Throttle Body Applications in Cybersecurity Infrastructure
JUL 18, 20259 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
Throttle Body Tech Evolution and Objectives
The concept of throttle body applications in cybersecurity infrastructure has evolved significantly over the past decade, driven by the increasing need for robust network traffic management and threat mitigation. Initially developed for automotive applications to control air intake in internal combustion engines, throttle bodies have found a new purpose in the digital realm, particularly in managing data flow and mitigating cyber threats.
The evolution of throttle body technology in cybersecurity began with the recognition that network traffic could be controlled and regulated in a manner similar to air flow in engines. Early implementations focused on basic rate limiting and traffic shaping, primarily to manage bandwidth usage and prevent network congestion. As cyber threats became more sophisticated, the objectives of throttle body applications expanded to include more advanced security functions.
One of the key milestones in this evolution was the integration of throttle body concepts with intrusion detection and prevention systems (IDS/IPS). This integration allowed for more dynamic and responsive traffic control, enabling systems to quickly throttle or block suspicious data flows in real-time. The technology progressed to incorporate machine learning algorithms, enhancing its ability to identify and respond to complex, evolving threat patterns.
Recent advancements have seen throttle body applications becoming an integral part of next-generation firewalls and software-defined networking (SDN) solutions. These modern implementations aim to provide granular control over network traffic, allowing for precise management of data flows based on a wide range of parameters, including application type, user identity, and threat intelligence.
The current objectives of throttle body applications in cybersecurity infrastructure are multifaceted. Primarily, they seek to enhance network security by providing adaptive traffic control mechanisms that can rapidly respond to emerging threats. This includes the ability to isolate compromised systems, contain the spread of malware, and mitigate the impact of distributed denial-of-service (DDoS) attacks.
Another key objective is to optimize network performance while maintaining security. Advanced throttle body systems aim to balance security measures with the need for efficient data transmission, ensuring that legitimate traffic is not unnecessarily impeded. This involves developing more sophisticated algorithms that can differentiate between normal traffic patterns and potential threats with high accuracy.
Looking forward, the future objectives of throttle body technology in cybersecurity include further integration with artificial intelligence and machine learning to create more autonomous and predictive security systems. There is also a focus on developing throttle body applications that can operate effectively in cloud and edge computing environments, addressing the unique challenges posed by distributed and decentralized network architectures.
The evolution of throttle body technology in cybersecurity began with the recognition that network traffic could be controlled and regulated in a manner similar to air flow in engines. Early implementations focused on basic rate limiting and traffic shaping, primarily to manage bandwidth usage and prevent network congestion. As cyber threats became more sophisticated, the objectives of throttle body applications expanded to include more advanced security functions.
One of the key milestones in this evolution was the integration of throttle body concepts with intrusion detection and prevention systems (IDS/IPS). This integration allowed for more dynamic and responsive traffic control, enabling systems to quickly throttle or block suspicious data flows in real-time. The technology progressed to incorporate machine learning algorithms, enhancing its ability to identify and respond to complex, evolving threat patterns.
Recent advancements have seen throttle body applications becoming an integral part of next-generation firewalls and software-defined networking (SDN) solutions. These modern implementations aim to provide granular control over network traffic, allowing for precise management of data flows based on a wide range of parameters, including application type, user identity, and threat intelligence.
The current objectives of throttle body applications in cybersecurity infrastructure are multifaceted. Primarily, they seek to enhance network security by providing adaptive traffic control mechanisms that can rapidly respond to emerging threats. This includes the ability to isolate compromised systems, contain the spread of malware, and mitigate the impact of distributed denial-of-service (DDoS) attacks.
Another key objective is to optimize network performance while maintaining security. Advanced throttle body systems aim to balance security measures with the need for efficient data transmission, ensuring that legitimate traffic is not unnecessarily impeded. This involves developing more sophisticated algorithms that can differentiate between normal traffic patterns and potential threats with high accuracy.
Looking forward, the future objectives of throttle body technology in cybersecurity include further integration with artificial intelligence and machine learning to create more autonomous and predictive security systems. There is also a focus on developing throttle body applications that can operate effectively in cloud and edge computing environments, addressing the unique challenges posed by distributed and decentralized network architectures.
