Method and system for recognizing a user during a radio communication via the human body
a radio communication and human body technology, applied in the field of short-range wireless communication, can solve the problems of insecure cbb communication, risk of confidential code theft, tedious scheme,
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
first embodiment
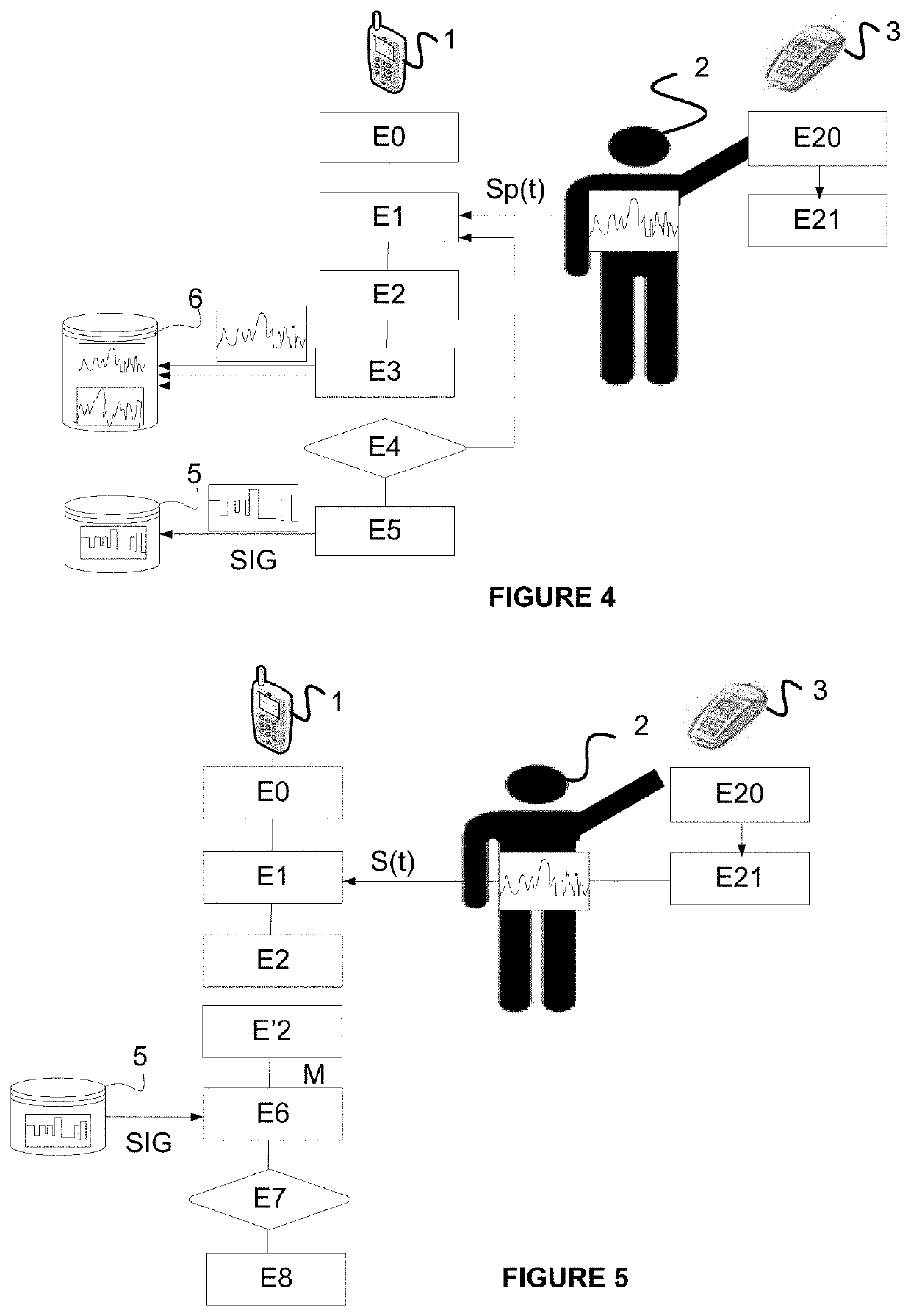
[0165]FIG. 5 represents the steps of a method for authenticating a user according to the invention.
[0166]In this embodiment, the user performs a voluntary movement in the direction of a master device (EPT) to validate a transaction, for example monetary. If the procedure succeeds, the user is authenticated, that is to say the latter is recognized as being the owner of the terminal.
