Method and tool for realizing password dynamic loading based on sidecar mode
A dynamic loading and password technology, applied in the field of kubernetes clusters, can solve problems such as increasing the workload of operation and maintenance personnel, manually managing password keys, and leaking password keys, so as to reduce the probability of manual configuration errors, improve security and ease of use. Usability and the effect of avoiding configuration redundancy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
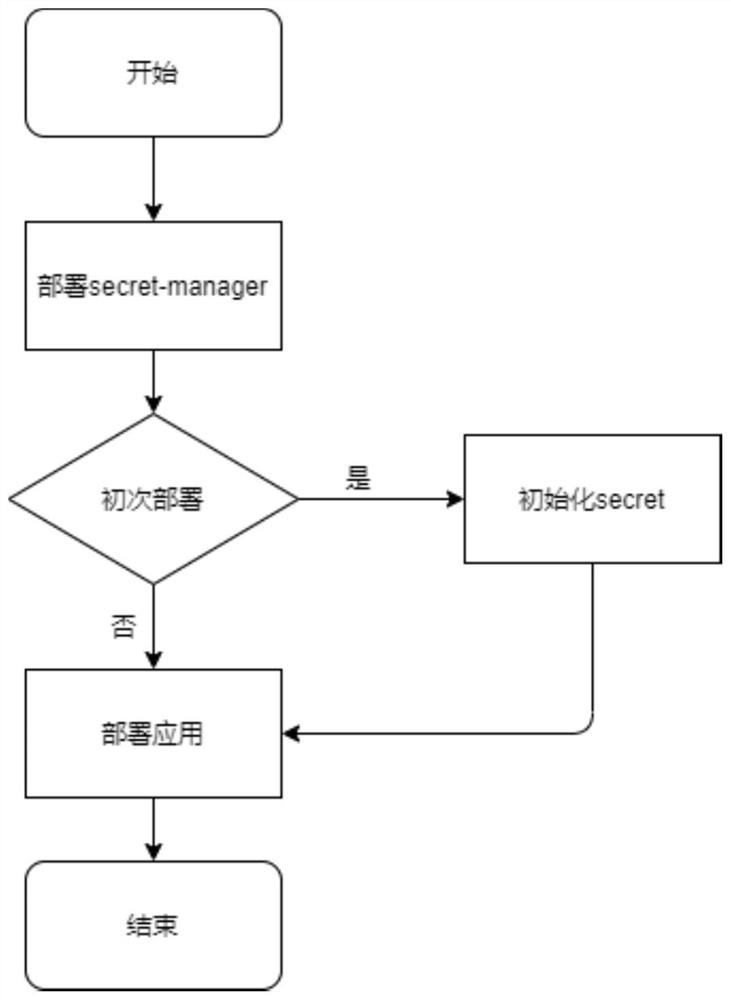
[0034] This embodiment proposes a method for implementing dynamic loading of passwords based on the sidecar mode, and the implementation process includes:
[0035] Step S1. Pre-configure the content that needs to generate the password key in Secret-manager. When deploying the kubernetes cluster, generate all the passwords required by the kubernetes cluster through the pre-configured content in Secret-manager, and store them in the pre-specified password storage after encryption Under contents.
[0036] In this step, when deploying a kubernetes cluster, all passwords generated by Secret-manager are stored in a structure similar to a file directory.
[0037] Secret-manager generates all the passwords required by the kubernetes cluster according to the pre-configured content, and provides the generated passwords to corresponding password usage services, such as mysql.
[0038] A series of policies are defined in Secret-manager. Each policy can pre-specify multiple password stora...
Embodiment 2
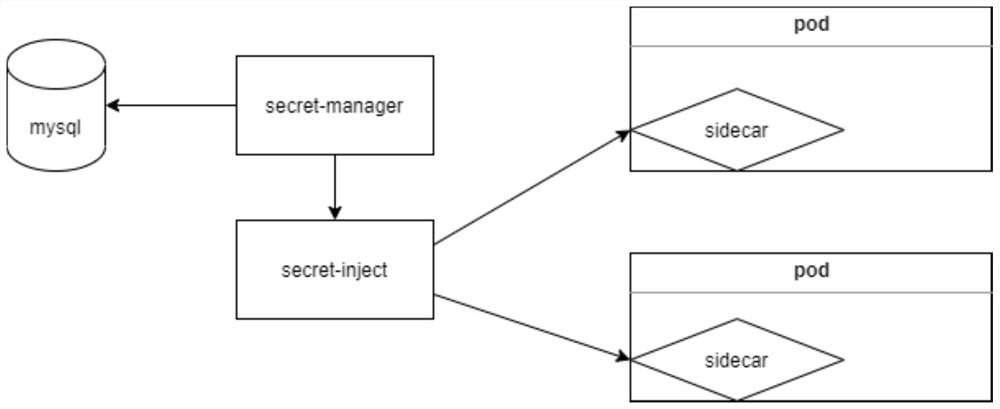
[0045] combined with figure 1 , 2, this embodiment proposes a tool for dynamically loading passwords based on the sidecar mode, based on a kubernetes cluster, and its implementation framework includes secret-manager and secret-inject, wherein the Secret-manager is pre-configured with content that needs to generate a password key,
[0046] secret-inject is used to inject Secret-manager into the application pod in sidecar mode, and mount it to the pre-specified directory of the application pod.
[0047] When deploying a kubernetes cluster:
[0048] (1) First, generate all passwords required by the kubernetes cluster based on the pre-configured content in Secret-manager, and store them in the pre-specified password storage directory after encryption.
[0049] At this point, Secret-manager generates all the passwords required by the kubernetes cluster according to the pre-configured content, and provides the generated passwords to the corresponding password usage services, such ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com