Cybersecurity Market Demand Analysis
The cybersecurity market has experienced significant growth in recent years, driven by the increasing frequency and sophistication of cyber threats. As organizations across various sectors recognize the critical importance of protecting their digital assets and infrastructure, the demand for robust cybersecurity solutions continues to surge. The global cybersecurity market size was valued at $167.13 billion in 2020 and is projected to reach $372.04 billion by 2028, exhibiting a compound annual growth rate (CAGR) of 10.9% during the forecast period.
The adoption of throttle body applications in cybersecurity infrastructure is gaining traction as organizations seek more advanced and efficient methods to control and manage network traffic. This technology, originally developed for automotive applications, is now being repurposed to enhance network security by regulating data flow and mitigating potential threats. The market demand for throttle body applications in cybersecurity is driven by several factors, including the need for real-time threat detection, improved network performance, and enhanced control over data transmission.
One of the primary drivers of market demand is the increasing complexity of cyber attacks. As threat actors employ more sophisticated techniques, traditional security measures are often inadequate. Throttle body applications offer a dynamic approach to traffic management, allowing organizations to quickly respond to potential threats by adjusting data flow in real-time. This capability is particularly valuable in sectors such as finance, healthcare, and government, where data sensitivity and regulatory compliance are paramount.
The rise of cloud computing and the Internet of Things (IoT) has also contributed to the growing demand for throttle body applications in cybersecurity. As more devices and systems become interconnected, the attack surface expands, creating new vulnerabilities. Organizations are seeking solutions that can effectively manage and secure the massive amounts of data flowing through their networks. Throttle body applications provide a scalable and flexible approach to traffic management, making them well-suited for cloud and IoT environments.
Furthermore, the shift towards remote work and distributed teams has accelerated the need for robust cybersecurity solutions. With employees accessing corporate networks from various locations and devices, organizations face increased risks of data breaches and unauthorized access. Throttle body applications offer a means to control and monitor network traffic more effectively, helping to mitigate these risks and ensure secure remote operations.
As the cybersecurity landscape continues to evolve, the market demand for innovative solutions like throttle body applications is expected to grow. Organizations are increasingly recognizing the value of proactive and adaptive security measures that can keep pace with emerging threats. This trend is likely to drive further investment and development in throttle body technologies for cybersecurity applications, creating new opportunities for vendors and solution providers in the coming years.
The adoption of throttle body applications in cybersecurity infrastructure is gaining traction as organizations seek more advanced and efficient methods to control and manage network traffic. This technology, originally developed for automotive applications, is now being repurposed to enhance network security by regulating data flow and mitigating potential threats. The market demand for throttle body applications in cybersecurity is driven by several factors, including the need for real-time threat detection, improved network performance, and enhanced control over data transmission.
One of the primary drivers of market demand is the increasing complexity of cyber attacks. As threat actors employ more sophisticated techniques, traditional security measures are often inadequate. Throttle body applications offer a dynamic approach to traffic management, allowing organizations to quickly respond to potential threats by adjusting data flow in real-time. This capability is particularly valuable in sectors such as finance, healthcare, and government, where data sensitivity and regulatory compliance are paramount.
The rise of cloud computing and the Internet of Things (IoT) has also contributed to the growing demand for throttle body applications in cybersecurity. As more devices and systems become interconnected, the attack surface expands, creating new vulnerabilities. Organizations are seeking solutions that can effectively manage and secure the massive amounts of data flowing through their networks. Throttle body applications provide a scalable and flexible approach to traffic management, making them well-suited for cloud and IoT environments.
Furthermore, the shift towards remote work and distributed teams has accelerated the need for robust cybersecurity solutions. With employees accessing corporate networks from various locations and devices, organizations face increased risks of data breaches and unauthorized access. Throttle body applications offer a means to control and monitor network traffic more effectively, helping to mitigate these risks and ensure secure remote operations.
As the cybersecurity landscape continues to evolve, the market demand for innovative solutions like throttle body applications is expected to grow. Organizations are increasingly recognizing the value of proactive and adaptive security measures that can keep pace with emerging threats. This trend is likely to drive further investment and development in throttle body technologies for cybersecurity applications, creating new opportunities for vendors and solution providers in the coming years.
Current Challenges in Throttle Body Cybersecurity
The integration of throttle body technology into cybersecurity infrastructure presents several significant challenges that require careful consideration and innovative solutions. One of the primary obstacles is the inherent vulnerability of throttle bodies to cyber attacks due to their critical role in controlling data flow within networks.
Throttle bodies, originally designed for automotive applications, are now being adapted for use in digital systems to regulate network traffic. However, this adaptation process has exposed weaknesses in their security architecture. Traditional throttle bodies lack built-in encryption and authentication mechanisms, making them susceptible to unauthorized access and manipulation.