[0167]It is assumed here, just as previously, that all the prerequisites necessary for the CBB communication have been performed in the course of the respective steps E0 and E20. It is also assumed that the learning phase described previously in support of FIG. 5 has been performed and that the user's characteristic imprint is on the mobile terminal (it is recalled that it could be located elsewhere, in a database external to the terminal). It is recalled that the voluntary movement (MV) is secret and corresponds to the user's signature (SIG) recorded in the base in analog, digital, or other form. The sign...
second embodiment
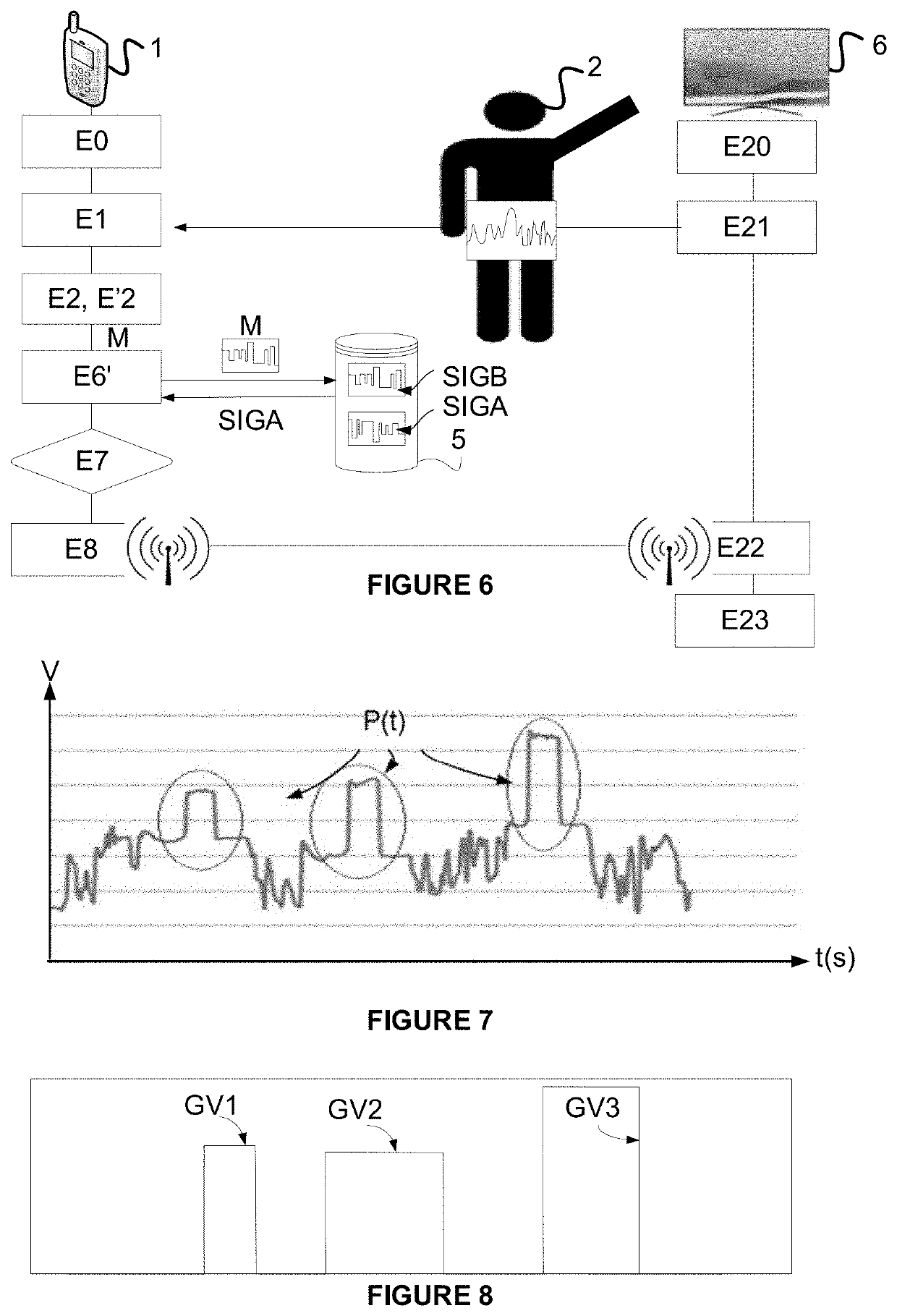
[0176]FIG. 6 represents the steps of an identification method according to the invention.
[0177]In this embodiment, the user performs a voluntary movement in the direction of a master device so as to be identified and to launch a personalized service, for example the reading of a preferred television channel. If the procedure succeeds, the user is identified, that is to say the latter is recognized as being a given user (A or B) and the corresponding service can access their profile and take appropriate action (launch channel A for A or channel B for B). For example a connected television is equipped with the master device (a CBB console) and the terminal (or the television) can access a database (or memory) comprising all the signatures of the users of the house (A, B, C, D, etc.).
[0178]It is assumed here, just as previously, that all the prerequisites necessary for the CBB communication have been performed in the course of the respective steps E0 and E20. It is also assumed that th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com