Automated security scanning process
a security scanning and automatic technology, applied in the field of terrorist threat detection systems, can solve the problems of no human alternative that can prove efficient and effective, and achieve the effects of reducing the effects of human complacency and loss of attention to detail, empowering the human operator, and increasing the human operator's identification ability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
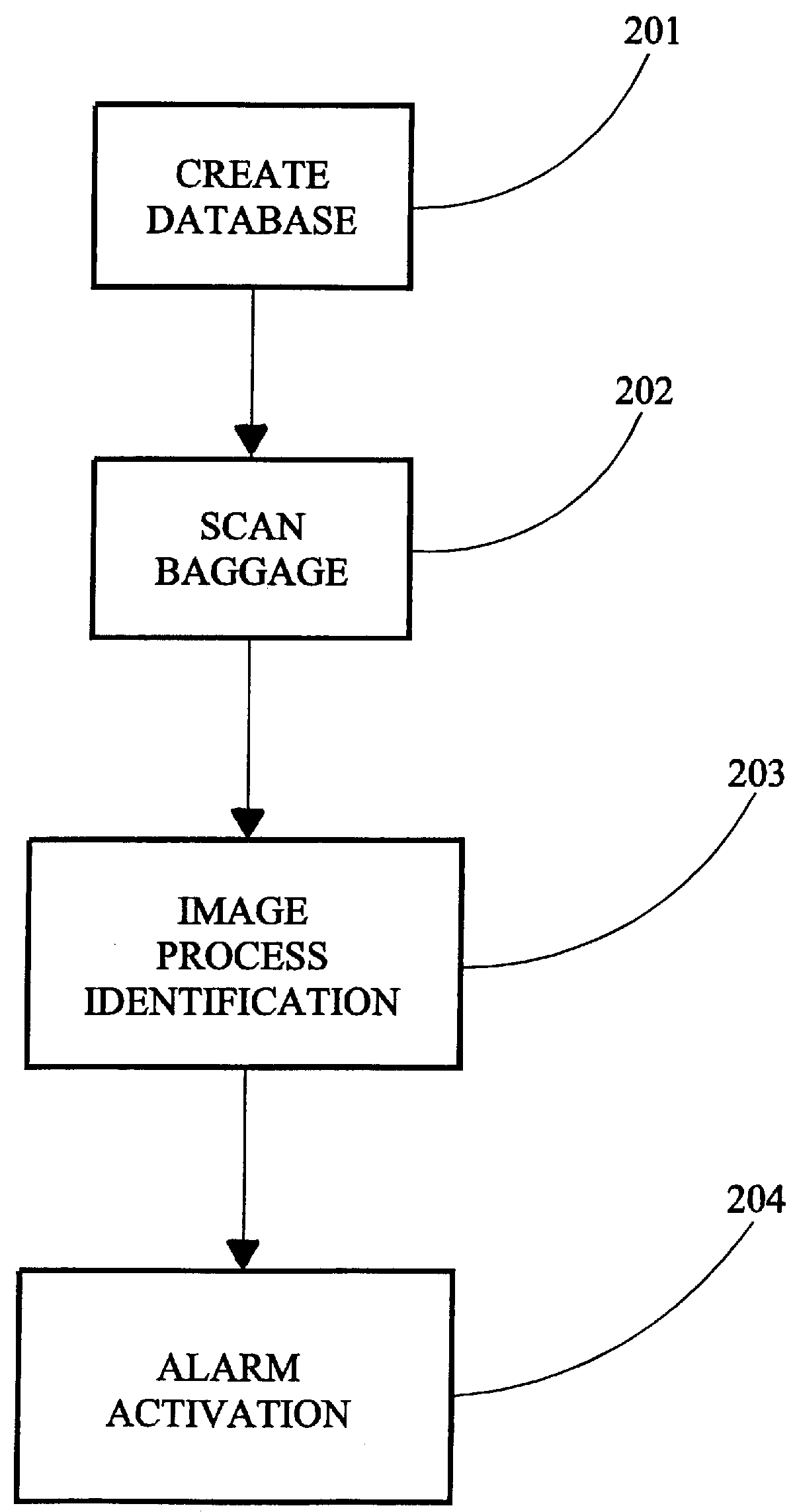
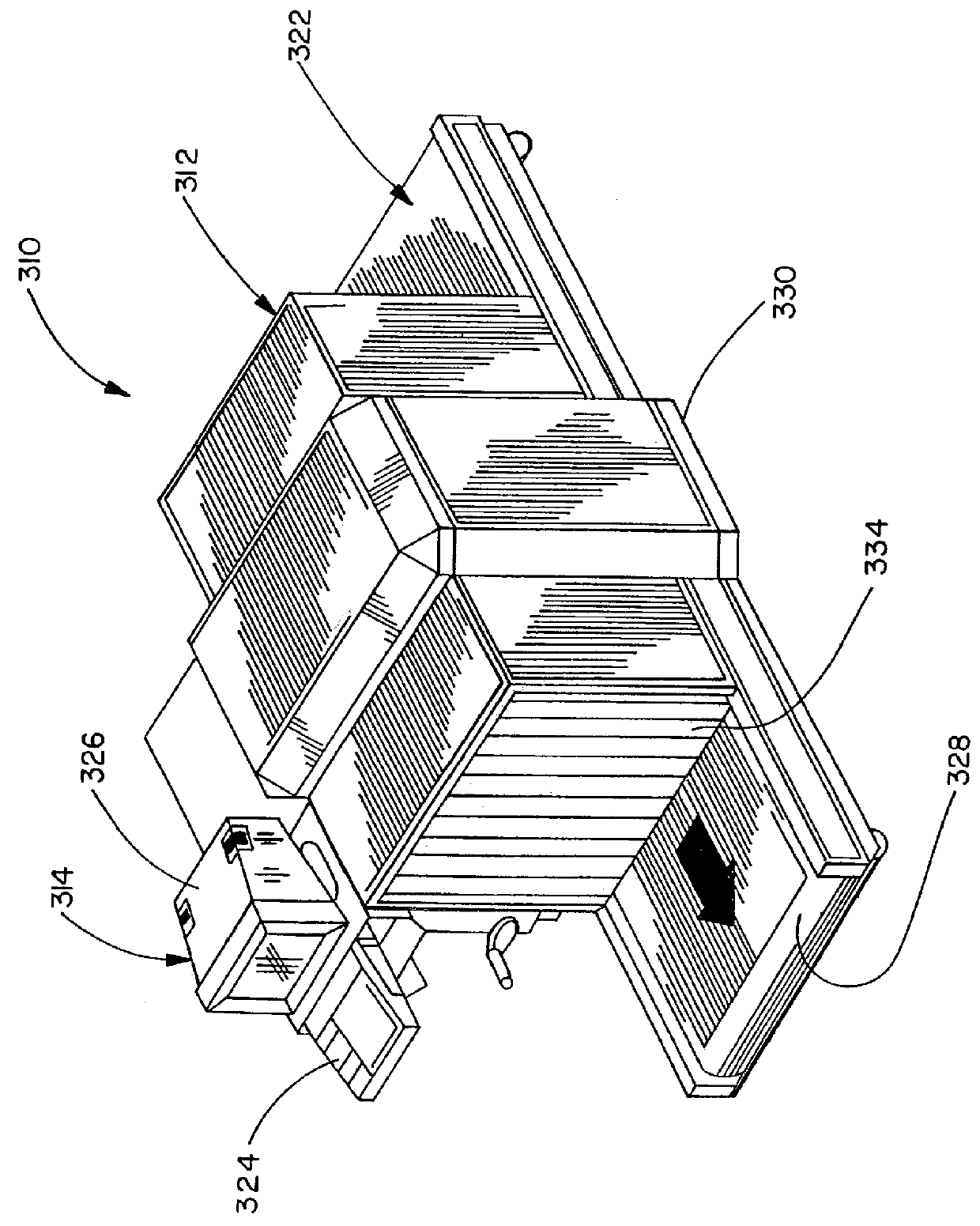
This invention automates a portion of the existing process by applying a computerized comparative assessment program to the image presented on the operator's viewing screen. This is accomplished by creating a computerized image database of all known weapons, dangerous articles, and other prohibited items. At the same time the scanned container's contents data is converted to the image presented on the operator's viewing screen, the same data is computer compared to the weapons database. Just as the human mentally compares learned weapons database against what he or she sees on the monitor, the computer accomplishes the same process, except much more timely and accurately. When the computer identifies data from the scanned image that correlates to it's prohibited items database, it alerts the security operator by any number of common means and highlights the image on the security operator's monitor.