Another major challenge lies in the real-time nature of throttle body operations. In cybersecurity contexts, these devices must make split-second decisions to allow or restrict data flow, leaving little room for complex security protocols. This time-sensitive requirement often conflicts with the need for thorough security checks, creating a delicate balance between performance and protection.
The diversity of network environments in which throttle bodies are deployed further complicates their security implementation. Each network may have unique traffic patterns, threat landscapes, and compliance requirements, necessitating highly adaptable security solutions. This variability makes it difficult to develop standardized security protocols for throttle body applications across different cybersecurity infrastructures.
Scalability presents another significant hurdle. As networks grow and evolve, throttle body systems must be able to handle increasing volumes of data while maintaining robust security measures. This scalability challenge is compounded by the need to integrate throttle bodies with existing security tools and protocols, which may not always be compatible or optimized for this technology.
The rapidly evolving nature of cyber threats also poses a continuous challenge to throttle body security. New attack vectors and sophisticated malware are constantly emerging, requiring frequent updates and patches to throttle body firmware and software. This ongoing maintenance and update process can be resource-intensive and may introduce new vulnerabilities if not managed properly.
Moreover, the lack of standardization in throttle body cybersecurity applications hinders interoperability and consistent security practices across different vendors and implementations. This fragmentation in the market makes it difficult for organizations to adopt and integrate throttle body technology seamlessly into their existing cybersecurity infrastructure.
Lastly, there is a significant skills gap in the cybersecurity workforce when it comes to understanding and managing throttle body technology in network security contexts. This shortage of expertise can lead to misconfigurations, inadequate monitoring, and delayed responses to potential security incidents involving throttle body systems.
Throttle bodies, originally designed for automotive applications, are now being adapted for use in digital systems to regulate network traffic. However, this adaptation process has exposed weaknesses in their security architecture. Traditional throttle bodies lack built-in encryption and authentication mechanisms, making them susceptible to unauthorized access and manipulation.
Another major challenge lies in the real-time nature of throttle body operations. In cybersecurity contexts, these devices must make split-second decisions to allow or restrict data flow, leaving little room for complex security protocols. This time-sensitive requirement often conflicts with the need for thorough security checks, creating a delicate balance between performance and protection.
The diversity of network environments in which throttle bodies are deployed further complicates their security implementation. Each network may have unique traffic patterns, threat landscapes, and compliance requirements, necessitating highly adaptable security solutions. This variability makes it difficult to develop standardized security protocols for throttle body applications across different cybersecurity infrastructures.
Scalability presents another significant hurdle. As networks grow and evolve, throttle body systems must be able to handle increasing volumes of data while maintaining robust security measures. This scalability challenge is compounded by the need to integrate throttle bodies with existing security tools and protocols, which may not always be compatible or optimized for this technology.
The rapidly evolving nature of cyber threats also poses a continuous challenge to throttle body security. New attack vectors and sophisticated malware are constantly emerging, requiring frequent updates and patches to throttle body firmware and software. This ongoing maintenance and update process can be resource-intensive and may introduce new vulnerabilities if not managed properly.
Moreover, the lack of standardization in throttle body cybersecurity applications hinders interoperability and consistent security practices across different vendors and implementations. This fragmentation in the market makes it difficult for organizations to adopt and integrate throttle body technology seamlessly into their existing cybersecurity infrastructure.
Lastly, there is a significant skills gap in the cybersecurity workforce when it comes to understanding and managing throttle body technology in network security contexts. This shortage of expertise can lead to misconfigurations, inadequate monitoring, and delayed responses to potential security incidents involving throttle body systems.
Existing Throttle Body Security Solutions
01 Throttle body design and construction
Throttle bodies are designed with various features to improve engine performance and efficiency. These designs may include specific shapes, materials, and components to optimize airflow control and response. Some throttle bodies incorporate advanced manufacturing techniques or unique structural elements to enhance durability and functionality.- Throttle body design and structure: Throttle bodies are designed with various structural features to improve airflow control and engine performance. These designs may include specific shapes, materials, and components to optimize the throttle body's function in regulating air intake to the engine.
- Electronic throttle control systems: Modern throttle bodies often incorporate electronic control systems, including sensors and actuators, to precisely manage airflow and improve engine efficiency. These systems can integrate with the vehicle's engine control unit for more accurate and responsive throttle operation.
