A blockchain-based concealed information transmission system and method
A technology of concealing information and transmission methods, applied in the field of concealed channel construction, which can solve problems such as poor security and large amount of data hiding, and achieve the effect of optimizing communication efficiency and economic benefits
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
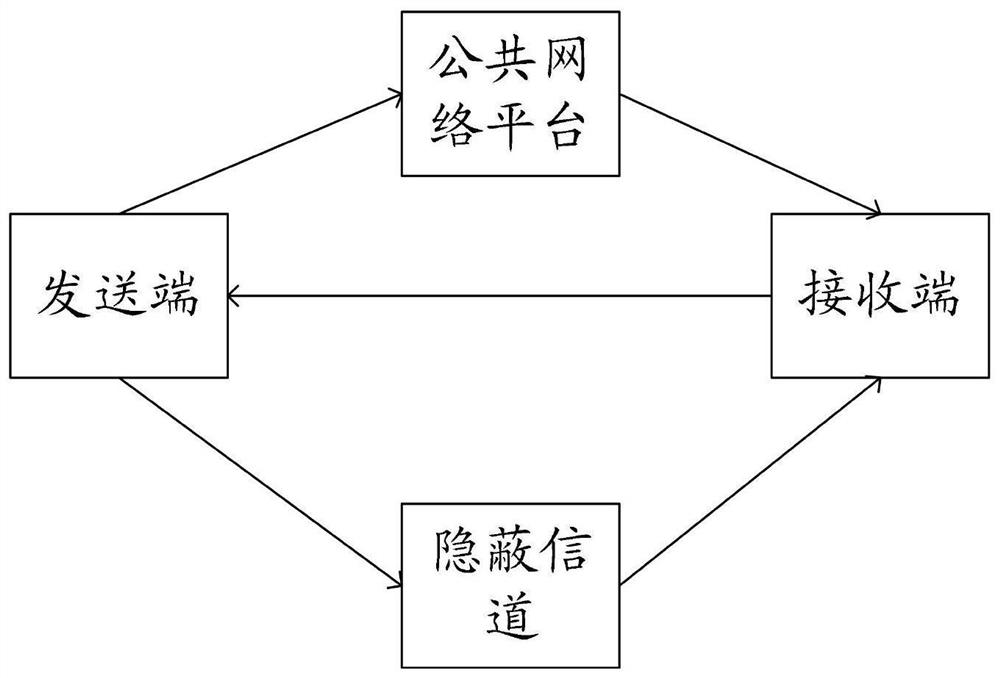
[0052] On the one hand, as attached figure 1 As shown, the embodiment of the present invention discloses a block chain-based covert information transmission system, including: a sending end, a covert channel, a receiving end, and a public network platform;
[0053] Wherein, the transmitting end is respectively connected with the covert channel and the public network platform; the receiving end is respectively connected with the covert channel and the public network platform.
[0054] In a specific embodiment, the covert channel is a covert communication channel on the blockchain, and the public network platform is a public network platform under the blockchain.
[0055] On the other hand, an embodiment of the present invention discloses a block chain-based covert information transmission method, which is characterized by comprising:
[0056] The sender obtains hidden information;
[0057] The sender obtains the steganographic image according to the hidden information;
[00...
Embodiment 2
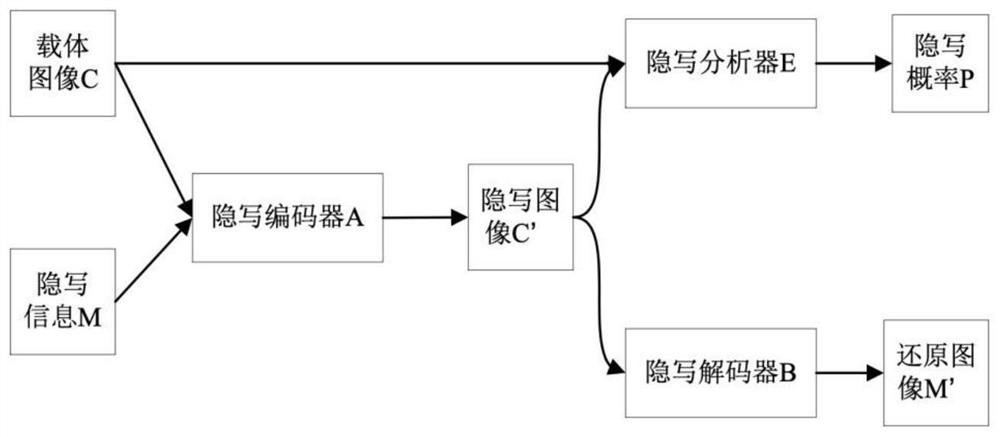
[0090] as attached figure 2 , is a schematic diagram of the image steganography model structure of generative adversarial network, A, B, E represent steganographic encoder, steganographic decoder, steganalyzer respectively, M represents hidden information, C represents carrier image, C' represents Steganographic image, M' represents the restored image, P steganographic probability.
[0091] Among them, the carrier image C and the hidden information M are input to the steganographic encoder A to obtain the steganographic image C', and the steganographic image C' is respectively sent to the steganographic decoder B and the steganographic analyzer E, and the steganographic analyzer E The steganographic probability P is output according to the carrier image C and the steganographic image C', and the steganographic decoder B obtains the restored image M' according to the steganographic image C'.
[0092] The specific working principle is as follows: the task of the steganographic...
Embodiment 3
[0095] The information sending end and the information receiving section can pre-determine the rule R of image steganography, the parameter set P of the covert channel of the blockchain network, the image steganography module S, and the image hash algorithm family is {Hash_1, Hash_2, ...}.
[0096] Suppose the information to be transmitted by the sender is M, and the serial number of the information is n (the nth message
[0097] Then, the specific steps of the sender are:
[0098] 1. The sender randomly selects a carrier image F from a certain public network u, and generates a steganographic image FS=S(F, M, R) through the steganographic module;
[0099] 2. Publish the carrier image and steganographic image through a public network platform;
[0100] 3. Randomly select the i-th hash function to calculate Hashi (FS) to obtain the image hash Hs of the steganographic image, send (n, HS, i, u) through the covert channel on the blockchain chain, and wait for the receiving end to co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com