A method, protection system, and storage medium for protecting identity privacy in the Internet of Vehicles
A car networking and identity technology, applied in the field of car networking, can solve problems such as exposure of user identity, theft verification attack, system security impact, etc., to solve risks and excessive calculation volume, reduce the risk of leakage, and reduce the workload of encryption Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033]The following describes in detail the embodiments of the present invention, examples of which are illustrated in the accompanying drawings, wherein the same or similar reference numerals refer to the same or similar elements or elements having the same or similar functions throughout. The embodiments described below with reference to the accompanying drawings are exemplary and are only used to explain the present invention, and should not be construed as a limitation of the present invention.
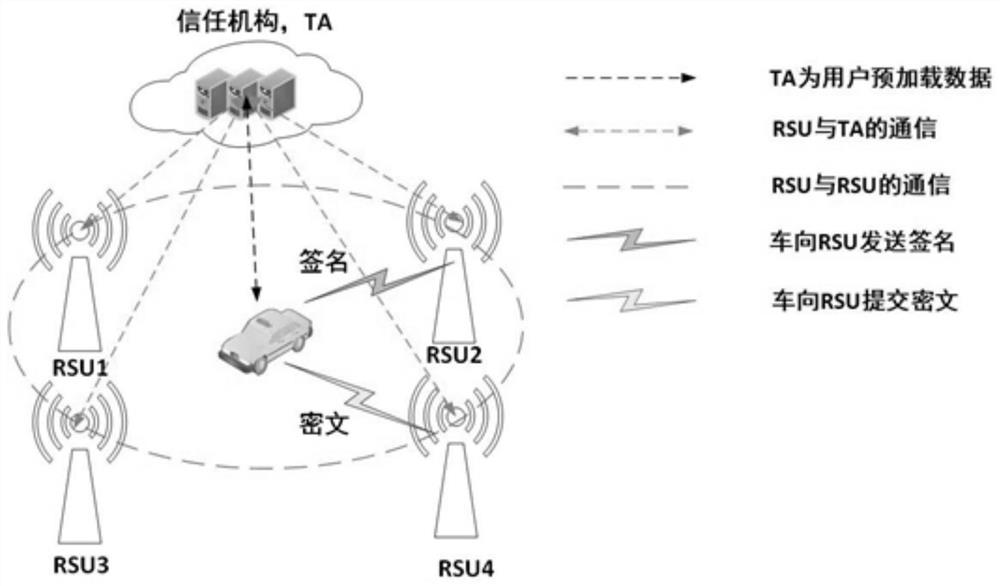
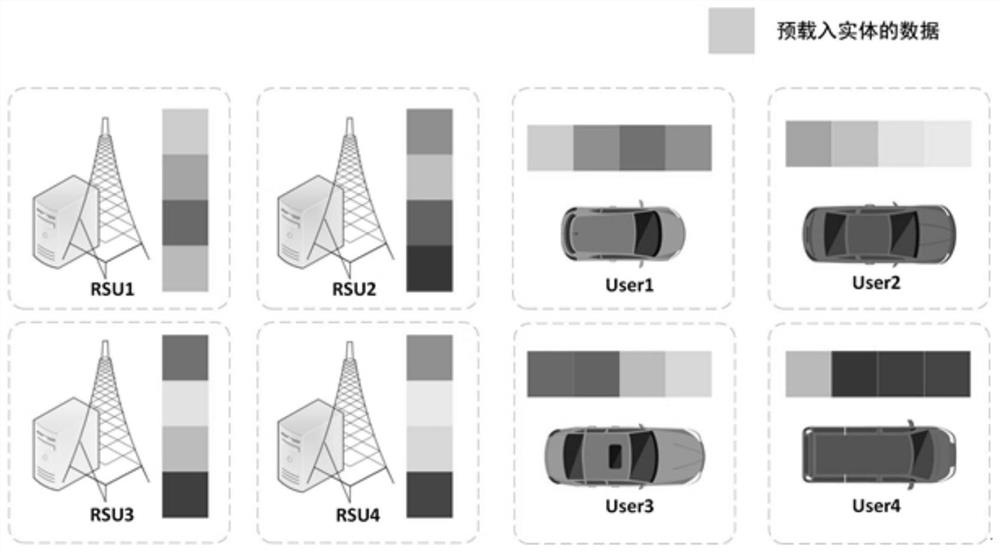
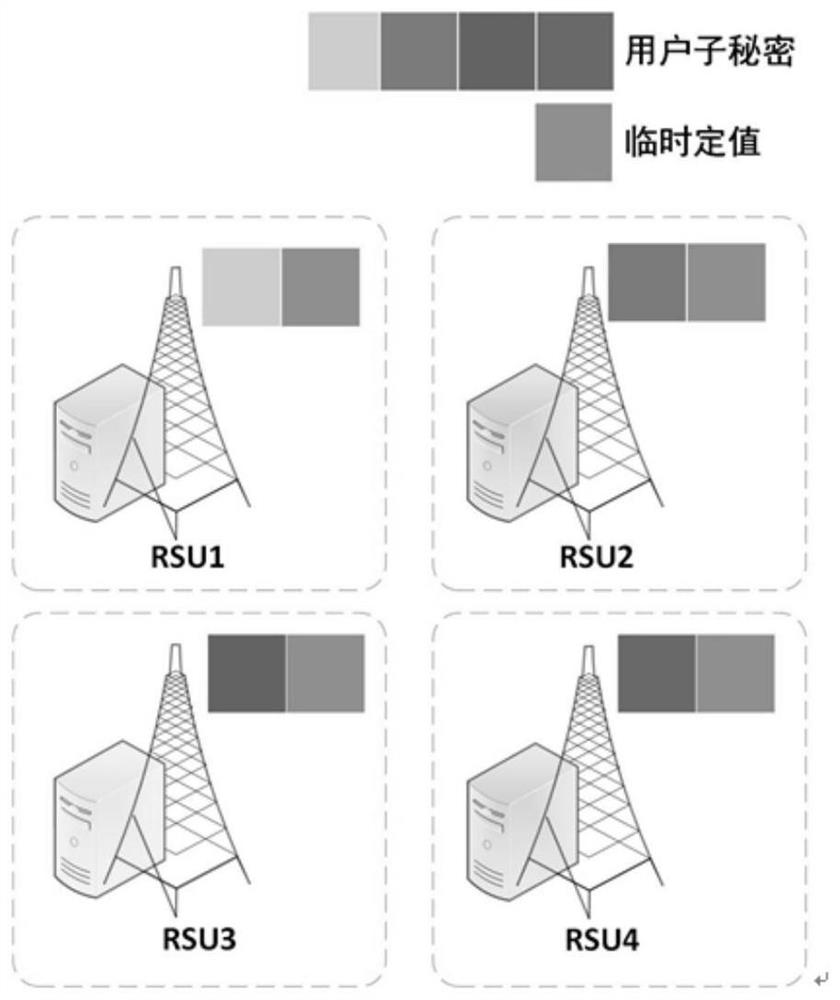
[0034] In the existing framework, the solutions are based on the assumption that the vehicle OBU is absolutely safe. If an OBU is breached, the security of the entire system will be threatened. In addition, there is also a scheme to store all vehicle data mapping pairs in the network in the RSU, but a single RSU may be attacked by theft verifier and leak the data stored in it, then the attacker can forge any vehicle.
[0035] In view of the above problems, in order to prevent a si...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com