Method and system for safely accessing after-loading equipment into vehicle electronic system
A technology for secure access and electronic systems, applied in the field of information security of vehicle electronic systems, can solve problems such as poor security, failure to consider other third-party after-installation equipment usage scenarios, security threats, etc., to improve security and stability , Protect timeliness and safety, and avoid potential safety hazards
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0050] In order to make the objectives, technical solutions and advantages of the present invention clearer, the present invention will be further described in detail below with reference to the accompanying drawings.
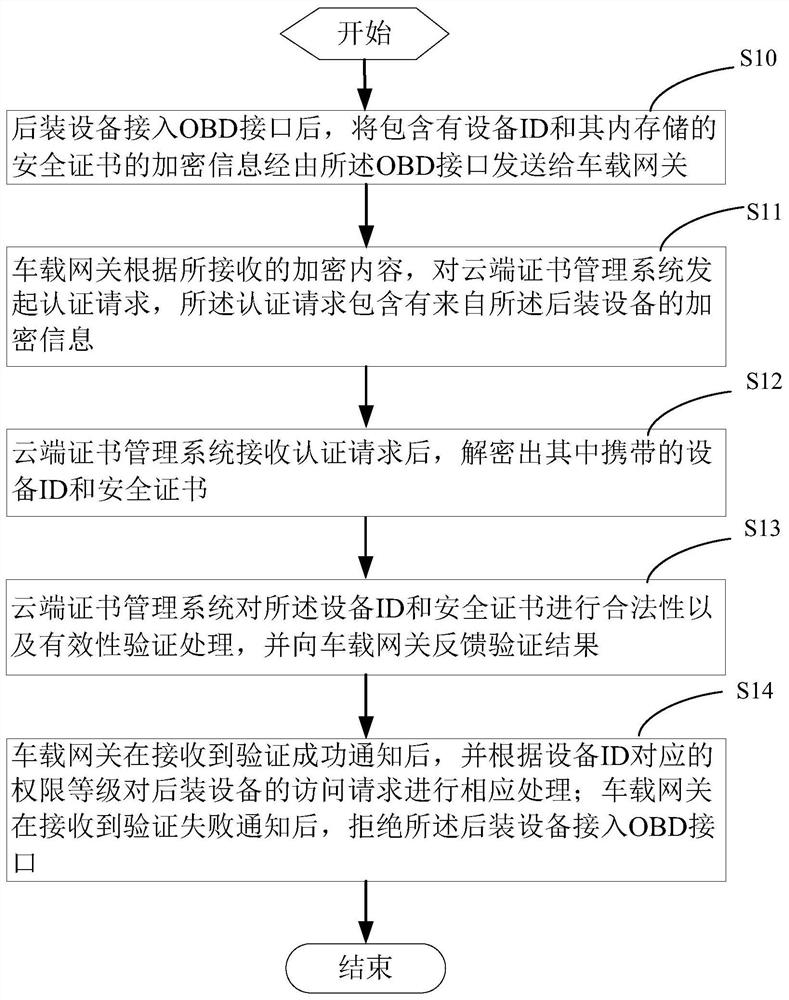
[0051] like figure 1 As shown, a schematic diagram of the main flow of an embodiment of a method for securely connecting an aftermarket device to a vehicle electronic system provided by the present invention is shown. In this embodiment, the method for safely connecting the after-installed equipment to the vehicle electronic system includes the following steps:
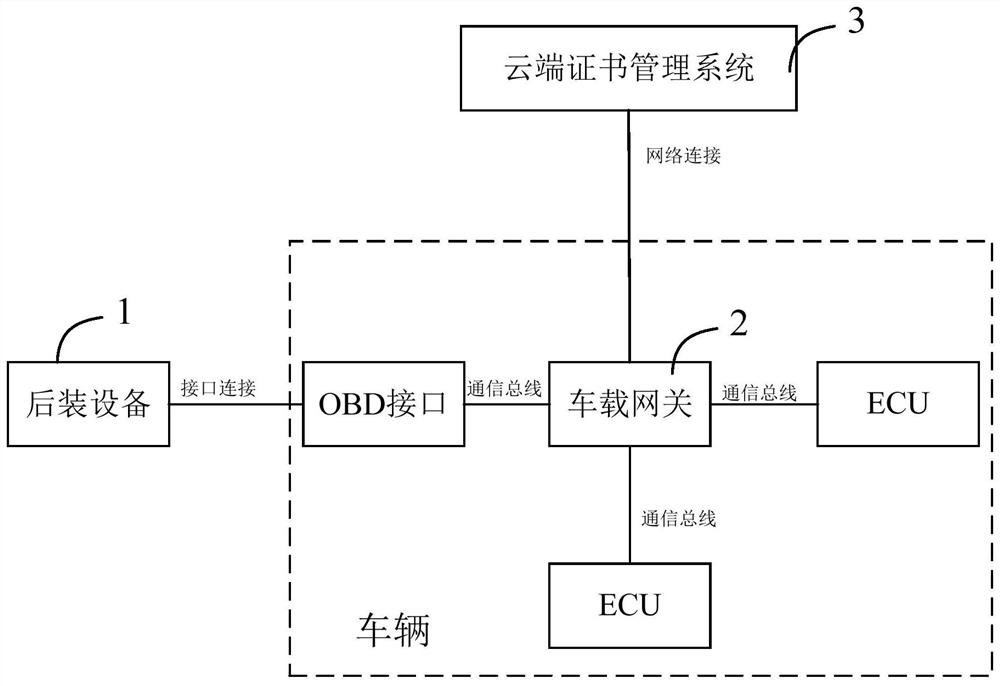
[0052] Step S10, after the post-installed device is connected to the OBD interface, the encrypted information including the device ID and its pre-stored security certificate is sent to the vehicle-mounted gateway via the OBD interface, wherein the encryption adopts a domestic cryptographic algorithm, and the OBD interface is connected to the vehicle-mounted gateway. The in-vehicle gateway establishes ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com