Method and system for authenticating a user by means of an application
a user and application technology, applied in the field of methods and systems for authenticating users through applications, can solve the problems of providing no guarantee of authenticity, user may have the difficulty of always carrying different cards and having them replaced,
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
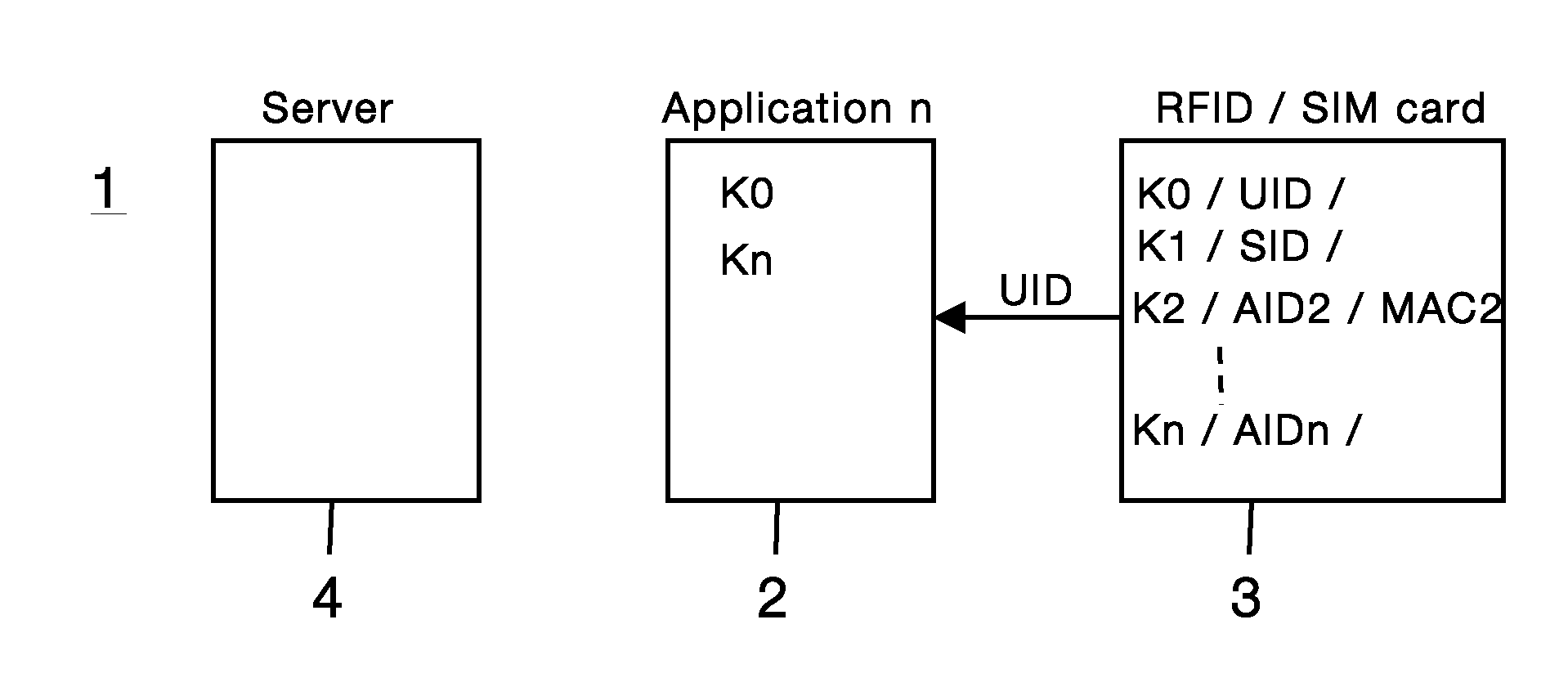
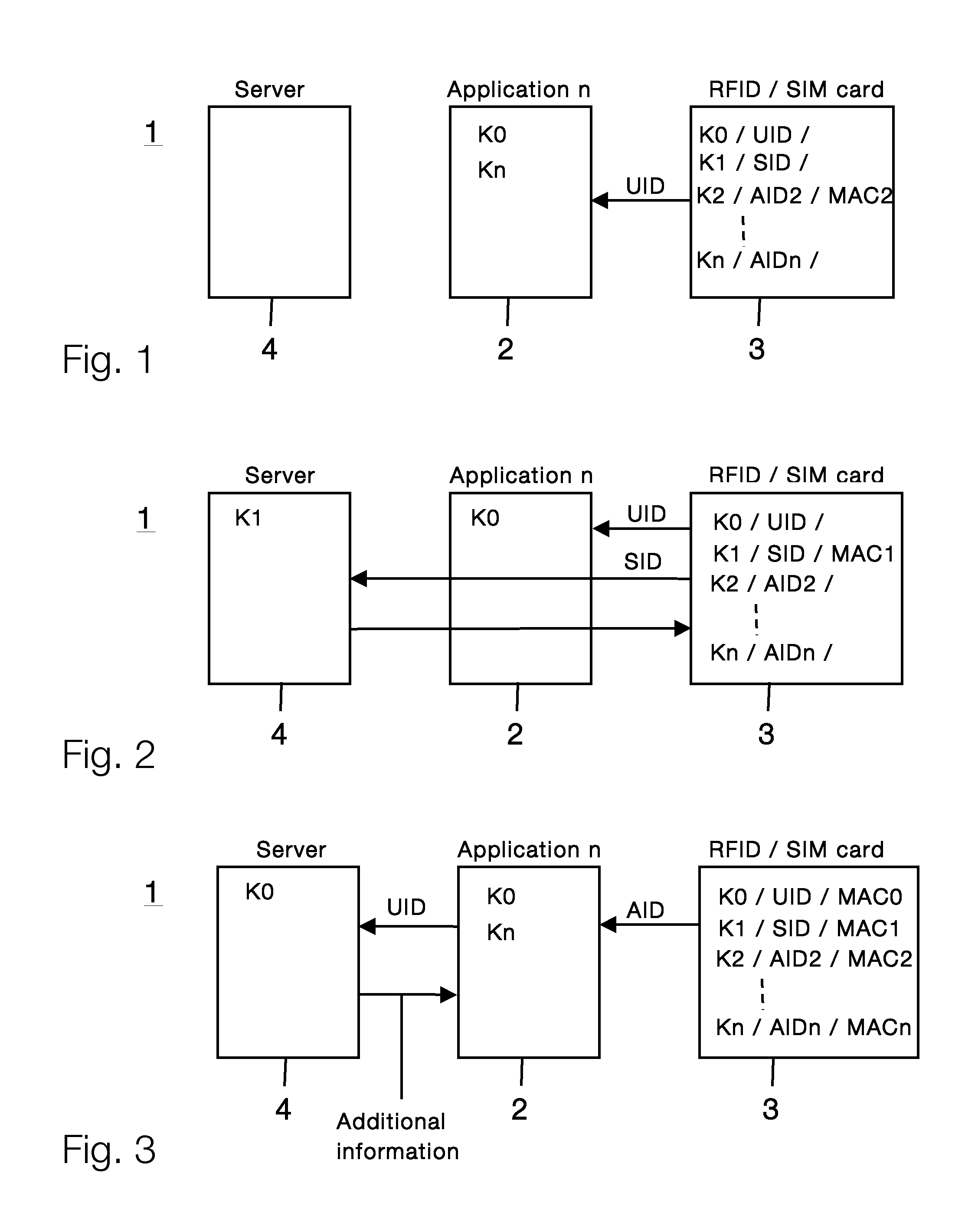
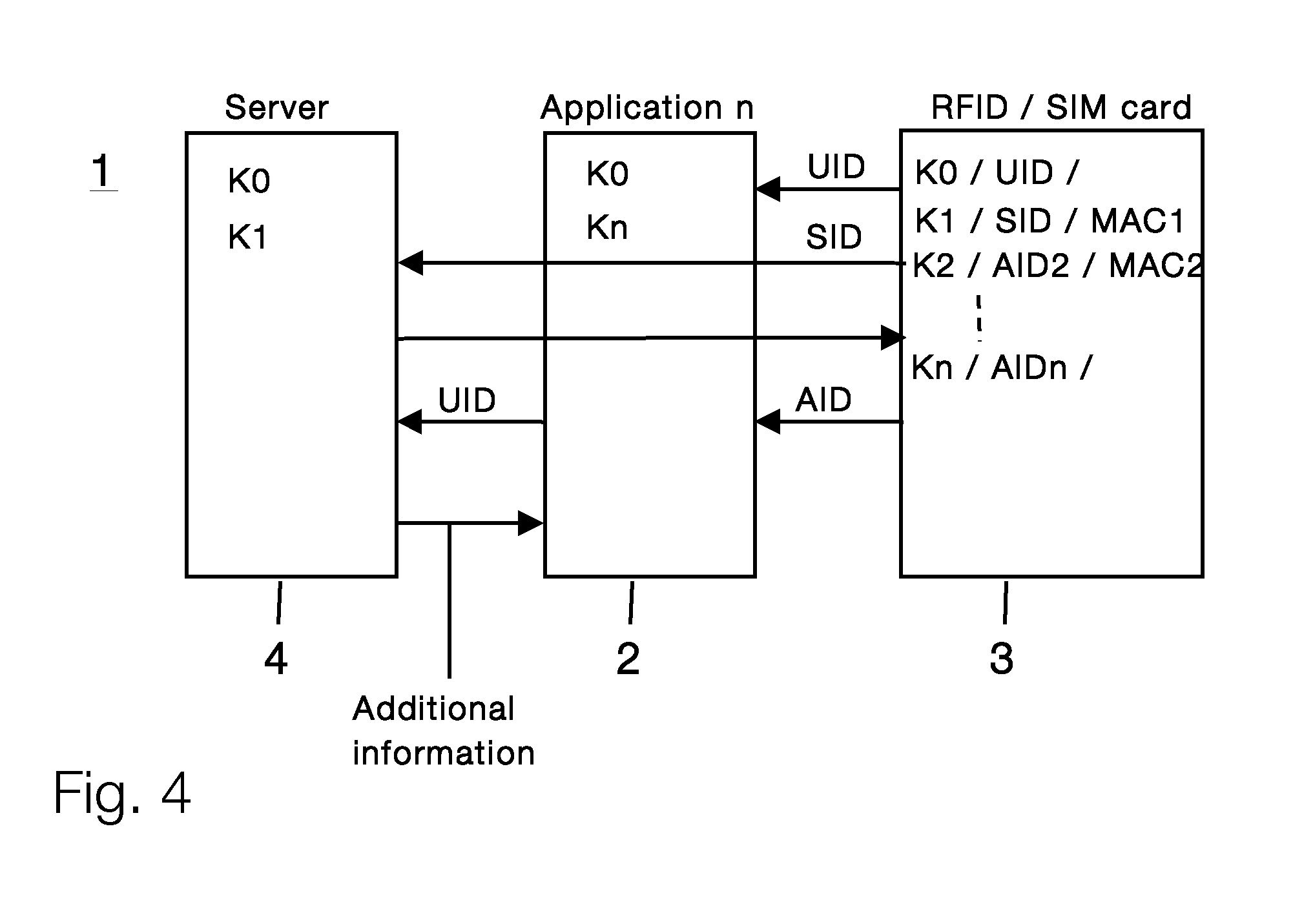
[0017]Certain embodiments of the present invention may be found in a method and system for authenticating a user using an application, as described in the following in more detail with reference to the attached figures.
[0018]As utilized herein the terms “circuits” and “circuitry” refer to physical electronic components (i.e. hardware) and any software and / or firmware (“code”) which may configure the hardware, be executed by the hardware, and or otherwise be associated with the hardware. As utilized herein, “and / or” means any one or more of the items in the list joined by “and / or”. As an example, “x and / or y” means any element of the three-element set {(x), (y), (x, y)}. As another example, “x, y, and / or z” means any element of the seven-element set {(x), (y), (z), (x, y), (x, z), (y, z), (x, y, z)}. As utilized herein, the terms “block” and “module” refer to functions than can be performed by one or more circuits. As utilized herein, the term “exemplary” means serving as a non-limit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com