- Throttle body cleaning and maintenance: Various methods and devices are developed for cleaning and maintaining throttle bodies to ensure optimal performance. These may include specialized cleaning solutions, tools, or procedures to remove carbon deposits and other contaminants that can affect throttle operation.
- Throttle position sensors and feedback mechanisms: Throttle bodies often incorporate position sensors and feedback mechanisms to accurately measure and report the throttle plate's position. This information is crucial for engine management systems to optimize fuel injection and ignition timing.
- Throttle body integration with intake systems: Innovations in throttle body design focus on improving integration with intake manifolds and air intake systems. This includes optimizing airflow patterns, reducing turbulence, and enhancing overall engine breathing efficiency.
02 Electronic throttle control systems
Modern throttle bodies often incorporate electronic control systems for precise regulation of airflow. These systems may include sensors, actuators, and control modules that work together to adjust throttle position based on various engine parameters and driver input. Electronic throttle control can improve fuel efficiency, emissions control, and overall engine performance.Expand Specific Solutions03 Throttle body cleaning and maintenance
Maintaining a clean throttle body is crucial for optimal engine performance. Various methods and devices have been developed for cleaning throttle bodies, including specialized cleaning solutions, tools, and procedures. Some designs incorporate features that facilitate easier cleaning and maintenance, such as removable components or self-cleaning mechanisms.Expand Specific Solutions04 Throttle body integration with fuel injection systems
Throttle bodies are often integrated with fuel injection systems to optimize air-fuel mixture and engine performance. These integrated designs may include features such as fuel injectors mounted directly in the throttle body or specialized channels for fuel delivery. Such integration can lead to improved atomization, more precise fuel metering, and better overall engine efficiency.Expand Specific Solutions05 Throttle body airflow management
Various techniques are employed to manage and optimize airflow through the throttle body. These may include specially designed air passages, variable geometry systems, or additional valves to control airflow under different operating conditions. Some designs incorporate features to reduce turbulence, improve laminar flow, or adjust airflow characteristics based on engine speed and load.Expand Specific Solutions
Key Players in Throttle Body Cybersecurity
The cybersecurity infrastructure market for throttle body applications is in its early growth stage, characterized by rapid technological advancements and increasing adoption. The market size is expanding as organizations prioritize securing critical systems against evolving threats. While the technology is still maturing, key players like Huawei, Microsoft, and ZTE are driving innovation. Companies such as Ericsson, Intel, and IBM are also contributing to the development of more sophisticated throttle body solutions for cybersecurity infrastructure. As the technology progresses, we can expect increased competition and market consolidation, with a focus on enhancing performance, scalability, and integration capabilities.
Huawei Technologies Co., Ltd.
Technical Solution: Huawei has developed a comprehensive throttle body application for cybersecurity infrastructure, leveraging its expertise in 5G and cloud technologies. The solution incorporates AI-driven threat detection and response mechanisms, utilizing machine learning algorithms to analyze network traffic patterns and identify potential security breaches in real-time[1]. Huawei's throttle body application employs a multi-layered approach, combining network segmentation, access control, and encryption to create a robust defense against cyber attacks[3]. The system also features adaptive throttling capabilities, allowing it to dynamically adjust network resources based on threat levels and performance requirements[5].
Strengths: Strong integration with 5G networks, advanced AI capabilities, and comprehensive security features. Weaknesses: Potential geopolitical concerns and scrutiny in some markets due to the company's origin.
Microsoft Technology Licensing LLC
Technical Solution: Microsoft's throttle body application for cybersecurity infrastructure is built on its Azure cloud platform, offering a scalable and flexible solution for organizations of all sizes. The system utilizes Azure Sentinel, a cloud-native SIEM and SOAR solution, to provide intelligent security analytics across the enterprise[2]. Microsoft's approach incorporates advanced throttling mechanisms that can automatically detect and mitigate DDoS attacks, protecting critical infrastructure from overwhelming traffic[4]. The solution also integrates with Microsoft's extensive threat intelligence network, allowing for real-time updates and proactive defense against emerging threats[6].
Strengths: Extensive cloud infrastructure, strong integration with existing Microsoft products, and access to vast threat intelligence data. Weaknesses: Potential vendor lock-in and complexity for organizations not already invested in the Microsoft ecosystem.
