Method for realizing high-usability of network security equipment under cluster mode
A technology for network security and security equipment, which is applied in the field of high availability of network security equipment in cluster mode, can solve problems such as failure to guarantee the reliability of network security equipment, reduce the availability of network security equipment, and the failure of network card services to work normally, so as to avoid network Session Loss, High Availability, Effect of Improved Availability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
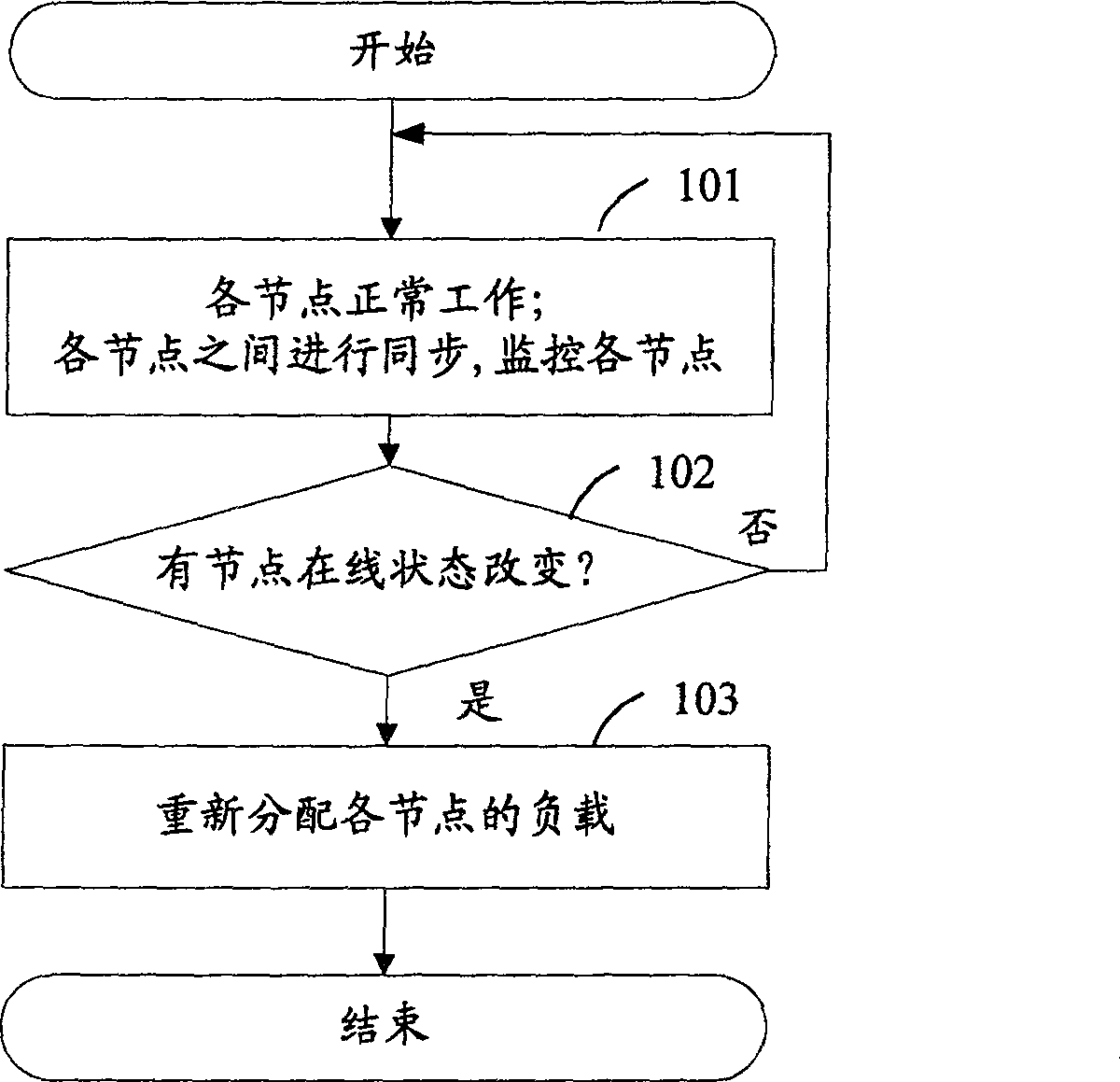
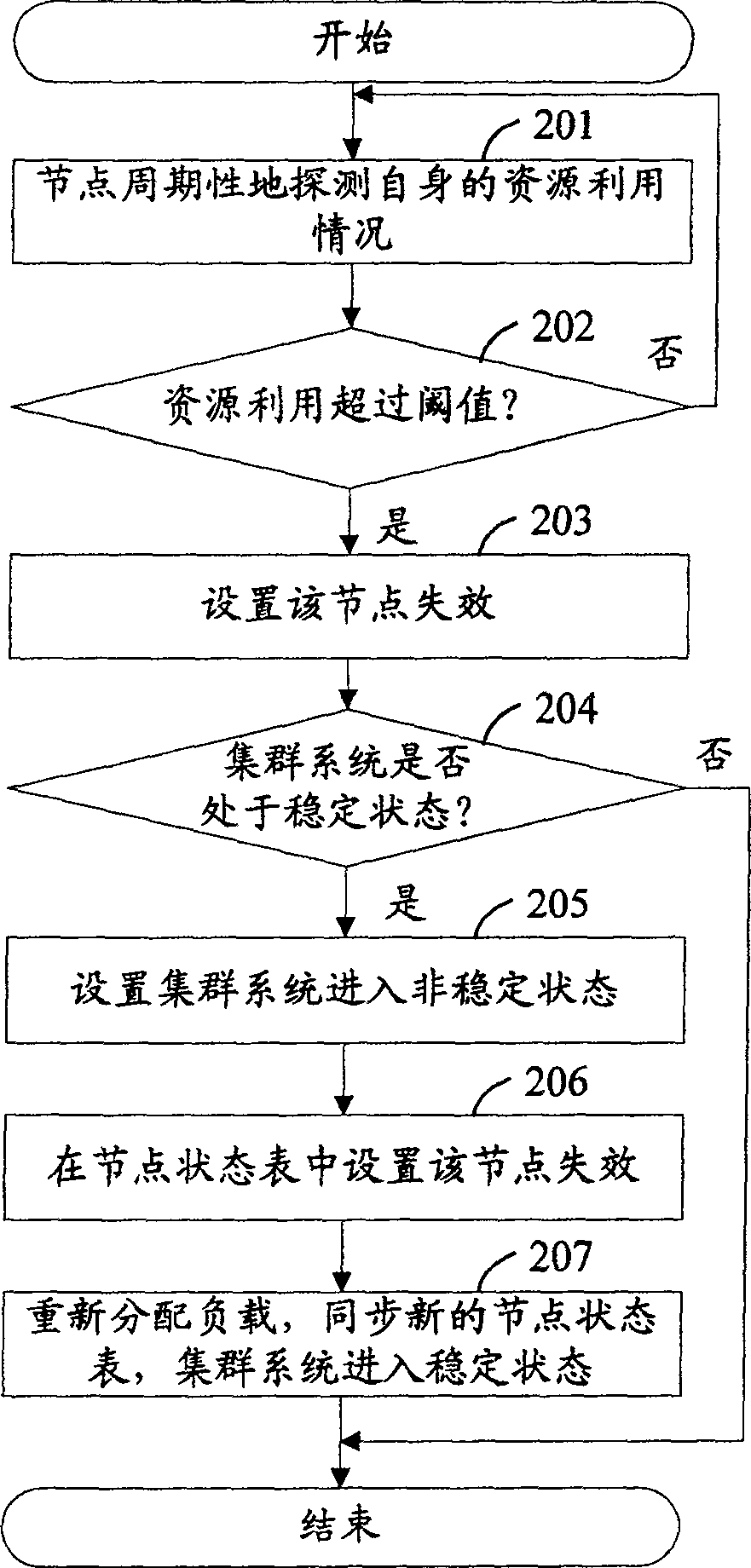
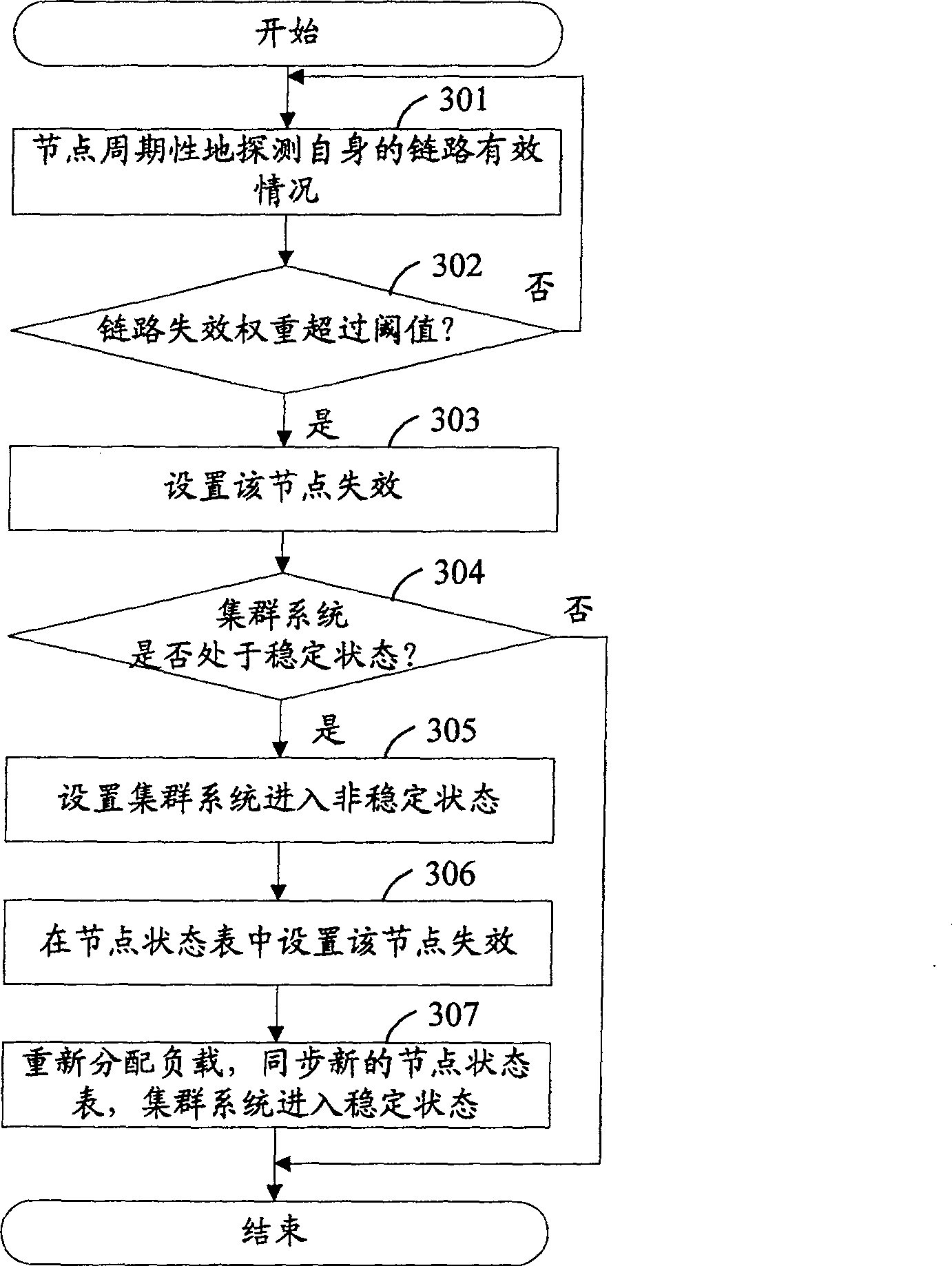
[0041] In order to make the object, technical solution and advantages of the present invention more clearly, the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
[0042] Generally, a network security device cluster system (hereinafter referred to as the cluster system) is composed of no less than one network security device node (hereinafter referred to as the node), including a master network security device node (hereinafter referred to as the master node) and no less than One slave network security device node (hereinafter referred to as slave node). In the cluster system, each node is provided with a node status table, which includes unique identifiers of all nodes in the cluster system, priority levels of all nodes, and synchronization status of all nodes. In the cluster system, each node has a priority. The master node started first has the highest priority. The priority of other nodes is...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com