Equipment configuration method and equipment configuration device
A device configuration and device identification technology, applied in the information field, can solve problems such as unfavorable promotion and high operation complexity, and achieve the effect of improving user experience and simplifying user operations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
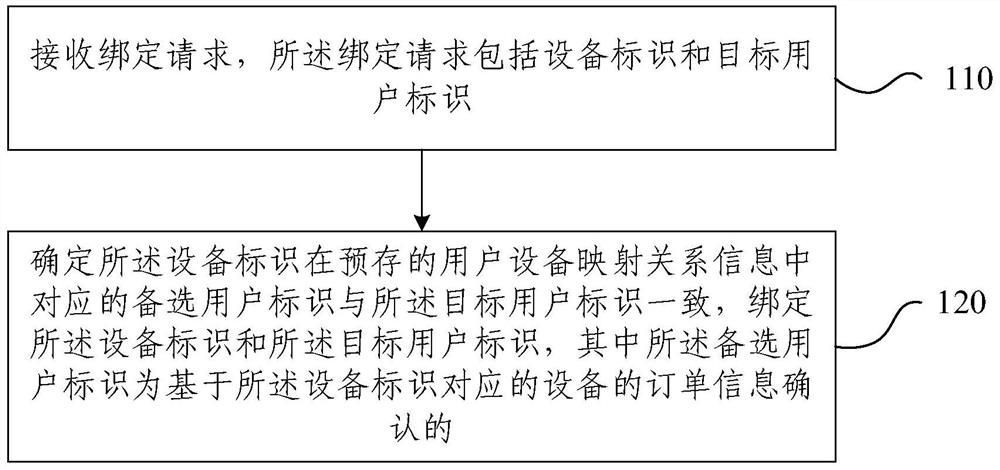
[0039] Embodiment a: receiving a first device sends binding request, the first request includes a device identifier and binding the target user ID.
[0040] In other words, the binding request sent by the device, such as a device having a data transmission module, the data transmission and the target device identification module identifies the user device transmits to the management platform. In an actual implementation, the device may have a scanning module, the scanning device can scan a two-dimensional module of the user terminal, to obtain the target user ID, and user ID and the target device identification to the device management platform; of course also be other ways initiating, including but not limited to NFC tag.
Embodiment approach 2
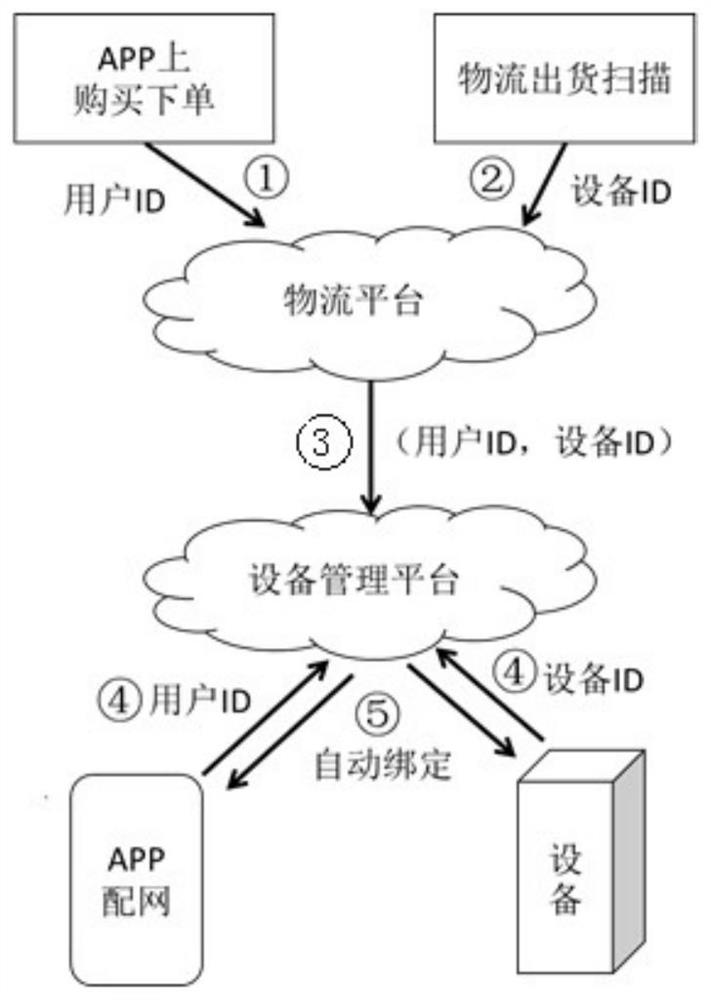
[0041] Second Embodiment: The second user terminal receiving a binding request sent by the second binding request comprises the user identifier and the target device identification.
[0042] When the terminal device of the network configuration by user, the user terminal may send a request for a second binding device management platform, the second binding request may include a user terminal identifier corresponding to the target user, the target user may be the user's account identification, phone number, email or other unique identifier, or user identification can also target multiple, the multiple target user ID making up the group, according to the different scenarios, the group can be a family group, company or group custom Groups like. In practical execution, the user terminal may have a scanning module, the scanning module of the user terminal device can scan the QR code to obtain the device identifier and the target identifier and the user equipment identifier to the facil...
Embodiment approach 3
[0043] Embodiment three: a first binding request sent by the receiving device, comprising a first target binding request includes a device identifier and the target UE identifier, and the second binding receiving a request sent by the user terminal, the second binding request user identifier and the device identifier.
[0044] In practical execution, the user terminal may have a scanning module, the scanning module of the user terminal device can scan the QR code to obtain the device identifier and the target identifier and the user equipment identifier to the facilities management platform; of course also be other ways initiating, including but not limited to NFC tag. The user terminal will be sent to the target user identification device, the device also sends the target user identity and device identification to device management platform.
[0045] In other words, when initiating binding request and the user terminal equipment are sent bind request, the device management platfo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com