Core Innovations in Throttle Body Protection
Background network bandwidth sharing behind gateway devices
PatentInactiveEP1904930A2
Innovation
- Implementing a method where local network clients share information about their bandwidth consumption to determine the actual usage across a shared gateway, allowing each client to adjust its background data transfer rate to prioritize other local network machines' usage, thereby reducing interference and optimizing bandwidth utilization.
Method for generating descriptive trace gaps
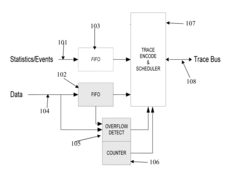
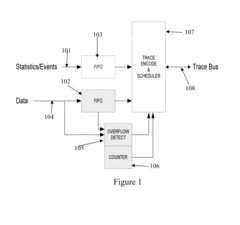
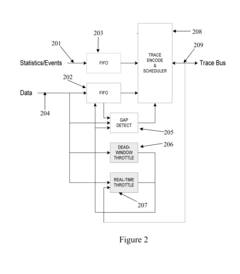
PatentActiveUS20150113336A1
Innovation
- A 10-bit encoding scheme is used to efficiently represent program counter traces, timing information, and load/store data, allowing for data gaps with accompanying count values to indicate lost data, and throttling mechanisms like Dead-Window and Real-Time Throttles to manage bandwidth, ensuring optimal bandwidth utilization and cost-effectiveness.
Regulatory Framework for Automotive Cybersecurity
The regulatory framework for automotive cybersecurity is rapidly evolving to address the increasing complexity and connectivity of modern vehicles. As throttle body applications become more integrated with cybersecurity infrastructure, regulatory bodies worldwide are developing comprehensive guidelines to ensure the safety and security of automotive systems.
In the United States, the National Highway Traffic Safety Administration (NHTSA) has taken a leading role in establishing cybersecurity standards for vehicles. The agency has published guidelines that emphasize the importance of a layered approach to cybersecurity, including the protection of critical systems such as throttle bodies. These guidelines recommend implementing security measures throughout the vehicle's lifecycle, from design and development to maintenance and decommissioning.
The European Union has introduced the UN Regulation No. 155 on Cyber Security and Cyber Security Management System, which became mandatory for all new vehicle types from July 2022. This regulation requires manufacturers to implement a Cyber Security Management System (CSMS) and obtain type approval for their vehicles. The regulation specifically addresses the need for secure communication channels and protection against unauthorized access to vehicle systems, including throttle control mechanisms.
In Asia, countries like Japan and South Korea have also been proactive in developing cybersecurity regulations for the automotive industry. The Japanese government has established guidelines that require automakers to conduct risk assessments and implement appropriate security measures for connected vehicles. Similarly, South Korea has introduced certification requirements for automotive cybersecurity systems.
International standards organizations play a crucial role in shaping the regulatory landscape. The ISO/SAE 21434 standard, developed jointly by the International Organization for Standardization (ISO) and SAE International, provides a comprehensive framework for automotive cybersecurity engineering. This standard outlines processes for identifying and mitigating cybersecurity risks throughout the vehicle's lifecycle, including those related to throttle body systems.
As the automotive industry continues to embrace advanced technologies, regulators are increasingly focusing on the cybersecurity aspects of over-the-air (OTA) updates. These updates can potentially affect throttle body performance and security, necessitating stringent regulations to ensure that OTA processes do not introduce vulnerabilities or compromise vehicle safety.
The regulatory framework also addresses the need for incident response and reporting mechanisms. Manufacturers are required to establish protocols for detecting, responding to, and reporting cybersecurity incidents that may affect vehicle systems, including throttle bodies. This approach aims to create a more resilient automotive ecosystem capable of rapidly addressing emerging threats.
In the United States, the National Highway Traffic Safety Administration (NHTSA) has taken a leading role in establishing cybersecurity standards for vehicles. The agency has published guidelines that emphasize the importance of a layered approach to cybersecurity, including the protection of critical systems such as throttle bodies. These guidelines recommend implementing security measures throughout the vehicle's lifecycle, from design and development to maintenance and decommissioning.
The European Union has introduced the UN Regulation No. 155 on Cyber Security and Cyber Security Management System, which became mandatory for all new vehicle types from July 2022. This regulation requires manufacturers to implement a Cyber Security Management System (CSMS) and obtain type approval for their vehicles. The regulation specifically addresses the need for secure communication channels and protection against unauthorized access to vehicle systems, including throttle control mechanisms.
