Method and device for reducing network security scanning rule set
A network security and rule-based technology, applied in the information field, can solve problems such as low sequential matching and pattern matching performance, high complexity of malicious code detection rules, and limited portability of detection engines.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
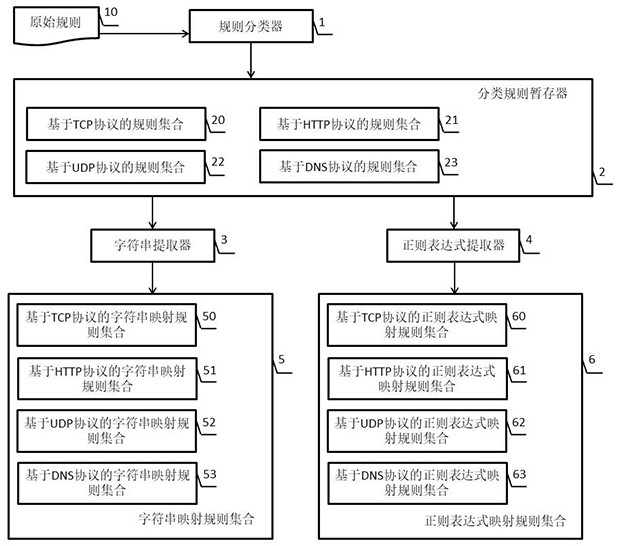
[0055] see figure 1 , the reduction device of the network security scanning rule set provided by the present invention is composed of a rule classifier 1, a classification rule temporary store 2, a character string extractor 3, a regular expression extractor 4, a character string mapping rule set 5 and a regular expression The mapping rule set consists of 6;
[0056] Rule classifier 1 reads the original rule set, which is a standard specification document for network message analysis and detection written according to the MTX rules;
[0057] The rule classifier 1 classifies the rules according to the protocol according to the protocol type field of each rule in the original rule set to form a rule set 20 based on the TCP protocol, a rule set 21 based on the HTTP protocol, a rule set 22 based on the UDP protocol, and a rule set based on the DNS protocol. The rule set 23 of the protocol, each rule set is stored in the classification rule temporary register 2, and there is the f...
Embodiment 2
[0071] When scanning network protocols:
[0072] 1. First read the string mapping rule set 5 and the regular expression mapping rule set 6 into the computer memory;
[0073] 2. According to the type of the network protocol being scanned, select the subset of the string mapping rule set 5 and the subset of the regular expression mapping rule set 6 participating in the scan, and complete the operation of narrowing the calculation range for the first time;
[0074] 3. Extract the string of the scanned network protocol by the character string extractor 3. When the string of the scanned network protocol has a mapped rule number in the subset of the string mapping rule set 5, the output rule number is a character String detailed comparison number set, the rule number in the string detailed comparison number set is the rule number for determining the participating and scanned network protocols for detailed comparison, and completes the second operation of narrowing the calculation ra...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com