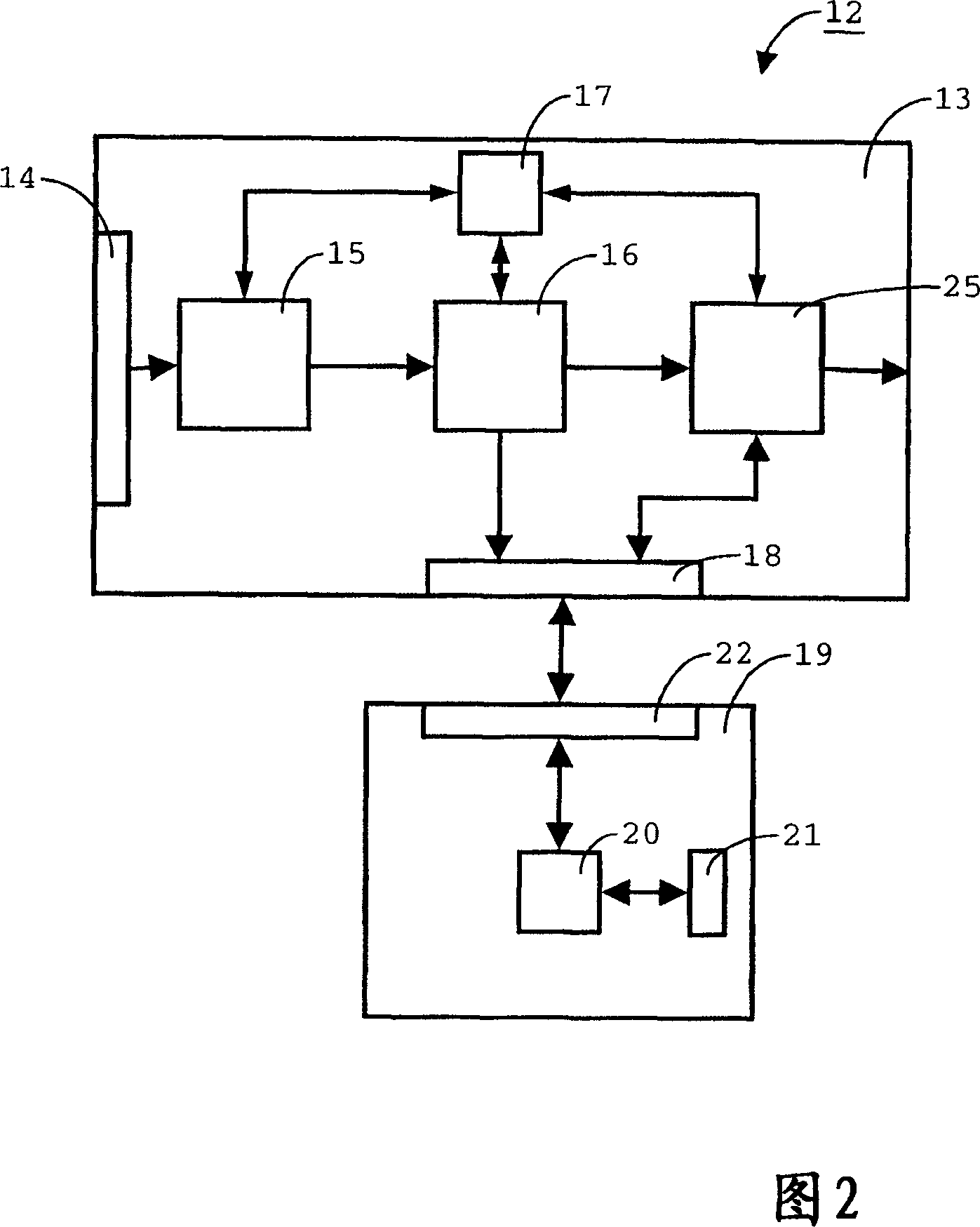
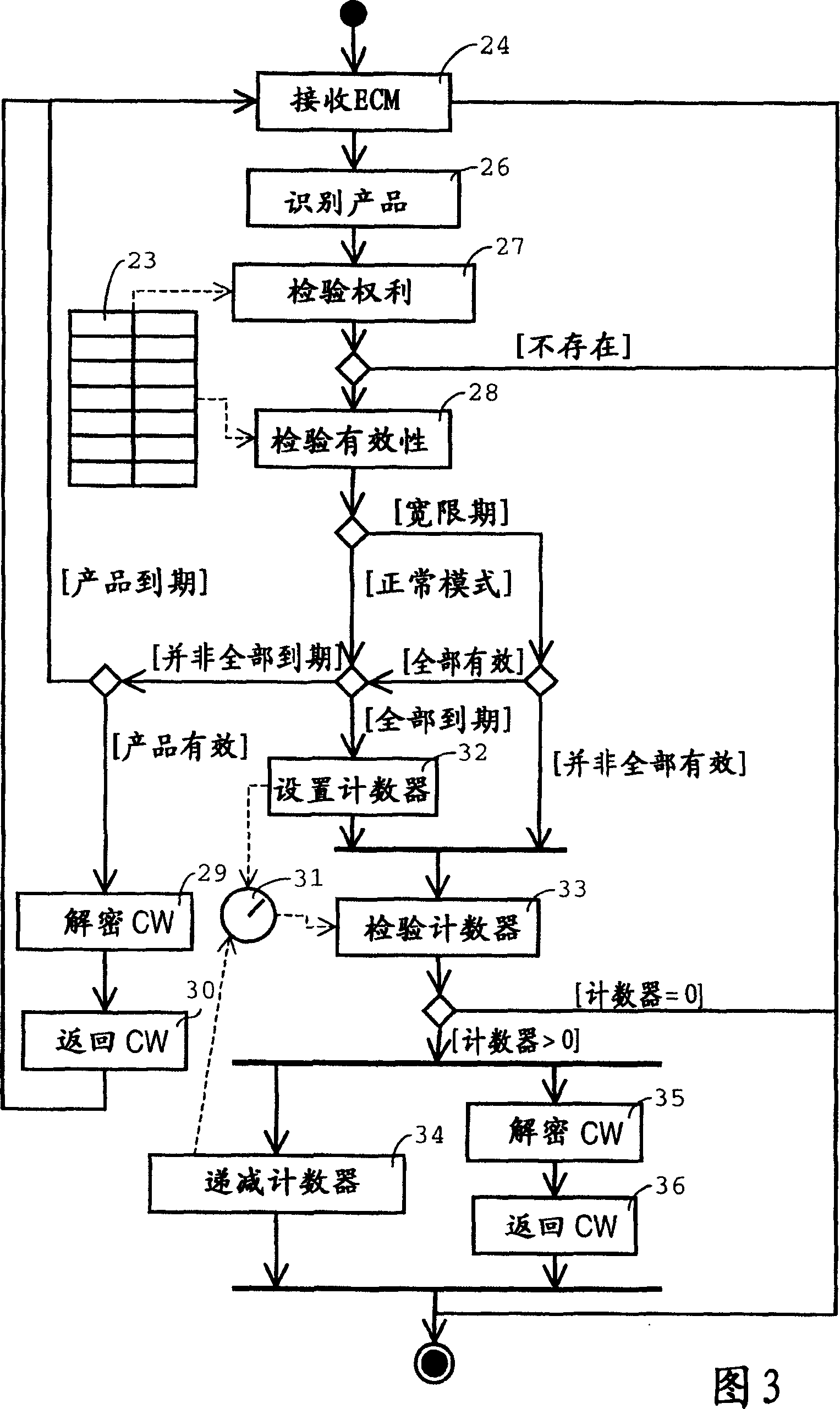
[0048] The head-end system 1 shown as an example in FIG. 1 is suitable for generating an encrypted digital data product and a right message used when decrypting the encrypted digital data product. In one embodiment, the encrypted digital data product is a file equipped with separate information implementing a digital rights management (DRM) system. Such information specifies the type of use that can be composed of encrypted data products. The file can be recorded on a data carrier such as an optical or magnetic disk. Alternatively, they can be downloaded by the receiver via a communication network including, for example, a cellular mobile telephone network, a satellite network, and / or a wired or terrestrial broadcasting network. In another embodiment, as shown in FIG. 1, the encrypted digital data product includes a set of one or more digital data streams composed of digital data packets including a header and a payload. The header contains an identification number indicating the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com