In Asia, countries like Japan and South Korea have also been proactive in developing cybersecurity regulations for the automotive industry. The Japanese government has established guidelines that require automakers to conduct risk assessments and implement appropriate security measures for connected vehicles. Similarly, South Korea has introduced certification requirements for automotive cybersecurity systems.
International standards organizations play a crucial role in shaping the regulatory landscape. The ISO/SAE 21434 standard, developed jointly by the International Organization for Standardization (ISO) and SAE International, provides a comprehensive framework for automotive cybersecurity engineering. This standard outlines processes for identifying and mitigating cybersecurity risks throughout the vehicle's lifecycle, including those related to throttle body systems.
As the automotive industry continues to embrace advanced technologies, regulators are increasingly focusing on the cybersecurity aspects of over-the-air (OTA) updates. These updates can potentially affect throttle body performance and security, necessitating stringent regulations to ensure that OTA processes do not introduce vulnerabilities or compromise vehicle safety.
The regulatory framework also addresses the need for incident response and reporting mechanisms. Manufacturers are required to establish protocols for detecting, responding to, and reporting cybersecurity incidents that may affect vehicle systems, including throttle bodies. This approach aims to create a more resilient automotive ecosystem capable of rapidly addressing emerging threats.
Threat Modeling for Throttle Body Systems
Threat modeling for throttle body systems in cybersecurity infrastructure requires a comprehensive analysis of potential vulnerabilities and attack vectors. The process begins with identifying the system's components, including sensors, actuators, control modules, and communication interfaces. These elements form the attack surface that malicious actors may exploit.
A crucial aspect of threat modeling is understanding the data flow within the throttle body system. This includes examining how information is transmitted between components, processed, and used to control vehicle performance. Potential threats can arise at various points in this data flow, such as interception, manipulation, or injection of false data.
One significant concern is the potential for remote attacks on throttle body systems. As vehicles become increasingly connected, the risk of unauthorized access through wireless interfaces or compromised networks grows. Attackers could potentially gain control over throttle functions, leading to dangerous situations on the road.
Physical tampering is another threat vector that must be considered. Unauthorized modifications to throttle body hardware or firmware could compromise system integrity and safety. This necessitates the implementation of robust physical security measures and tamper-evident mechanisms.
The threat model should also account for insider threats, such as malicious employees or compromised supply chain partners. These actors may have privileged access to system components or sensitive information, potentially facilitating attacks or introducing vulnerabilities.
Denial of service (DoS) attacks represent another critical threat to throttle body systems. By overwhelming the system with excessive requests or disrupting communication channels, attackers could impair vehicle performance or cause system failures.
To address these threats, the threat model should incorporate defense-in-depth strategies. This includes implementing strong authentication and encryption mechanisms, securing communication protocols, and employing intrusion detection systems. Regular security audits and penetration testing should be conducted to identify and address vulnerabilities proactively.
Furthermore, the threat model should consider the potential impact of successful attacks on vehicle safety and performance. This involves assessing the consequences of various attack scenarios and developing appropriate mitigation strategies and incident response plans.
A crucial aspect of threat modeling is understanding the data flow within the throttle body system. This includes examining how information is transmitted between components, processed, and used to control vehicle performance. Potential threats can arise at various points in this data flow, such as interception, manipulation, or injection of false data.
One significant concern is the potential for remote attacks on throttle body systems. As vehicles become increasingly connected, the risk of unauthorized access through wireless interfaces or compromised networks grows. Attackers could potentially gain control over throttle functions, leading to dangerous situations on the road.
Physical tampering is another threat vector that must be considered. Unauthorized modifications to throttle body hardware or firmware could compromise system integrity and safety. This necessitates the implementation of robust physical security measures and tamper-evident mechanisms.
The threat model should also account for insider threats, such as malicious employees or compromised supply chain partners. These actors may have privileged access to system components or sensitive information, potentially facilitating attacks or introducing vulnerabilities.
Denial of service (DoS) attacks represent another critical threat to throttle body systems. By overwhelming the system with excessive requests or disrupting communication channels, attackers could impair vehicle performance or cause system failures.
To address these threats, the threat model should incorporate defense-in-depth strategies. This includes implementing strong authentication and encryption mechanisms, securing communication protocols, and employing intrusion detection systems. Regular security audits and penetration testing should be conducted to identify and address vulnerabilities proactively.
Furthermore, the threat model should consider the potential impact of successful attacks on vehicle safety and performance. This involves assessing the consequences of various attack scenarios and developing appropriate mitigation strategies and incident response plans.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!