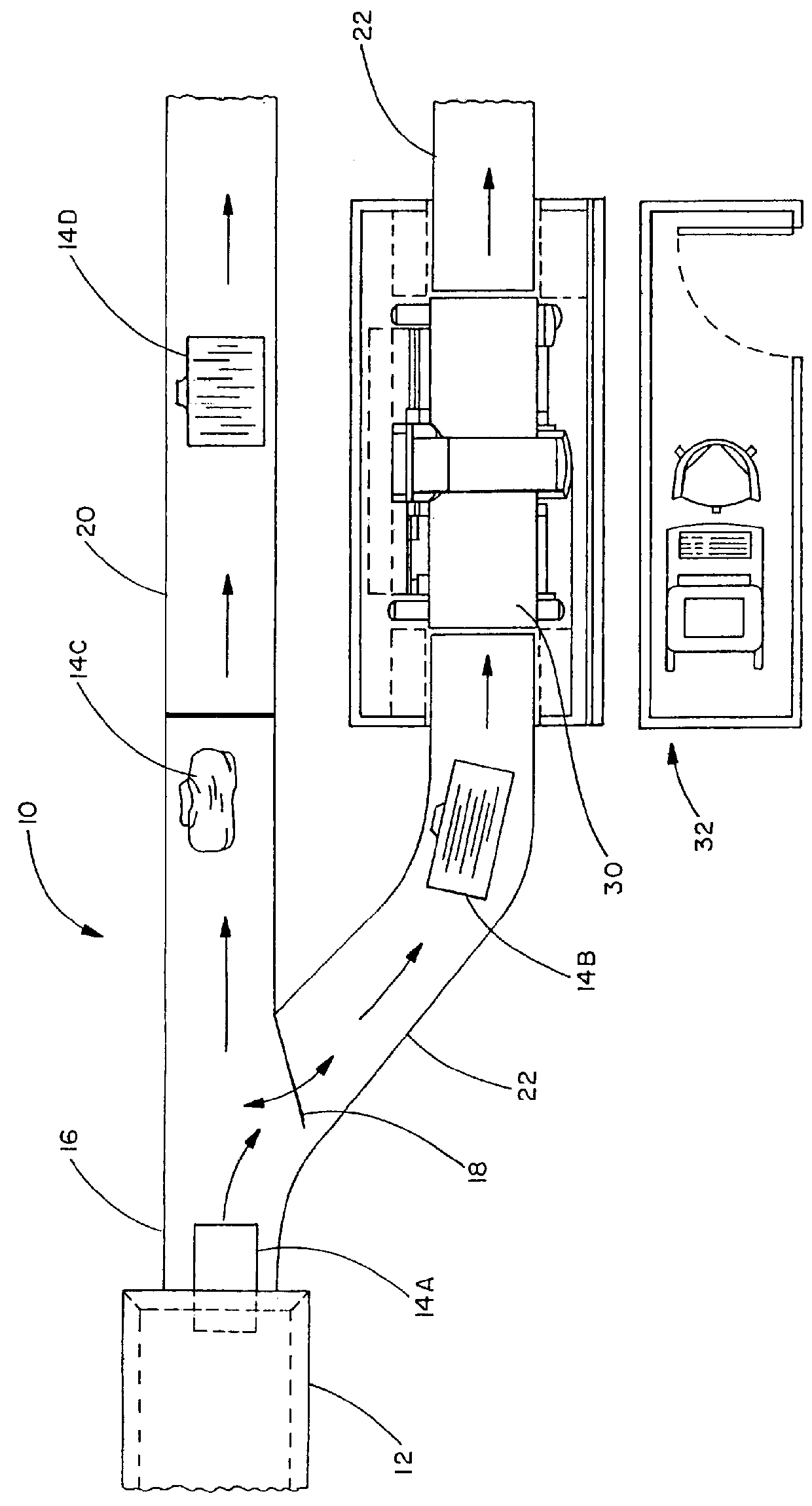
FIG. 1 is an illustration of the prior art x-ray luggage inspection system. Referring ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com