IoT equipment security access method and system based on RFID signal
A security access and signal technology, applied in the field of Internet of Things, can solve the problems of Wi-Fi signal fluctuation, long access time, uncontrollable, etc., to prevent malicious devices from randomly accessing the security domain, lightweight data processing, connection Controllable effect of the entry process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
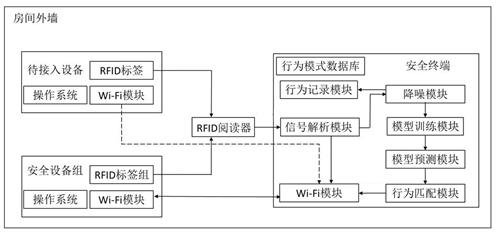
[0054] figure 1 It is a schematic diagram of the application architecture of the RFID signal-based secure access method for IoT devices provided by the present invention. Such as figure 1 As shown, the IoT device secure access method provided by the present invention mainly involves a security device group, a device to be connected, a security terminal and an RFID reader.
[0055] The basic idea of the secure access method for IoT devices based on RFID signals provided by the present invention is to train a CNN-LightGBM model that can recognize actions through changes in radio frequency signals by recording user activity habits and user-defined access actions. When the RFID signal of the device to be accessed generates a signal fluctuation of a corresponding action with a sufficiently high prediction probability at the correct time, the device to be accessed is considered to be in the room and the device to be accessed is allowed to access. Since the RFID signal will have ...
Embodiment 2
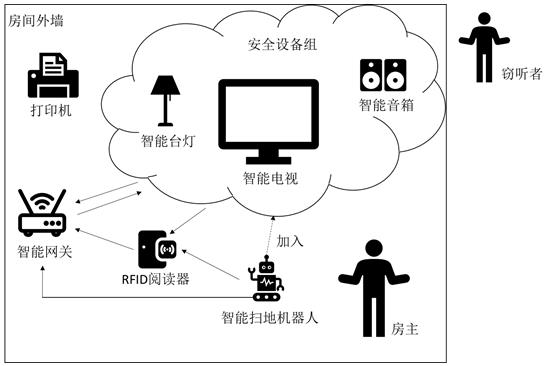
[0089] image 3 It is a schematic diagram of an application example of the RFID signal-based secure access method for IoT devices provided by the present invention. In this embodiment, the security terminal is a smart gateway that controls all IoT devices in the room. The security devices include smart TVs, smart speakers, and smart desk lamps in the room. Common devices include printers. The device to be connected is an intelligent sweeping robot. The RFID reader is an ordinary RFID reader. Among them, the smart gateway provides a Wi-Fi hotspot as the AP terminal. The original smart TV, smart speaker and smart desk lamp in the room are connected to the smart gateway through Wi-Fi. At the same time, the smart sweeping robot is brought into the room by the user as a device to be connected. Smart TVs, smart speakers, smart desk lamps and smart robot vacuums all include RFID tags. A database of user behavior patterns has been established. The CNN-LightGBM model for recognizing...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com